HOME
SCRIPTS
PROJECTS
READING
CV

NEWS
2021-05-29 SSH Canary(sshcanary) v0.6 has been released!
I just pushed an updated version to sshcanary with some random ssh banners and minor improvements. This
is a handy way to see who is banging on your ssh servers including the usernames and passwords they
are using.
2021-01-14 Log Templater(tmpltr) v0.10 has been released!
I just pushed an updated version of tmpltr with performance improvements (thanks Tom)!
2018-12-10 Log Pseudo Indexer(logpi) v0.6 has been released!
Searching through a large dataset was taking too long, so I updated and released a small utility
that will index addresses in arbitrary formatted text data. Once a pseudo index has been generated,
finding interesting data is pretty quick. Very helpful when you want to find the bad guys.
2018-01-03 Wirespy(wsd) v0.6 has been released!
I spent some time over the holiday to finish the new version of wirespy. It now supports
off-line mode using PCAP files, logs more metadata including TCP flows and can save
flow state across executions.
2016-07-06 Difftree(dt) v0.5.8 made it into a trade journal!
Difftree earned 5 stars in Linux Pro Magazine's July issue #188 with a nice quote "Difftree is convincing due to its speed, flexibility,
and simple operation. Numerous examples on the project
site and man page help out with the first steps."
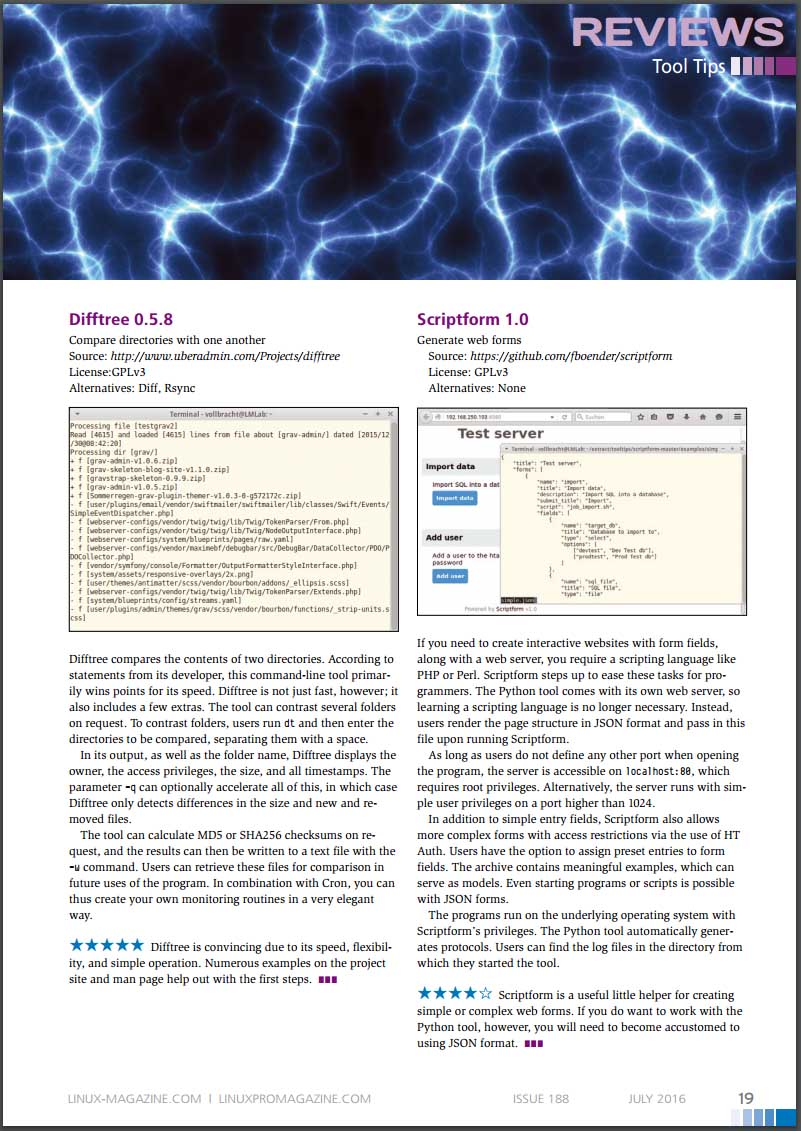
* Image included with permission from linuxpromagazine.com
2016-03-27 PDF Carver(pdfcarve) v0.7 has been released
I had a need to extract a malicious binary from a PDF file at CanSecWest this year and was inspired to
dust off my PDF carving code and fix some bugs.
2015-12-29 Difftree(dt) v0.5.8 has been released
I just finished updating difftree to play nicely with ATIME and to report on changes. This come in handy
when you need to see when a file was accessed across a series of time periods. Run difftree every day and
it is simple to see what has happened in a directory tree over time.
2015-08-23 Difftree(dt) has moved from SourceForge to GitHub
I have started moving the many of my projects that could benifit from more community involvement to GitHub. Difftree is the second project to make the trek and I can't wait to see how it improves over time!
2015-08-23 Log Templater (tmpltr) has moved from SourceForge to GitHub
After being forced to use GitHub to help port passivedns to OpenBSD, it is clear that GitHub is far better
than SourceForge.
2015-07-26 Freshening The Wiretappers Toolkit (TWT)
I have been modernizing The Wiretappers Toolkit (TWT)
and just finished standing up a new packet vacuum for my home office. CappuccinoPC makes a nice small form factor fanless machine.
The machine includes an Atom D525, 4Gb Ram, 4xUSB, 4x1Gb Ethernet, RS232 and room for one 2.5" HDD:

I added a 2TB HDD for $110 and an extra external heat-sink for $8. Out the door for $440.
2014-12-03 Selling Packet Vacuums Door-to-Door
Thanks to the IANS Faculty for inviting me to speak
about my second most favorite incident response tool (Packet Vacuums)!
2014-09-18 Enough with the BSoD!
I gave up in frustration at
my Intel Extreme MB
with the BSoD, hangs, thermal events
and on and on. So, time for an upgrade! I switched to an ASUS
Rampage Black Edition. Along with the
MB, CPU and
Ram,
I upgraded my SDD
and HDD configuration.
Boot speed times are as follows:.
2
x 500Gb Samsung 840 EVO SSD (Raid-0)
Sample
1
Sample
2
Sample
3
Average
Boot to Login
27.70 sec
25.80 sec
27.00 sec
26.30 sec
Login to Desktop
3.40 sec
2.50 sec
2.70 sec
2.70 sec
Login to
Chrome Open/Page Loaded
4.50 sec
4.10 sec
4.10 sec
4.20 sec
Now the really important thing is how does this new computer run for gaming? Well, here is the benchmark for
the default motherboard confuguration (no overclocking):
The 2 x RAID-0 Samsung SSD performed much better than the 4 x RAID-0 drives I had previously used:
An additional surprise was how well the 4 x RAID-5 Samsung 2.5" HDD performed:
2013-12-31 Log Templater (tmpltr) v0.6 is now available
I have been laying some ground work for implementing log chain templates in the next version of Log Templater.
Part of that work includes adding support for more field types (IPv4, IPv6, MAC Address and HEX numbers).
These changes clean up the templates and make it simpler and faster to find some key data when responding to
a threat.
2013-04-03 Geeking out with Marcus Ranum - Take 2
My last session
with Marcus in February may have lacked "Marcus", but there was enough participation and positive feedback that he
asked me to come back and have a more detailed discussion. This time, we had a chance to dig much deeper into the topic and
came up with a couple of interesting ideas that we are now percolating on. Perhaps this will lead to a new tool in our kit.
The webcast is available and who knows what may come next.
2013-02-19 Geeking out with Marcus Ranum
I was looking forward to spending some quality
geek out
time with Marcus today talking about logging
and log analysis. Unfortunately, Marcus fell victim to the Webcast gremlins at a hotel in Germany and
was not able to join me. I still had a good time talking with Allan
about all things "logging" but I am looking forward to geeking our with Marcus some other time.
The webcast has been posted along with some takeaways.
2013-01-20 Hosting ISOI 11
I had the honor and privilege of hosting ISOI 11 in January.
There was an amazing array of speakers and topics. I can't wait for ISOI 12!
Special thanks to Dragos for the use of the secure WiFi gear.
2012-06-27 Upgraded GPU Cracker
With the recent breaches of authentication credentials around the Interwebs, I decided to upgrade my GPU
Cracker and see how it performs and how hot my office can get all at the same time. I replaced my aging
Radeon 5xxx boards with three Radeon 7970's
and one Radeon 6970. SHA1 is now running at almost 6T computations
per second using oclHashCat-Plus.
Time to port Nightengale (BaraCUDA) to OpenCL and see how she runs!

