HOME
SCRIPTS
PROJECTS
READING
CV

Please donate if you find SSH Canary (sshcanary) useful.
BTC: 1GwYToq2AuUWUfJJ7NeCpksfjMth7bw7TuLTC: LKh99yzPeXZ7jQgvGgRhkTGReN4TRK4C6p
SSH Canary (sshcanary) can be found on GitHub.
You can clone the repository directly from github:
| % git clone https:/github.com/rondilley/sshcanary.git |
Or you can download the current distribution tarball: sshcanary v0.6
What is sshcanaryd?
SSH Canary is a ver low interaction honeypot specifically designed to gather information about potential attackers that attemp to brute-force into a system using SSH.Why use it?
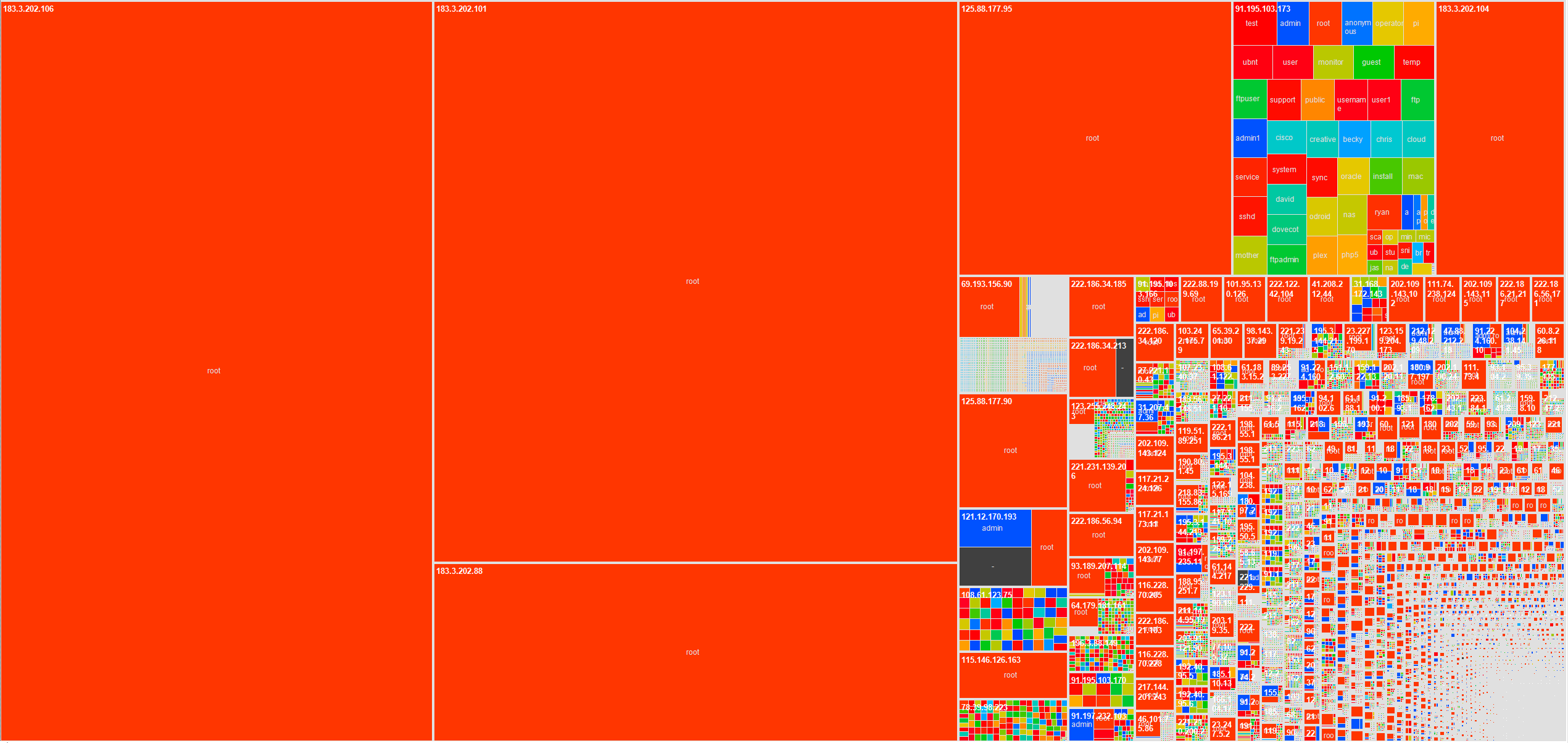
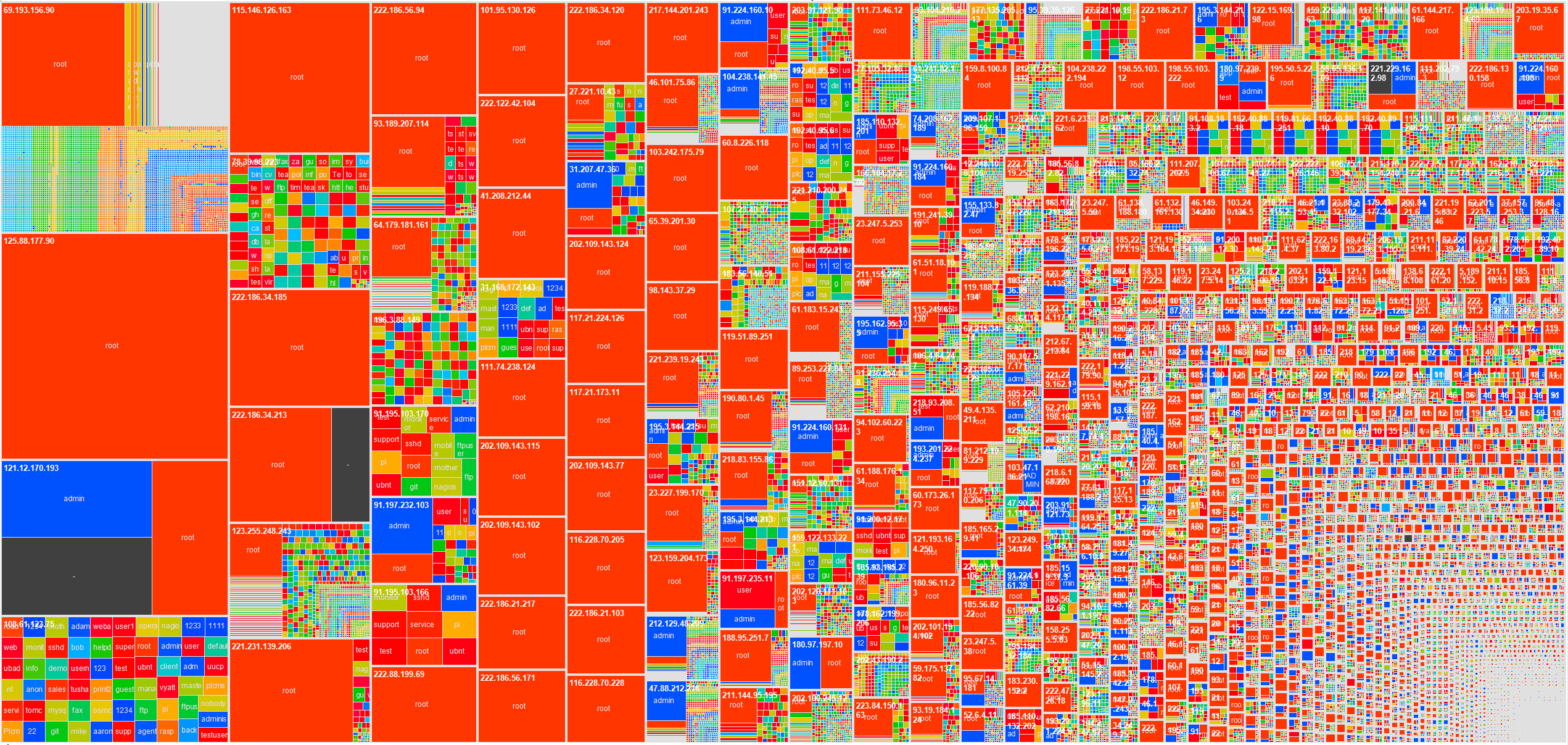
If you are tired of the constant SSH brute-force noise from your IDS and installing fail2ban is just too simple for you, you can use SSH Canary to monitor attackers and better understand the attributes of their campaigns against your systems. It is also nice to know if their dictionaries include some of your passwords at the same time.Once you have some date, you can start looking into the patterns associated with the brute forcing tools and campaigns as shown in the next two heat maps distilling 12 months of log data from sshcanary.