2012-02-04 Passive Proxy Daemon (pproxyd) v0.2 is now available
I have been procrastinating about building a libpcap based sniffer that reassembles web traffic and
generates Squid proxy logs for years.
I tried to use Mike Poor's "development via osmosis" trick with a couple of buddies but in the end, I was forced
to put it together in the last couple of weeks to help solve a vexing web application problem. So, in a pinch,
I pulled out the paper clips, rubber bands and chewing gum. Then I read the docs on libnids.
2012-01-17 Log Templater (tmpltr) v0.5 is now available
After some very helpful and specific feedback about the last version of tmpltr, I have added a few additions
including faux clustering for the occasion when it is handy to know what on a given log line has not changed.
There is a performance penalty for this extra processing, but not as much as I had originally expected. The
table below shows average performance metrics on a Linux VM running on an i7 @ 3.2GHz.
Log size and type
Avg. Line Len
Avg. Arg Count
Args Stored
Avg. Lines per Min
18M Line Cisco FW Log
180
32
0
12,004,023/min
18M Line Cisco FW Log (Clustered)
180
32
24,009
4,093,802/Min
11M Line Apache Access Log
246
44
0
9,453,905/Min
11M Line Apache Access Log (Clustered)
246
44
21,666
5,563,009/Min
4M Line Windows Event Log
793
90
0
2,854,123/Min
4M Line Windows Event Log (Clustered)
793
90
70,361
1,183,226/Min
In addition, I have added a greedy mode where the templater will ignore double quotes. This is very useful
when processing web server logs. In non-greedy mode, tmpltr will assume most things in between a pair of double
quotes are a single string. In greedy mode, all data will be handled the same.
2011-10-17 SSD-Spindle Hybrid
I picked up a couple of Seagate MomentusXT 500Gb
Solid State Hybrid drives to see how they stacked up to
my four 120Gb SSDs running RAID-0. I pulled out the very handy HD TunePro and
the sad fact is, configured as a RAID-0, they were no where near as fast as the pure SSD RAID-0. The linear read and the seek speed was also unpredictable.
Even worse, they did not out perform a couple of 1TB spindle drives running RAID-0 as the chart below shows.
2011-10-01 Log Templater (tmpltr) v0.3 is now available
During the last security incident that I worked on, I needed to grind through 20gb of log files looking
for any odd log lines that would indicate the point where the bad guys got in. If I had done it manually,
I would still be looking at log data. Instead, I built a tool that converted logs into pattern
templates and looked for templates that I had never seen before. This allowed me to zero in on just a
few hundred log lines out of all the data.
2011-07-29 Quick Parser (quickparser) v0.5 is now available
After re-implementing some parser code in difftree with bug
fixes and improved bounds checking, I have ported those changes back to this tool. So, I now present
the new and improved quick parser with less bugs and more bounds checking. Re-energized after touching
the code, I am working on the template based version, which will not be limited to syslog style,
key=value formatted logs.
2011-07-27 Directory Tree Differ (difftree) v0.5 is now available
I have released a new version of difftree with more features and less memory leaks.
This new version adds the ability to save directory tree state and to compare both
directories and archives of directory trees that were previously saved. In addition,
you can hash and compare files if accuracy is more important the speed.
2011-07-16 Directory Tree Differ (difftree) v0.4 is now available
While working on a security incident and fighting with tripwire and Osiris,
I gave up and wrote a fast directory diff tool to allow me to do simple
comparisons between SAN snapshots. To tool was so handy for me, I
figured I would share it.
2011-07-03 SSD Redux
After
fighting with the RAID chassis that I picked up to house my new clutch
of SSD drives I returned them all in a fit of nerd rage and downgraded
from a RAID enclosure to a simple JBOD and larger SSD drives.
I have not been disappointed:
4 x
120Gb OCZ SSD (Raid-0)
Sample
1
Sample
2
Sample
3
Average
Boot to Login
27.30 sec
27.50 sec
27.28 sec
27.28 sec
Login to Desktop
3.50 sec
3.10 sec
3.60 sec
3.40 sec
Login to
Firefox Open/Page Loaded
6.90 sec
5.40 sec
6.05 sec
6.12 sec
Using the very handy HD TunePro
utility, I was able to get a bit more imperial data about the
difference in performance between my old configuration and the new SSD
smoke-fest. Here is the read throughput and access time graph
for
the 4x120Gb OCZ Vertex II SSD (Raid-0):
That
may not look too impressive, but if you compare it to the same read
throughput and access time graph for my old 2x1Tb 7200RPM SATA II HDD
(Raid-0) configuration you will see a bit of a difference and why my
grin is from ear to ear:
2011-05-21 Power supply failure leads to faster boot
times
In
the spirit of tricking people into reading what I write, I have given
in to temptation and deliberately misled you. Yes, my old
power
supply on my Windows development system died and I was forced to
replace it today. In addition, I have improved my boot times
considerably. But the only correlation between the two is
that I
figured I would do a bit of upgrading while I had my case open to
replace the power supply. So, out with the old 850W and in
with
the new 1200W Thermaltake. Additionally, out
with the old 2 x 1TB Raid-0 boot drives and in with the new 4 x 64GB Raid-0 SSD. All
this "high speed, low drag" boot hotness in a fancy 5 1/4" chassis by Patriot. Boot
speed times are as follows:.
2
x 1TB 7200RPM HDD (Raid-0)
Sample
1
Sample
2
Sample
3
Average
Boot to Login
58.00 sec
87.80 sec
87.80 sec
77.87 sec
Login to Desktop
72.50 sec
51.40 sec
32.10 sec
52.00 sec
Login to
Firefox Open/Page Loaded
78.70 sec
63.80 sec
69.80 sec
70.77 sec
4
x 64Gb Patriot TRB SSD (Raid-0)
Sample
1
Sample
2
Sample
3
Average
Boot to Login
32.60 sec
29.40 sec
26.70 sec
29.57 sec
Login to Desktop
5.20 sec
3.40 sec
4.40 sec
4.33 sec
Login to
Firefox Open/Page Loaded
8.30 sec
6.20 sec
6.90 sec
7.13 sec

2010-11-24 Generate password lists using Markov
chains
In
preparation for adding additional password plaintext generators to my GPU password cracker,
I prototyped a simple Markov chain plaintext generator (pwMarkov.pl).
I added it to my John scripts for good measure and am testing
to
see if there is a measurable improvement in cracking efforts now.
2010-05-18 Say goodbye to my liquid cooling system
After
my second coolant leak, it was time to remove my liquid cooling system.
It worked really well at keeping my system cool. It
was not
as effective at keeping it dry. It would not have been as
annoying if I did not have an air cooled system running two dual GPU
graphics cards and a Tesla super computer sitting under my desk at the
same time. My GPU password cracking box just hummed along
without
any overheating issues while my game system learned how to swim in low
conductivity cooling solution. So, I upgraded my case to an
Antec
1200 to match my GPU cracker and replaced my pair of ATI
4895's
with two ATI 5970's and I am back to the races. The 3DMark
numbers speak wonders about both the video cards and the difference
between running Windows XP and Windows 7.
2010-05-12 LogReporter
v1.5 is available
In
response to some feedback from Santiago Zapata, I have updated the
LogReporter.c code to enumerate and report on all active MAC and IP
addresses. Irrespective of the size of your Windows
environment,
you probably struggle with mapping actions in your
firewalls or IDS logs back to users. Stick this program in
your
login scripts and it will provide syslog records for each
login
including NETBIOS computer name, username as well as all active MAC and
IP addresses.
2010-03-19 Mining A/V logs continues to extract gold
After updating my
simple Symantec A/V log parser
I used it to convert syslog Symantec A/V logs to CSV files and loaded
the data into Advizor
Analyst. This type of graph shows interesting re-infection
patterns for individual hosts (horizontal lines), signature updates
following malware blooms (vertical patterns with the same colors) as
well as others.
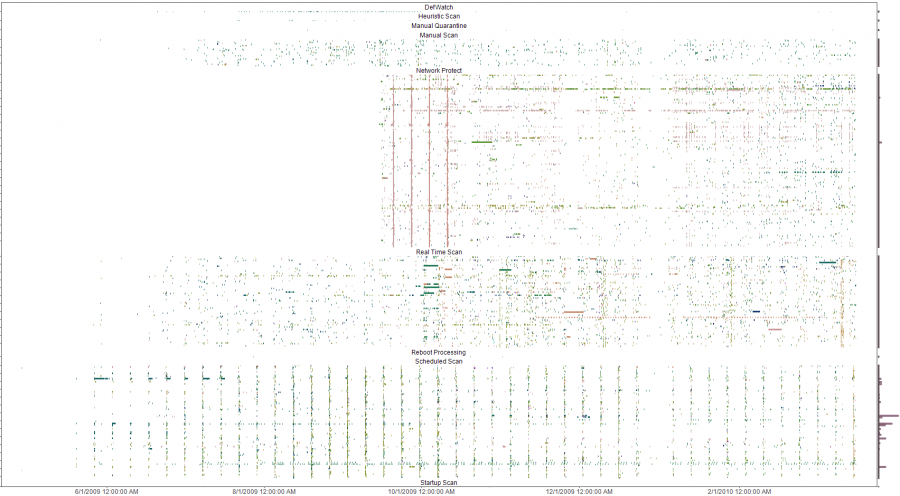
The y-axis is a list of all infected machines so each horizontal line
is a single system (Host names clipped for anonymity). The color coding
is based on the name of the malware with similar names having similar
colors on the pallet. Analysis of the four solid verticals outside of
the weekly schedule scan pattern (the consistent vertical pattern
across all the plots) were four different outbreaks of a network
scanner where signature updates were loaded across all systems and the
IPS started detecting and blocking immediately. The analysis was done
to evaluate the effectiveness of an A/V deployment. The initial impact
was a clear determination that the A/V system needed some attention and
over time, the analysis was used to re-enforce the value of enabling
additional options in the A/V system. Ongoing analysis shows the tempo
of malware detects and changes to the A/V environment.
2009-10-13 LogReporter
v1.4 is available
I
needed to add support for unicode in my simple login tracker.
While poking around in the source, I added a few more
features to
make is a bit easier to use. If you have a small, medium or
large
Windows environment, you probably struggle with mapping actions in your
firewalls or IDS logs back to users. Stick this program in
your
login scripts and it will provide syslog records for each
login
including NETBIOS computer name, username, MAC address and IP.
The new version does a better job with long and unicode
netbios
names and allows you to specify your loghost by name or IP address.
2009-09-21 A/V logs can help you find troubled
systems
I
was culling through the logs on one of my systems the other day and
realized that I was getting a fair amount of alerts from my Symantec
A/V servers. At first, I was not interested in what malware
was
being detected and cleaned but it got me thinking about what
interesting patterns existed. I suspected that the majority
of
malware infections were caused by a minority of users as most malware
these days require some user action. To test this theory I
wrote
a simple parser
to convert the logs to something that I could push into
a visualizer
and started looking for interesting patterns.
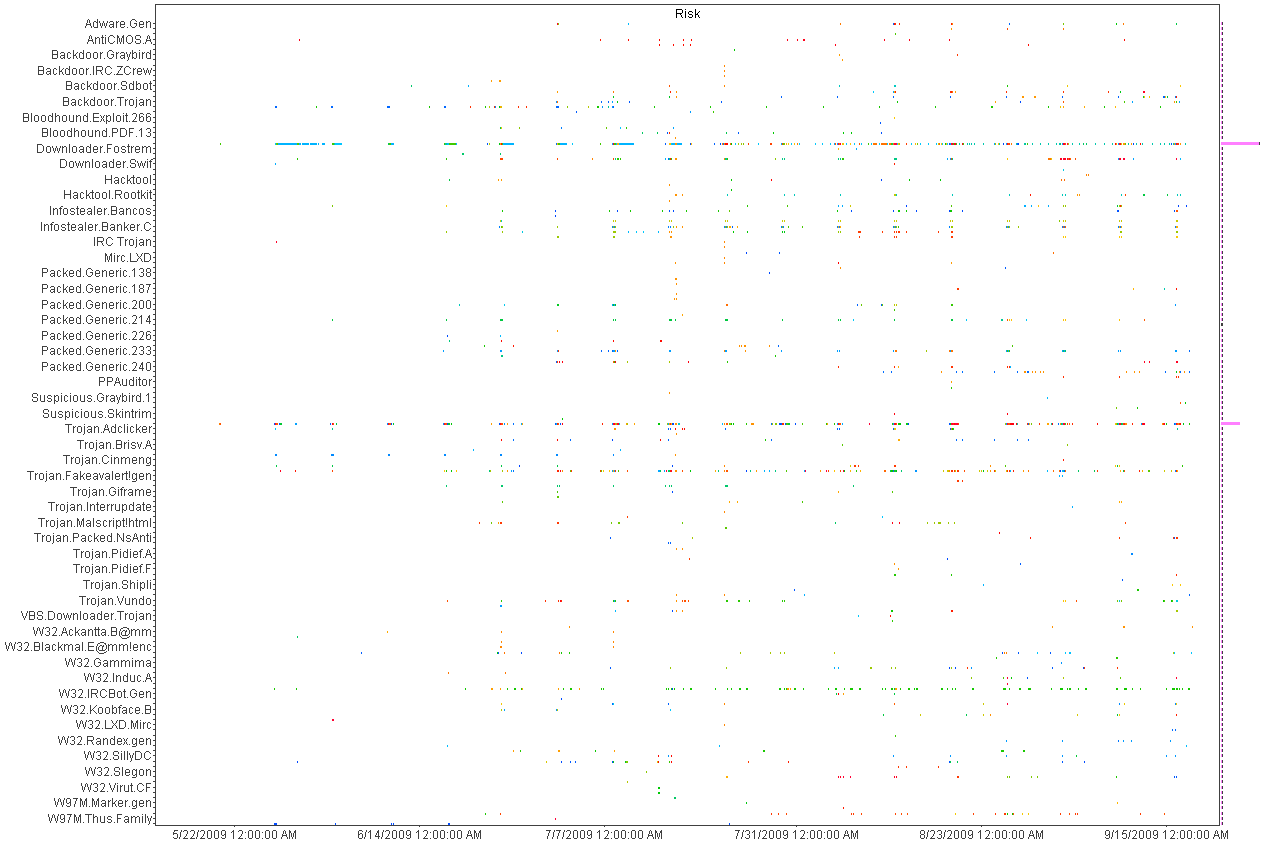
Above
is a histogram plotting A/V detects over time. Each dot is an
piece of malware color coded by host. Horizontal patterns are
a
large quantity of the same piece of malware and vertical lines show
patterns in the A/V detections indicating a schedule for scanning.
This was helpful in deducing the infection and detection
patterns
but not very useful for mapping infections to individual hosts.
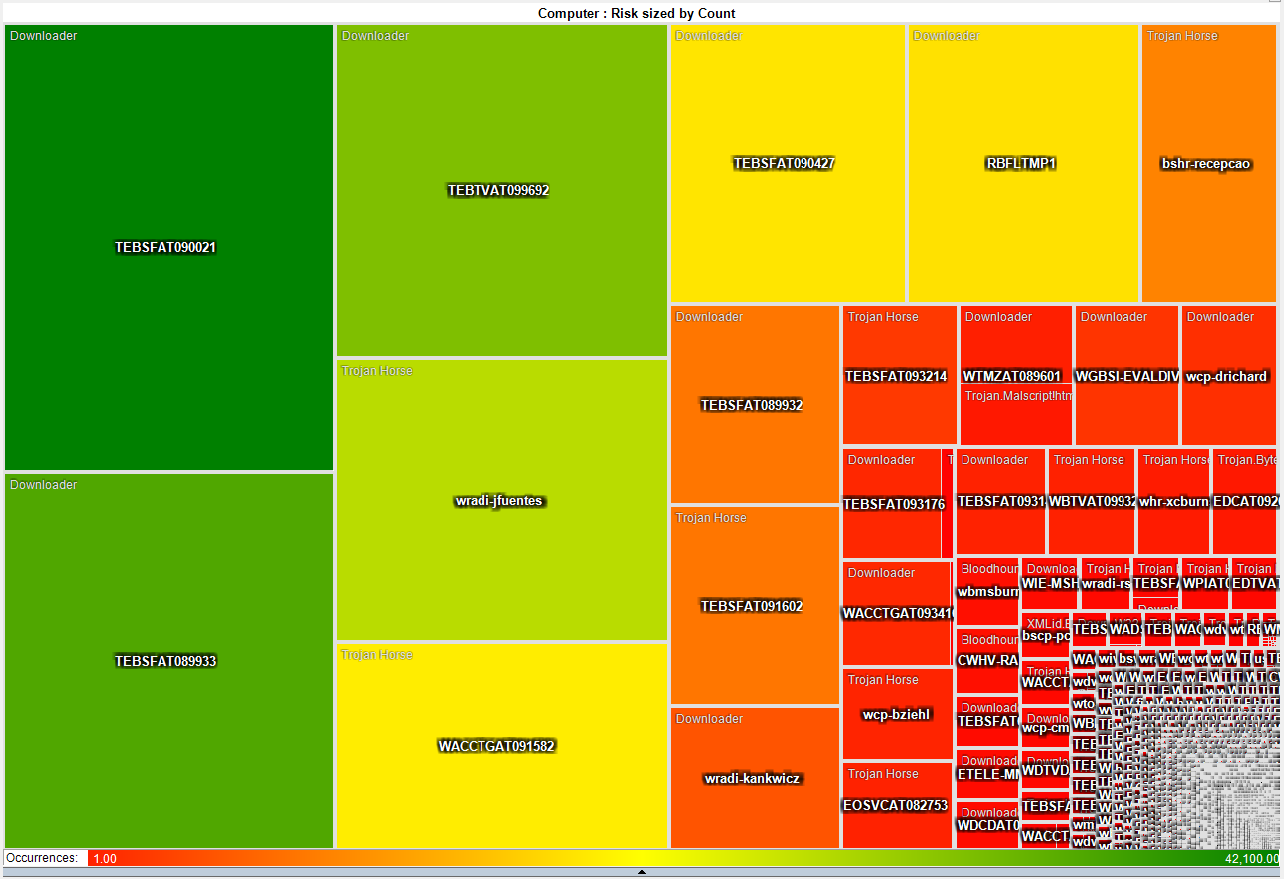
This heat map is much more interesting as it shows that a small number
of systems have a disproportionate
number of detected infections. About 50 systems have more
than
3,000 detected pieces of malware while the rest average just two.
This gives the admin teams a short list of systems that they
can
focus on both with technical as well as awareness based remediation.
2009-05-21 I just switched from air to liquid cooling
After
many years of dreading summer and the system over temp lock-ups I just
made the leap into liquid cooling. I had resisted for the
last
couple of years because the cost of entry in money and time was just
too much. After a couple of days to reading on the net I
decided
that it was too simple and cheap, that waiting any longer was silly.
So
far, I am running 32c on my CPU and 35c on both of my GPUs on fan speed
4 of 10. This is not bad considering ambient is 46c and my
CPU
averaged around 50c on air. I will play with this for a
couple
of weeks while I over clock this and that. Once I have
gathered
more data, I will switch from a serial to a parallel flow configuration
and see if that makes any significant difference.
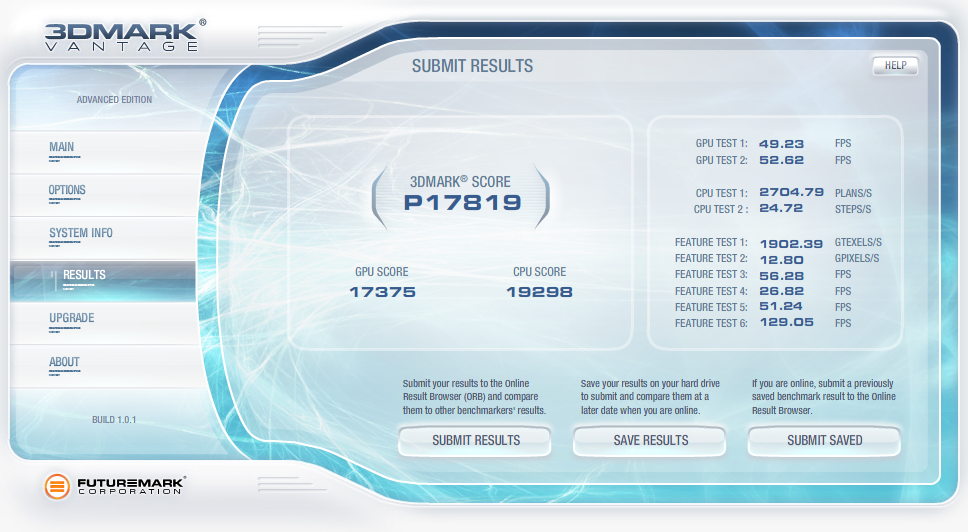
After running the Intel
over clocking utility and installing 3DMark I have a