Implimentation
You must first generate a server key for sshcanary to present when clients connect.|
% ssh-keygen -t rsa -f server.key |
If you want to run sshcanary as a non-privileged user or in conjuntion with a real ssh server, you can use iptables to forward connections to sshcanary on an alternate port.
The following forwards all inbound ssh connections destined for TCP/22 to TCP/2222.
|
# /sbin/iptables -A PREROUTING -t nat -p tcp --dport 22 -j REDIRECT --to-port 2222 |
When you start sshcanary, use -p 2222 or --port 2222 and all inbound ssh connections will be forwarded to your sshcanary.
If you want to allow local connections to a real ssh server from your trusted network (e.g. 192.168.10.0/24) but all other ssh connections to be forwarded to your sshcanary, you can use iptables to forward connections if they don't originate on your trusted network.
|
# /sbin/iptables -A PREROUTING -t nat -p tcp -s ! 192.168.10.0/24 --dport 22 \ -j REDIRECT --to-port 2222 |
A simple and dangerous way to run sshcanary is on the default ssh port as root.
|
# sshcanaryd -l /var/sshcanary/server.log -k /var/sshcanary/server.key |
A better way to run sshcanary is to set an effective UID/GID using the -u|--user and -g|--group options as shown below.
|
# sshcanaryd -p 2222 -u sshcanary -g sshcanary -l /var/sshcanary/server.log -k /var/sshcanary/server.key |
The installation includes an RC script for Linux that starts sshcanary in the above fashion but also enables random "traps" where sshcanary acts like the authentication was successful as seen below.
|
# sshcanaryd -p 2222 -u sshcanary -g sshcanary -l /var/sshcanary/server.log -k /var/sshcanary/server.key -t 1000 |
Logging is done in two places, system related events are logged to syslog and authentication events are logged to the specific log file as shown below.
What sshcanary sends to syslog:
|
Apr 17 12:29:57 server-dev sshcanaryd: sshcanaryd v0.6 [Apr 1 2021 - 20:57:47] started Apr 17 12:30:10 server-dev sshcanaryd: Client sent service message Apr 17 12:42:50 server-dev sshcanaryd: Client sent service message Apr 17 12:42:50 server-dev sshcanaryd: Client tried to connect without authenticating Apr 17 12:43:51 server-dev sshcanaryd: Client sent service message Apr 17 12:43:51 server-dev sshcanaryd: Client tried to connect without authenticating Apr 17 14:05:12 server-dev sshcanaryd: Error exchanging keys: [] |
What sshcanary writes to the log:
|
date=2021-04-16@23:47:59 ip=91.197.232.103 user=support pw=support date=2021-04-16@23:48:02 ip=91.197.232.103 user=sysadmin pw=admin date=2021-04-16@23:48:04 ip=91.197.232.103 user=telecomadmin pw=nE7jA%5m date=2021-04-16@23:48:06 ip=91.197.232.103 user=telnet pw=admin date=2021-04-16@23:48:08 ip=91.197.232.103 user=test pw=test date=2021-04-16@23:48:14 ip=91.197.232.103 user=ubnt pw=ubnt date=2021-04-16@23:48:16 ip=91.197.232.103 user=user pw=user date=2021-04-16@23:48:16 ip=91.197.232.103 user=user pw=123456 date=2021-04-16@23:48:16 ip=91.197.232.103 user=user pw=1234 date=2021-04-16@23:48:19 ip=91.197.232.103 user=user1 pw=1234 |
To get a list of all the options, you can execute the command with the -h or --help switch.
|
~/git/sshcanary$ ./src/sshcanaryd --help sshcanaryd v0.6 [Jun 10 2021 - 01:13:20] syntax: sshcanaryd [options] -c|--chroot {dir} chroot to {dir} -d|--debug {lvl} enable debugging info (0-9) -D|--daemon run in the background -h|--help this info -k|--key {fname} filename where ssh key is stored -l|--log {fname} filename where events will be logged -L|--listen {addr} address to listen on -p|--port {portnum} port to listen on (default:22) -P|--pid {fname} filename where pid is stored -t|--trap {freq} randomly report success (default:1000) -u|--user {uname} user to run as -g|--group {gname} group to run as -v|--version display version information |