snapshot of what my new performance is with little tweaking.
2009-04-07 QuickParser
(quickparser) v0.4 released
I
just posted an updated version of QuickParser to SourceForge.
There are some minor bug fixes and changes to the parser to
better support generic logs with key=value pairs.
2008-12-27 Projects on my short list
Of
the long list of projects that I am ignoring most of the time and
banging on when I have a free moment, there are a few that I am putting
on my resolution list to get finished in 2009!
- Log tokenizer, compressor and decompressor
- PDF carver (pdfcarver)
- Network ACL Builder (wirespy)
- IM Sniffer (imspy)
- Forensic packet archiver (The
Wiretapper's Toolkit - TWT)
- DNS Sniffer (pdnsd)
There are also a few ideas that I need to flesh out on paper in 2009
(we shall see how I do).
- "Distrust Engineering", finding the bad guys without
signatures.
- "The State of Information Security Data
Visualization", a Marcus style rant.
- "The
11th Domain of Information Security", how to achieve long term
improvement of the security of your organization by creating a
sustainable information security practice.
2008-08-21 QuickParser
(quickparser) v0.3
In
the spirit of sharing and in the hopes of prodding a co-conspirator
into finishing *his* better, stronger and faster parser, I have
released the source to my regex-less log parser specifically for
Juniper (Netscreen) firewall logs.
2008-07-01 PiRAT
v0.2
I
just upgraded my Nokia N800 to a N810 and it is time to update my tool
chain for OS2008. The new version will sport all of my
favorite
tools including NMAP,
AMAP,
xprobe2,
NBTScan,
NetCat,
Hping2, dsniff,
p0f,
hydra,
John the
Ripper, Snort,
TCPDump,
Metasploit,
Kismet,
Wireshark
(a real pain to build) and many more.
2008-06-19 Transitive Distrust
I have
watched our capability to detect threats degrade year after year as our
adversaries invest more and more time and effort in the pursuit of
stealthiness. As with all arms races, the winner is the faction with
the deepest pockets and lowest overhead. In the corporate
world,
that is a guarantee that the adversaries will always win. I
have
been toying with a different paradigm to identifying threats called
transitive distrust, or as a good friend of mine commented, trust
engineering.
Thesis:
To
test this, I am building with the help of some friends, a system of
instrumentation that applies a simple set of 30-40 rules to all systems
that interact with a given network. Once the rules are
applied, a
trust/distrust map is compiled. This is a very effective
filter
to separate the trusted, and therefore not interesting, from the
untrusted
The system can run
constantly, correcting the evaluated trust/distrust as the data points
change. Distrust
degrades over time so a system that was previously untrusted but no
longer exhibits these traits will become more trusted.
2008-05-31 Monitoring and logging removable media
access with OS/X
I wrongly assumed
that it would
be simple to find an intellectual property (IP) leakage monitoring tool
for removable media on OS/X. It is unfortunate that the
abundance
of this type of tool on Windows has not rubbed off on Mac.
That
said, I hacked together a volume monitoring daemon (vmd)
to provide logging of file activity on removable devices on systems
running OS/X. It is the poor mans solution to the problem.
It uses syslog, so it is possible to have all of your Mac's
point
to a central syslog server and gain arms length auditing of removable
media across all of your OS/X based systems with this little daemon.
A word of caution, I used the fsevents functionality of
10.4 and 10.5 which is not a standard hook for applications.
So don't be surprised if this stops working in a future
version of
OS/X.
2008-04-26 Malware detection through data visualization
Raffael over at secvis.org has been
working to improve the overall state of information security data
visualization. Along with logging, data visualization has
been a
pet project of mine for several years. I have, from time to
time
used visualization to filter through large volumes of data looking for
intruders, malware and data breaches.
I have been trying to find a way to go through firewall logs at a large
corporation where a days worth of traffic equates to 25Gb of
uncompressed logs
and mapping portions of the logs to simple 2D graphs helps
to point out obvious and sometimes subtle anomalies.
When you plot the destination IP address as an integer over time, many
interesting patterns are highlighted.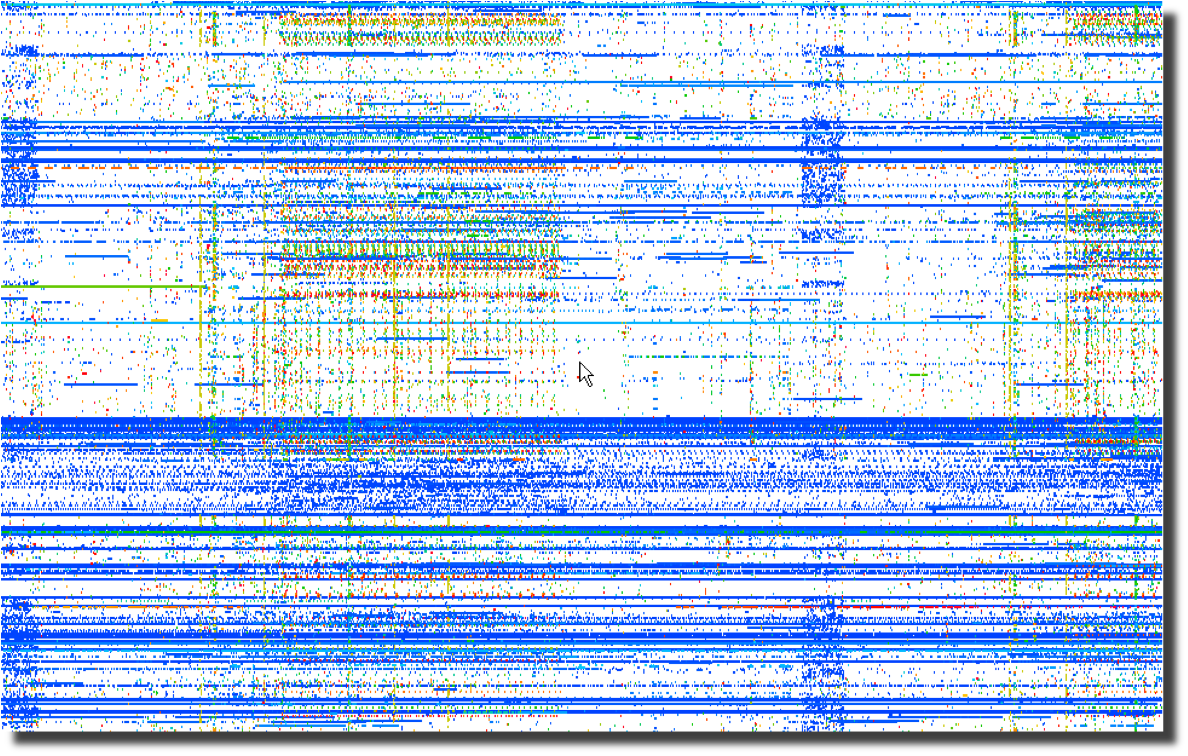 Even more interesting than the horizontal patterns indicating
continuous traffic to specific IP addresses are the vertical clusters
with regularly repeating frequencies.
Even more interesting than the horizontal patterns indicating
continuous traffic to specific IP addresses are the vertical clusters
with regularly repeating frequencies.
Next, a plot of the same data using the destination port number over
time points to obvious port scanning in the form of diagonal
lines as well as odd patterns that sync with the previous destination
IP address plot. 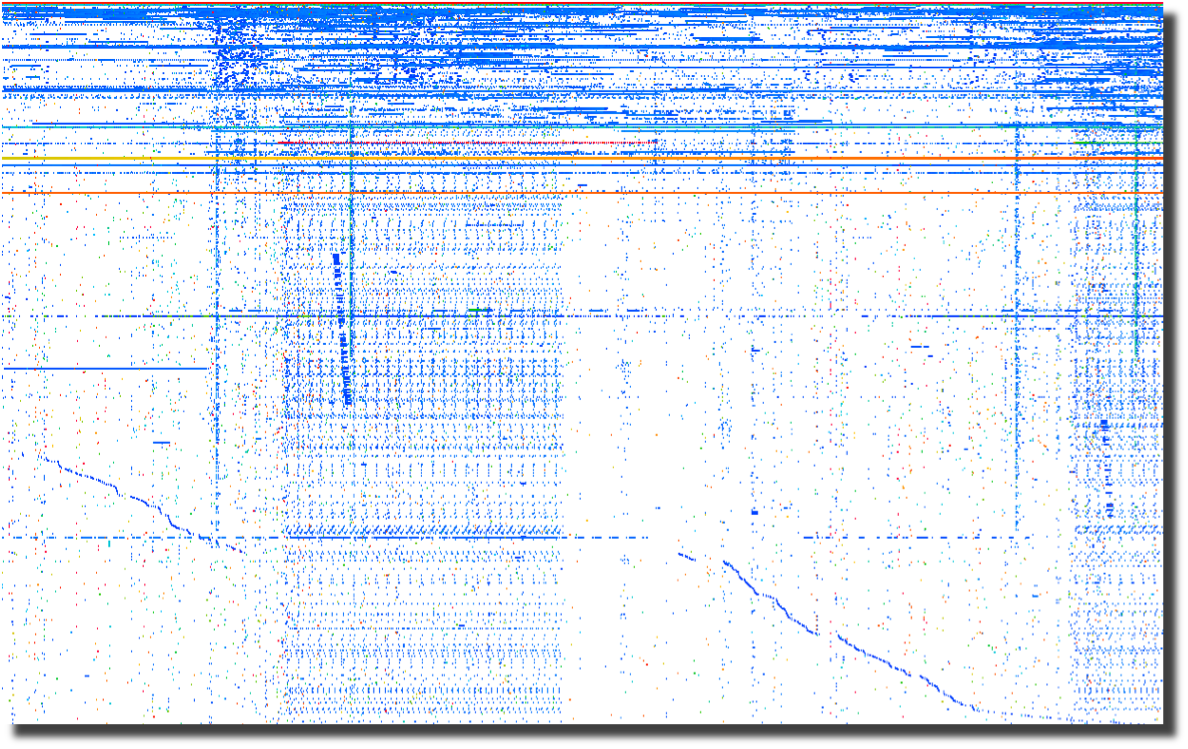
The last plot of source ports over time points to crafted packets.
Normal sockets allocated through the operating system will
have
positively incrementing source ports for each new connection.
Look for the horizontal lines and you have most likely found
tools
that are not using the operating system to instantiate new sockets.
To me, this screams packet crafting. 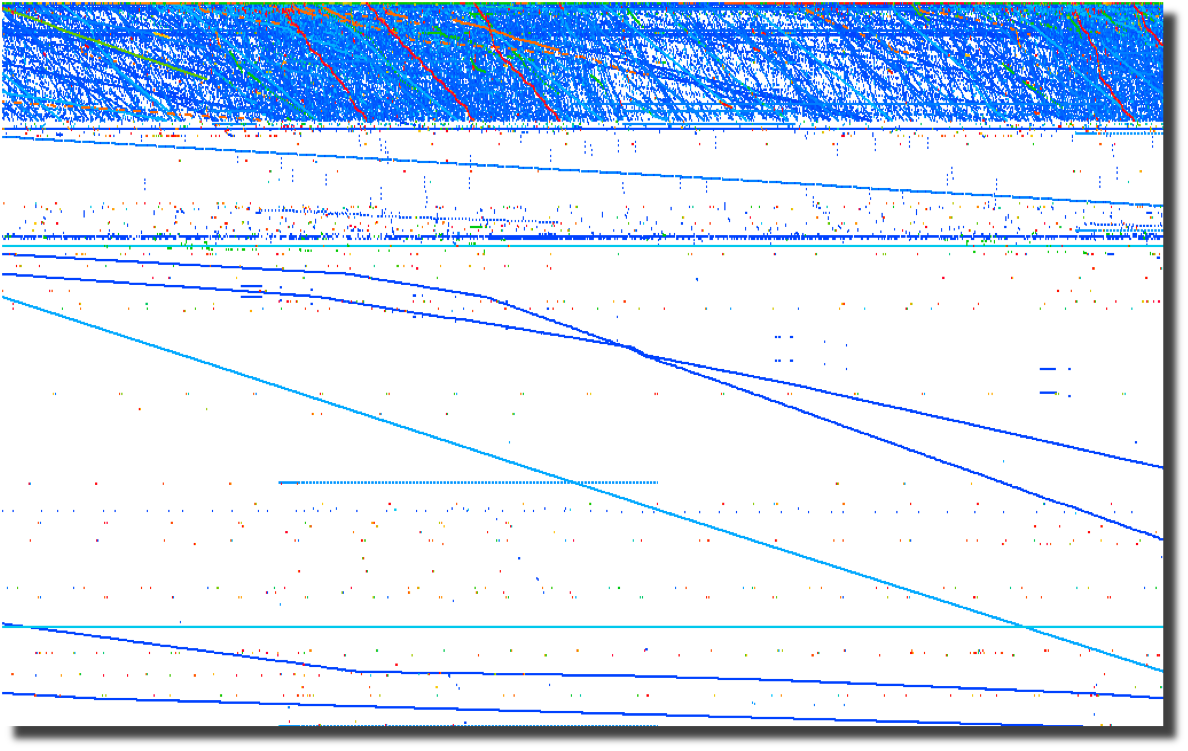
All of these graphs were created by parsing firewalls logs using a perl script and
loading them into Advizor
Analyst.
Web server logs are another source of interesting data if you are able
to separate the wheat from the chaff. Apache2Dot.pl
is a small script that makes clear diagrams of website interactions.
2008-03-19 Sumo
vs. Judo
Over the course of my
career, it has become clear to me that Japan's national
sport offers a perfect analogy for the current state of
information security.

2008-03-18 Is it time for Computer Access
License Agreements?

Now that the US Federal Government is regularly seizing, coping and
snooping into the computers of US Citizens returning home, what can we
do to protect the privacy that we hold dear? The most obvious
response is to encrypt your drives using whatever tools you deem
appropriate. I had considered a "FiST
US Customs" campaign, but I suppose that would not be very
professional. I had also considered implementing some
anti-forensic countermeasures on my computers. A simple
change to
one of the many open source disk wipers could fill your unallocated and
slack space with billions of partial GIF
images. That sure would make going through the preview in EnCASE a bit more
tedious. And I suppose there are even more 'active'
countermeasures available to those who are not squeamish about fighting
back. After all, I have nothing to hide, and its not my job
to
make it easy for Law Enforcement to do theirs. Then it
occurred
to me as I was ranting to a fellow infosec practitioner. What
we
need is the equivalent of a EULA for our computers. Something
that warns off would-be snoopers who decide to look at our computers
without a warrant. I suppose putting one of these stickers on
your computer and your hard drives is just asking for them to be
confiscated, never to be seen again. But it sure would make a
great story.
2008-03-14 DPS for life!





Distance makes the
heart grow fonder.
2008-01-24 Passive syslog monitor v1.2.1 (psmd) has been
released
After many days of
pushing
hundreds of gigabytes of data through it, the new version of psmd
offers many bug fixes and a new TCP reassembler which notes lost log
data due to dropped packets. Along with the new features,
psmd
still offers many others:
- Passive syslog monitoring (no listening ports)
- Support for syslog over UDP and TCP (syslog-ng)
- Archiving of all log data with proper time stamps,
source and dest MAC and IP address
- MD5 and SHA1 hashing of all archived logs
- Forwarding of syslog data with or without forged
source IP addresses
- TIMEMARK insertion to handle time zone and time skew
issues
2007-09-25 Sending a shout out to my com padre
Further continuing
the South
Park theme, I bring you yet another image of a fellow student of Sun
Tsu and InfoSec practitioner. Can you guess who it is?

I just want to know one thing, where is my cut of the shirt
action Tom?
2007-09-22 Regexless log parsing (quickparser)
A co-conspirator
and I have been
building some log analysis tools. To feed data to the tools,
we
needed to convert log files into a pseudo XML format. I built
a
couple of regex log parsers in perl but they were very slow.
We
have spent some time talking about other ways of parsing logs and I
cannibalized a log compression tool that I had built using regexless
parsing and found out that it is pretty fast. By fast I am
talking 2.6M lines per minute on a single processor 2.5GHz PC running
linux and 950K lines per minute on a SunBlade 2000 with 1GHz processors.
Check out my quickparser,
it chews up syslog data from Netscreen firewalls. It should
work
properly with any syslog source that uses key/value pairs separated by
a '='.
2007-08-17 "Better out than in, that's what
I always say!" -Shrek
InfoSec is from
Pluto, NetOps is from Jupiter
As
the tenth largest body orbiting our sun, Pluto has in recent years been
center stage to heated discussion about what makes a planet.
Living on
Pluto as it spins around its eccentric orbit at a chilly 29 AU to a
really chilly 49 AU from our Sun would be quite a challenge.
It's cold
and lonely and most people don't even consider Pluto a planet including
the IAU which on August 24th, 2006 relegated Pluto to 'dwarf planet'
status. It is surprisingly similar to the life as an InfoSec
professional. They are center stage to heated discussions
about the
significance, priority and impact of information security on
organizations. Aside from government and financial circles,
InfoSec is
at best an ugly stepchild and at worst is the bastard child of an
adulterous relationship. To the rest of the world, information security
is the curse of 'due diligence and care' that is resisted, ignored and
hated with vim and vigor likened to paying taxes. In short,
information security is the group that tries to make organizations do
silly things that cost too much and delay projects for no good reason
because "security breaches only happen to the other guy, not us".
The fifth planet from our Sun, Jupiter, stacks up as the
largest body in our solar system at 2 ½ times more massive
that all the
other planets put together. Jupiter keeps showing up in the
press with
missions like Voyager, Cassini and Galileo. If that
was not enough of
a spotlight, consider the Shoemaker-Levy 9 Impacts in July of
1994.
Jupiter is big, bright and full of hydrogen. Everybody knows
what
Jupiter looks like and we thank Jupiter for its gravitational pull, we
all prefer to have things hit Jupiter instead of us. Network
operations, like Jupiter, gets lots of visibility, is generally large
in comparison to other operational bodies and is full of an amazingly
diverse class of gases. And we all know to make a bee-line to
NetOps
when we can't surf the Internet.
Putting aside the above analogies, there are some fundamental
differences between InfoSec and NetOps and over the years I have
struggled to understand those differences as a way to improve my
interactions with my family on Jupiter. At its most
fundamental level,
the difference between "network" people and "security" people is that
one is focused on ensuring that packets move and the other
isn't. I
will leave ascribing the correct labels to you, the reader.
This fundamental schism is surprisingly wide and deep. And,
we are talking astronomic units (AU) here, not Grand Canyon
distances.
Countless times, I have gone to my brothers and sisters on Jupiter
asking for help in reducing the 'attack surface' of a problem and time
and time again, I have received feedback and lumps. With each
tongue-lashing and stroke I have heard "We don't have time or
resources". For a long time, I assumed that part of my family
was just
lazy.
The Epiphany came to me last week, NetOps is from Jupiter, not
my home town over on Pluto. When I ask network operations to
install
an ACL or firewall, they resist. Not out of laziness but as
an
instinctive response built into the very fabric of each resident of
Jupiter. Asking to block traffic is like asking them to move
to Pluto,
which is far too small and cold. When I look at the problem,
I see it
through the eyes of a happy resident of Pluto where blocking traffic is
just a matter of simple changes to router and firewall
configurations.
Add in a little audit trail and some monitoring for giggles, and it is
a happy place for all. But when someone from Jupiter looks at
preventing packets from reaching their final destination, it is like
preventing a packet from reaching it's pre-ordained and rightful place
in the universe and the ramifications will topple everything.
Not to
mention making a mess in the holiest of places, the change control
archive.
So, consider this, the next time you endeavor to make the
journey from Pluto to Jupiter to request a packet filter, start the
conversation with "Every packet is sacred", and bring lots of photos of
home to reassure them that Pluto is not all bad, because a network
operator who turns up a firewall is actually a Plutonian on vacation in
a warmer climate.
Ron Dilley
:Plutonian
2007-07-31 Blatant C.a.S.E.
I am sorry Marcus, I just can't keep it to myself . . .

2007-07-30 Passive syslog monitor v1.0 (psmd) has been
released
Thanks to mjr for suggesting an interesting solution to the problem of
how to handle broken time in logs. By broken I mean logs from
systems without accurate time, mixed time zones and the most annoying
of all . . . daylight savings. The new version of psmd
inserts
time marks which record the time skew between log time and the time
that the log is sucked off the wire.
2007-03-22 Yet another project (PiRat)
I just picked up a Nokia
N800
with the intent to port all of my InfoSec related tools to this
ultra-small computing platform. There is a pretty well put
together development environment and a strong open source development
community branded as Maemo.
2006-09-25 ÜberAdmin has a new website
After several years of a really plain website, I decided to give up
using vi for web development and switched to a more modern tool which
was capable of making really fancy websites. Though I opted
not
to make this site much fancier than the vi version, I at least used
more than one font this time.
2006-09-18 Passive syslog monitor daemon has a new home
at SourceForge (psmd)
After tweaking on my code an hour at a time over the last year, I have
finally been pushed and prodded enough to actually release it to the
public. As I am not a programmer by trade and know just how
much
gum and how many rubber bands are used to hold it together, I do so
with a bit of reservation. With all the messages on the logs
mailing list about signing syslog, what else could I do?
2021-01-14 Log Templater(tmpltr) v0.10 has been released!
I just pushed an updated version of tmpltr with performance improvements (thanks Tom)!
2018-12-10 Log Pseudo Indexer(logpi) v0.6 has been released!
Searching through a large dataset was taking too long, so I updated and released a small utility
that will index addresses in arbitrary formatted text data. Once a pseudo index has been generated,
finding interesting data is pretty quick. Very helpful when you want to find the bad guys.
2018-01-03 Wirespy(wsd) v0.6 has been released!
I spent some time over the holiday to finish the new version of wirespy. It now supports
off-line mode using PCAP files, logs more metadata including TCP flows and can save
flow state across executions.
2016-07-06 Difftree(dt) v0.5.8 made it into a trade journal!
Difftree earned 5 stars in Linux Pro Magazine's July issue #188 with a nice quote "Difftree is convincing due to its speed, flexibility,
and simple operation. Numerous examples on the project
site and man page help out with the first steps."

* Image included with permission from linuxpromagazine.com
2016-03-27 PDF Carver(pdfcarve) v0.7 has been released
I had a need to extract a malicious binary from a PDF file at CanSecWest this year and was inspired to
dust off my PDF carving code and fix some bugs.
2015-12-29 Difftree(dt) v0.5.8 has been released
I just finished updating difftree to play nicely with ATIME and to report on changes. This come in handy
when you need to see when a file was accessed across a series of time periods. Run difftree every day and
it is simple to see what has happened in a directory tree over time.
2015-08-23 Difftree(dt) has moved from SourceForge to GitHub
I have started moving the many of my projects that could benifit from more community involvement to GitHub. Difftree is the second project to make the trek and I can't wait to see how it improves over time!
2015-08-23 Log Templater (tmpltr) has moved from SourceForge to GitHub
After being forced to use GitHub to help port passivedns to OpenBSD, it is clear that GitHub is far better
than SourceForge.
2015-07-26 Freshening The Wiretappers Toolkit (TWT)
I have been modernizing The Wiretappers Toolkit (TWT)
and just finished standing up a new packet vacuum for my home office. CappuccinoPC makes a nice small form factor fanless machine.
The machine includes an Atom D525, 4Gb Ram, 4xUSB, 4x1Gb Ethernet, RS232 and room for one 2.5" HDD:

I added a 2TB HDD for $110 and an extra external heat-sink for $8. Out the door for $440.
2014-12-03 Selling Packet Vacuums Door-to-Door
Thanks to the IANS Faculty for inviting me to speak
about my second most favorite incident response tool (Packet Vacuums)!
2014-09-18 Enough with the BSoD!
I gave up in frustration at
my Intel Extreme MB
with the BSoD, hangs, thermal events
and on and on. So, time for an upgrade! I switched to an ASUS
Rampage Black Edition. Along with the
MB, CPU and
Ram,
I upgraded my SDD
and HDD configuration.
Boot speed times are as follows:.
2
x 500Gb Samsung 840 EVO SSD (Raid-0)
Sample
1
Sample
2
Sample
3
Average
Boot to Login
27.70 sec
25.80 sec
27.00 sec
26.30 sec
Login to Desktop
3.40 sec
2.50 sec
2.70 sec
2.70 sec
Login to
Chrome Open/Page Loaded
4.50 sec
4.10 sec
4.10 sec
4.20 sec
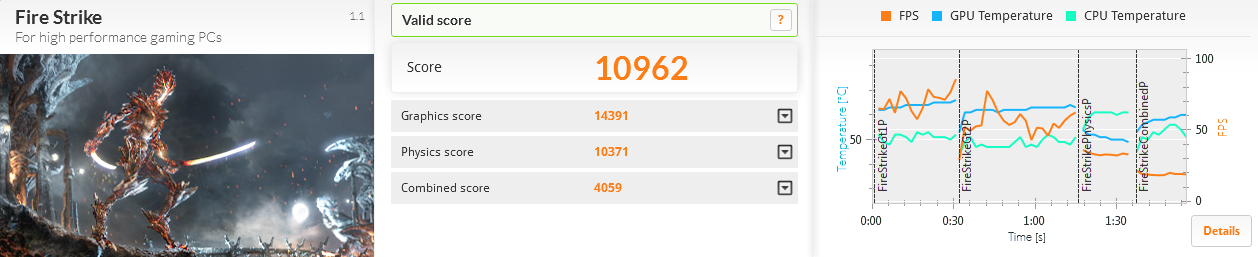
Now the really important thing is how does this new computer run for gaming? Well, here is the benchmark for
the default motherboard confuguration (no overclocking):

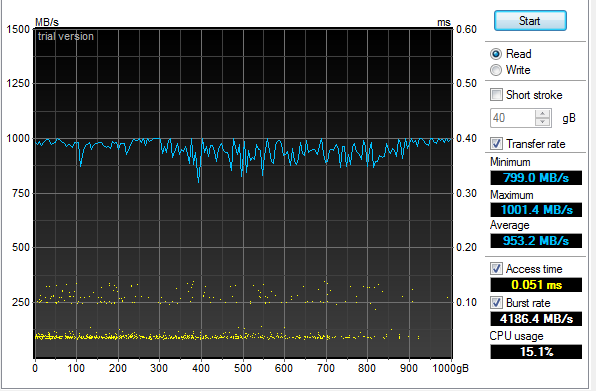
The 2 x RAID-0 Samsung SSD performed much better than the 4 x RAID-0 drives I had previously used:

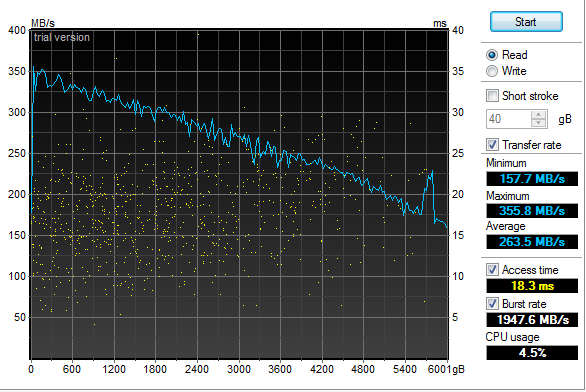
An additional surprise was how well the 4 x RAID-5 Samsung 2.5" HDD performed:

2013-12-31 Log Templater (tmpltr) v0.6 is now available
I have been laying some ground work for implementing log chain templates in the next version of Log Templater.
Part of that work includes adding support for more field types (IPv4, IPv6, MAC Address and HEX numbers).
These changes clean up the templates and make it simpler and faster to find some key data when responding to
a threat.
2013-04-03 Geeking out with Marcus Ranum - Take 2
My last session
with Marcus in February may have lacked "Marcus", but there was enough participation and positive feedback that he
asked me to come back and have a more detailed discussion. This time, we had a chance to dig much deeper into the topic and
came up with a couple of interesting ideas that we are now percolating on. Perhaps this will lead to a new tool in our kit.
The webcast is available and who knows what may come next.
2013-02-19 Geeking out with Marcus Ranum
I was looking forward to spending some quality
geek out
time with Marcus today talking about logging
and log analysis. Unfortunately, Marcus fell victim to the Webcast gremlins at a hotel in Germany and
was not able to join me. I still had a good time talking with Allan
about all things "logging" but I am looking forward to geeking our with Marcus some other time.
The webcast has been posted along with some takeaways.
2013-01-20 Hosting ISOI 11
I had the honor and privilege of hosting ISOI 11 in January.
There was an amazing array of speakers and topics. I can't wait for ISOI 12!
Special thanks to Dragos for the use of the secure WiFi gear.
2012-06-27 Upgraded GPU Cracker
With the recent breaches of authentication credentials around the Interwebs, I decided to upgrade my GPU
Cracker and see how it performs and how hot my office can get all at the same time. I replaced my aging
Radeon 5xxx boards with three Radeon 7970's
and one Radeon 6970. SHA1 is now running at almost 6T computations
per second using oclHashCat-Plus.
Time to port Nightengale (BaraCUDA) to OpenCL and see how she runs!

2012-02-04 Passive Proxy Daemon (pproxyd) v0.2 is now available
I have been procrastinating about building a libpcap based sniffer that reassembles web traffic and
generates Squid proxy logs for years.
I tried to use Mike Poor's "development via osmosis" trick with a couple of buddies but in the end, I was forced
to put it together in the last couple of weeks to help solve a vexing web application problem. So, in a pinch,
I pulled out the paper clips, rubber bands and chewing gum. Then I read the docs on libnids.
2012-01-17 Log Templater (tmpltr) v0.5 is now available
After some very helpful and specific feedback about the last version of tmpltr, I have added a few additions
including faux clustering for the occasion when it is handy to know what on a given log line has not changed.
There is a performance penalty for this extra processing, but not as much as I had originally expected. The
table below shows average performance metrics on a Linux VM running on an i7 @ 3.2GHz.
Log size and type
Avg. Line Len
Avg. Arg Count
Args Stored
Avg. Lines per Min
18M Line Cisco FW Log
180
32
0
12,004,023/min
18M Line Cisco FW Log (Clustered)
180
32
24,009
4,093,802/Min
11M Line Apache Access Log
246
44
0
9,453,905/Min
11M Line Apache Access Log (Clustered)
246
44
21,666
5,563,009/Min
4M Line Windows Event Log
793
90
0
2,854,123/Min
4M Line Windows Event Log (Clustered)
793
90
70,361
1,183,226/Min
In addition, I have added a greedy mode where the templater will ignore double quotes. This is very useful
when processing web server logs. In non-greedy mode, tmpltr will assume most things in between a pair of double
quotes are a single string. In greedy mode, all data will be handled the same.
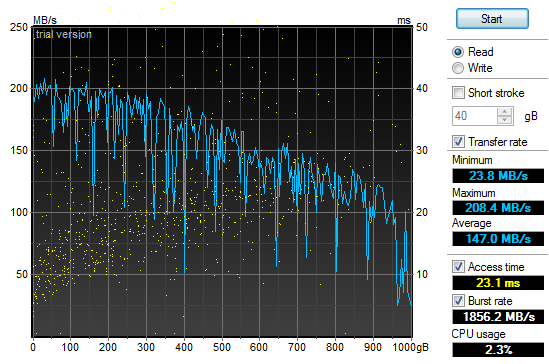
2011-10-17 SSD-Spindle Hybrid
I picked up a couple of Seagate MomentusXT 500Gb
Solid State Hybrid drives to see how they stacked up to
my four 120Gb SSDs running RAID-0. I pulled out the very handy HD TunePro and
the sad fact is, configured as a RAID-0, they were no where near as fast as the pure SSD RAID-0. The linear read and the seek speed was also unpredictable.
Even worse, they did not out perform a couple of 1TB spindle drives running RAID-0 as the chart below shows.

2011-10-01 Log Templater (tmpltr) v0.3 is now available
During the last security incident that I worked on, I needed to grind through 20gb of log files looking
for any odd log lines that would indicate the point where the bad guys got in. If I had done it manually,
I would still be looking at log data. Instead, I built a tool that converted logs into pattern
templates and looked for templates that I had never seen before. This allowed me to zero in on just a
few hundred log lines out of all the data.
2011-07-29 Quick Parser (quickparser) v0.5 is now available
After re-implementing some parser code in difftree with bug
fixes and improved bounds checking, I have ported those changes back to this tool. So, I now present
the new and improved quick parser with less bugs and more bounds checking. Re-energized after touching
the code, I am working on the template based version, which will not be limited to syslog style,
key=value formatted logs.
2011-07-27 Directory Tree Differ (difftree) v0.5 is now available
I have released a new version of difftree with more features and less memory leaks.
This new version adds the ability to save directory tree state and to compare both
directories and archives of directory trees that were previously saved. In addition,
you can hash and compare files if accuracy is more important the speed.
2011-07-16 Directory Tree Differ (difftree) v0.4 is now available
While working on a security incident and fighting with tripwire and Osiris,
I gave up and wrote a fast directory diff tool to allow me to do simple
comparisons between SAN snapshots. To tool was so handy for me, I
figured I would share it.
2011-07-03 SSD Redux
After
fighting with the RAID chassis that I picked up to house my new clutch
of SSD drives I returned them all in a fit of nerd rage and downgraded
from a RAID enclosure to a simple JBOD and larger SSD drives.
I have not been disappointed:
4 x
120Gb OCZ SSD (Raid-0)
Sample
1
Sample
2
Sample
3
Average
Boot to Login
27.30 sec
27.50 sec
27.28 sec
27.28 sec
Login to Desktop
3.50 sec
3.10 sec
3.60 sec
3.40 sec
Login to
Firefox Open/Page Loaded
6.90 sec
5.40 sec
6.05 sec
6.12 sec
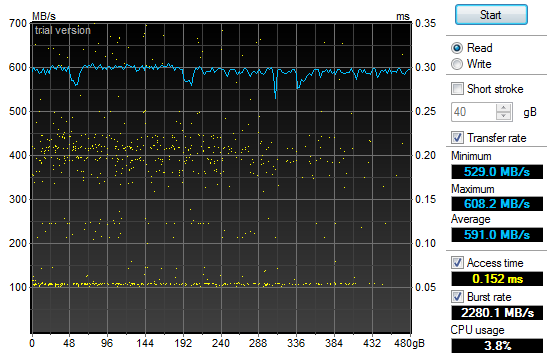
Using the very handy HD TunePro
utility, I was able to get a bit more imperial data about the
difference in performance between my old configuration and the new SSD
smoke-fest. Here is the read throughput and access time graph
for
the 4x120Gb OCZ Vertex II SSD (Raid-0):

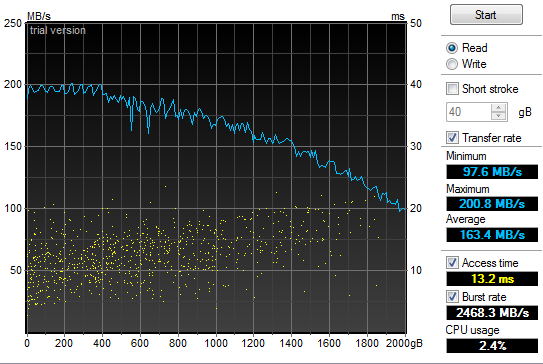
That
may not look too impressive, but if you compare it to the same read
throughput and access time graph for my old 2x1Tb 7200RPM SATA II HDD
(Raid-0) configuration you will see a bit of a difference and why my
grin is from ear to ear:

2011-05-21 Power supply failure leads to faster boot
times
In
the spirit of tricking people into reading what I write, I have given
in to temptation and deliberately misled you. Yes, my old
power
supply on my Windows development system died and I was forced to
replace it today. In addition, I have improved my boot times
considerably. But the only correlation between the two is
that I
figured I would do a bit of upgrading while I had my case open to
replace the power supply. So, out with the old 850W and in
with
the new 1200W Thermaltake. Additionally, out
with the old 2 x 1TB Raid-0 boot drives and in with the new 4 x 64GB Raid-0 SSD. All
this "high speed, low drag" boot hotness in a fancy 5 1/4" chassis by Patriot. Boot
speed times are as follows:.
2
x 1TB 7200RPM HDD (Raid-0)
Sample
1
Sample
2
Sample
3
Average
Boot to Login
58.00 sec
87.80 sec
87.80 sec
77.87 sec
Login to Desktop
72.50 sec
51.40 sec
32.10 sec
52.00 sec
Login to
Firefox Open/Page Loaded
78.70 sec
63.80 sec
69.80 sec
70.77 sec
4
x 64Gb Patriot TRB SSD (Raid-0)
Sample
1
Sample
2
Sample
3
Average
Boot to Login
32.60 sec
29.40 sec
26.70 sec
29.57 sec
Login to Desktop
5.20 sec
3.40 sec
4.40 sec
4.33 sec
Login to
Firefox Open/Page Loaded
8.30 sec
6.20 sec
6.90 sec
7.13 sec

2010-11-24 Generate password lists using Markov
chains
In
preparation for adding additional password plaintext generators to my GPU password cracker,
I prototyped a simple Markov chain plaintext generator (pwMarkov.pl).
I added it to my John scripts for good measure and am testing
to
see if there is a measurable improvement in cracking efforts now.
2010-05-18 Say goodbye to my liquid cooling system
After
my second coolant leak, it was time to remove my liquid cooling system.
It worked really well at keeping my system cool. It
was not
as effective at keeping it dry. It would not have been as
annoying if I did not have an air cooled system running two dual GPU
graphics cards and a Tesla super computer sitting under my desk at the
same time. My GPU password cracking box just hummed along
without
any overheating issues while my game system learned how to swim in low
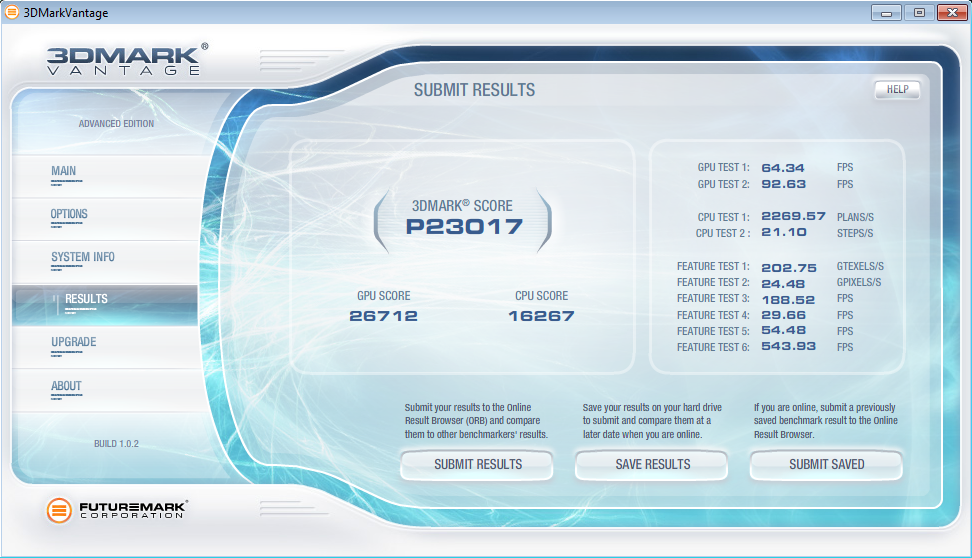
conductivity cooling solution. So, I upgraded my case to an
Antec
1200 to match my GPU cracker and replaced my pair of ATI
4895's
with two ATI 5970's and I am back to the races. The 3DMark
numbers speak wonders about both the video cards and the difference
between running Windows XP and Windows 7.

2010-05-12 LogReporter
v1.5 is available
In
response to some feedback from Santiago Zapata, I have updated the
LogReporter.c code to enumerate and report on all active MAC and IP
addresses. Irrespective of the size of your Windows
environment,
you probably struggle with mapping actions in your
firewalls or IDS logs back to users. Stick this program in
your
login scripts and it will provide syslog records for each
login
including NETBIOS computer name, username as well as all active MAC and
IP addresses.
2010-03-19 Mining A/V logs continues to extract gold
After updating my
simple Symantec A/V log parser
I used it to convert syslog Symantec A/V logs to CSV files and loaded
the data into Advizor
Analyst. This type of graph shows interesting re-infection
patterns for individual hosts (horizontal lines), signature updates
following malware blooms (vertical patterns with the same colors) as
well as others.

The y-axis is a list of all infected machines so each horizontal line
is a single system (Host names clipped for anonymity). The color coding
is based on the name of the malware with similar names having similar
colors on the pallet. Analysis of the four solid verticals outside of
the weekly schedule scan pattern (the consistent vertical pattern
across all the plots) were four different outbreaks of a network
scanner where signature updates were loaded across all systems and the
IPS started detecting and blocking immediately. The analysis was done
to evaluate the effectiveness of an A/V deployment. The initial impact
was a clear determination that the A/V system needed some attention and
over time, the analysis was used to re-enforce the value of enabling
additional options in the A/V system. Ongoing analysis shows the tempo
of malware detects and changes to the A/V environment.
2009-10-13 LogReporter
v1.4 is available
I
needed to add support for unicode in my simple login tracker.
While poking around in the source, I added a few more
features to
make is a bit easier to use. If you have a small, medium or
large
Windows environment, you probably struggle with mapping actions in your
firewalls or IDS logs back to users. Stick this program in
your
login scripts and it will provide syslog records for each
login
including NETBIOS computer name, username, MAC address and IP.
The new version does a better job with long and unicode
netbios
names and allows you to specify your loghost by name or IP address.
2009-09-21 A/V logs can help you find troubled
systems
I
was culling through the logs on one of my systems the other day and
realized that I was getting a fair amount of alerts from my Symantec
A/V servers. At first, I was not interested in what malware
was
being detected and cleaned but it got me thinking about what
interesting patterns existed. I suspected that the majority
of
malware infections were caused by a minority of users as most malware
these days require some user action. To test this theory I
wrote
a simple parser
to convert the logs to something that I could push into
a visualizer
and started looking for interesting patterns.

Above
is a histogram plotting A/V detects over time. Each dot is an
piece of malware color coded by host. Horizontal patterns are
a
large quantity of the same piece of malware and vertical lines show
patterns in the A/V detections indicating a schedule for scanning.
This was helpful in deducing the infection and detection
patterns
but not very useful for mapping infections to individual hosts.

This heat map is much more interesting as it shows that a small number
of systems have a disproportionate
number of detected infections. About 50 systems have more
than
3,000 detected pieces of malware while the rest average just two.
This gives the admin teams a short list of systems that they
can
focus on both with technical as well as awareness based remediation.
2009-05-21 I just switched from air to liquid cooling
After
many years of dreading summer and the system over temp lock-ups I just
made the leap into liquid cooling. I had resisted for the
last
couple of years because the cost of entry in money and time was just
too much. After a couple of days to reading on the net I
decided
that it was too simple and cheap, that waiting any longer was silly.

So
far, I am running 32c on my CPU and 35c on both of my GPUs on fan speed
4 of 10. This is not bad considering ambient is 46c and my
CPU
averaged around 50c on air. I will play with this for a
couple
of weeks while I over clock this and that. Once I have
gathered
more data, I will switch from a serial to a parallel flow configuration
and see if that makes any significant difference.
After running the Intel
over clocking utility and installing 3DMark I have a
snapshot of what my new performance is with little tweaking.

2009-04-07 QuickParser
(quickparser) v0.4 released
I
just posted an updated version of QuickParser to SourceForge.
There are some minor bug fixes and changes to the parser to
better support generic logs with key=value pairs.
2008-12-27 Projects on my short list
Of
the long list of projects that I am ignoring most of the time and
banging on when I have a free moment, there are a few that I am putting
on my resolution list to get finished in 2009!
- Log tokenizer, compressor and decompressor
- PDF carver (pdfcarver)
- Network ACL Builder (wirespy)
- IM Sniffer (imspy)
- Forensic packet archiver (The
Wiretapper's Toolkit - TWT)
- DNS Sniffer (pdnsd)
There are also a few ideas that I need to flesh out on paper in 2009
(we shall see how I do).
- "Distrust Engineering", finding the bad guys without
signatures.
- "The State of Information Security Data
Visualization", a Marcus style rant.
- "The
11th Domain of Information Security", how to achieve long term
improvement of the security of your organization by creating a
sustainable information security practice.
2008-08-21 QuickParser
(quickparser) v0.3
In
the spirit of sharing and in the hopes of prodding a co-conspirator
into finishing *his* better, stronger and faster parser, I have
released the source to my regex-less log parser specifically for
Juniper (Netscreen) firewall logs.
2008-07-01 PiRAT
v0.2
I
just upgraded my Nokia N800 to a N810 and it is time to update my tool
chain for OS2008. The new version will sport all of my
favorite
tools including NMAP,
AMAP,
xprobe2,
NBTScan,
NetCat,
Hping2, dsniff,
p0f,
hydra,
John the
Ripper, Snort,
TCPDump,
Metasploit,
Kismet,
Wireshark
(a real pain to build) and many more.
2008-06-19 Transitive Distrust
I have
watched our capability to detect threats degrade year after year as our
adversaries invest more and more time and effort in the pursuit of
stealthiness. As with all arms races, the winner is the faction with
the deepest pockets and lowest overhead. In the corporate
world,
that is a guarantee that the adversaries will always win. I
have
been toying with a different paradigm to identifying threats called
transitive distrust, or as a good friend of mine commented, trust
engineering.
Thesis:
To
test this, I am building with the help of some friends, a system of
instrumentation that applies a simple set of 30-40 rules to all systems
that interact with a given network. Once the rules are
applied, a
trust/distrust map is compiled. This is a very effective
filter
to separate the trusted, and therefore not interesting, from the
untrusted
The system can run
constantly, correcting the evaluated trust/distrust as the data points
change. Distrust
degrades over time so a system that was previously untrusted but no
longer exhibits these traits will become more trusted.
2008-05-31 Monitoring and logging removable media
access with OS/X
I wrongly assumed
that it would
be simple to find an intellectual property (IP) leakage monitoring tool
for removable media on OS/X. It is unfortunate that the
abundance
of this type of tool on Windows has not rubbed off on Mac.
That
said, I hacked together a volume monitoring daemon (vmd)
to provide logging of file activity on removable devices on systems
running OS/X. It is the poor mans solution to the problem.
It uses syslog, so it is possible to have all of your Mac's
point
to a central syslog server and gain arms length auditing of removable
media across all of your OS/X based systems with this little daemon.
A word of caution, I used the fsevents functionality of
10.4 and 10.5 which is not a standard hook for applications.
So don't be surprised if this stops working in a future
version of
OS/X.
2008-04-26 Malware detection through data visualization
Raffael over at secvis.org has been
working to improve the overall state of information security data
visualization. Along with logging, data visualization has
been a
pet project of mine for several years. I have, from time to
time
used visualization to filter through large volumes of data looking for
intruders, malware and data breaches.
I have been trying to find a way to go through firewall logs at a large
corporation where a days worth of traffic equates to 25Gb of
uncompressed logs
and mapping portions of the logs to simple 2D graphs helps
to point out obvious and sometimes subtle anomalies.
When you plot the destination IP address as an integer over time, many
interesting patterns are highlighted. Even more interesting than the horizontal patterns indicating
continuous traffic to specific IP addresses are the vertical clusters
with regularly repeating frequencies.
Even more interesting than the horizontal patterns indicating
continuous traffic to specific IP addresses are the vertical clusters
with regularly repeating frequencies.
Next, a plot of the same data using the destination port number over
time points to obvious port scanning in the form of diagonal
lines as well as odd patterns that sync with the previous destination
IP address plot. 
The last plot of source ports over time points to crafted packets.
Normal sockets allocated through the operating system will
have
positively incrementing source ports for each new connection.
Look for the horizontal lines and you have most likely found
tools
that are not using the operating system to instantiate new sockets.
To me, this screams packet crafting. 
All of these graphs were created by parsing firewalls logs using a perl script and
loading them into Advizor
Analyst.
Web server logs are another source of interesting data if you are able
to separate the wheat from the chaff. Apache2Dot.pl
is a small script that makes clear diagrams of website interactions.
2008-03-19 Sumo
vs. Judo
Over the course of my
career, it has become clear to me that Japan's national
sport offers a perfect analogy for the current state of
information security.

2008-03-18 Is it time for Computer Access
License Agreements?

Now that the US Federal Government is regularly seizing, coping and
snooping into the computers of US Citizens returning home, what can we
do to protect the privacy that we hold dear? The most obvious
response is to encrypt your drives using whatever tools you deem
appropriate. I had considered a "FiST
US Customs" campaign, but I suppose that would not be very
professional. I had also considered implementing some
anti-forensic countermeasures on my computers. A simple
change to
one of the many open source disk wipers could fill your unallocated and
slack space with billions of partial GIF
images. That sure would make going through the preview in EnCASE a bit more
tedious. And I suppose there are even more 'active'
countermeasures available to those who are not squeamish about fighting
back. After all, I have nothing to hide, and its not my job
to
make it easy for Law Enforcement to do theirs. Then it
occurred
to me as I was ranting to a fellow infosec practitioner. What
we
need is the equivalent of a EULA for our computers. Something
that warns off would-be snoopers who decide to look at our computers
without a warrant. I suppose putting one of these stickers on
your computer and your hard drives is just asking for them to be
confiscated, never to be seen again. But it sure would make a
great story.
2008-03-14 DPS for life!






Distance makes the
heart grow fonder.
2008-01-24 Passive syslog monitor v1.2.1 (psmd) has been
released
After many days of
pushing
hundreds of gigabytes of data through it, the new version of psmd
offers many bug fixes and a new TCP reassembler which notes lost log
data due to dropped packets. Along with the new features,
psmd
still offers many others:
- Passive syslog monitoring (no listening ports)
- Support for syslog over UDP and TCP (syslog-ng)
- Archiving of all log data with proper time stamps,
source and dest MAC and IP address
- MD5 and SHA1 hashing of all archived logs
- Forwarding of syslog data with or without forged
source IP addresses
- TIMEMARK insertion to handle time zone and time skew
issues
2007-09-25 Sending a shout out to my com padre
Further continuing
the South
Park theme, I bring you yet another image of a fellow student of Sun
Tsu and InfoSec practitioner. Can you guess who it is?

I just want to know one thing, where is my cut of the shirt
action Tom?
2007-09-22 Regexless log parsing (quickparser)
A co-conspirator
and I have been
building some log analysis tools. To feed data to the tools,
we
needed to convert log files into a pseudo XML format. I built
a
couple of regex log parsers in perl but they were very slow.
We
have spent some time talking about other ways of parsing logs and I
cannibalized a log compression tool that I had built using regexless
parsing and found out that it is pretty fast. By fast I am
talking 2.6M lines per minute on a single processor 2.5GHz PC running
linux and 950K lines per minute on a SunBlade 2000 with 1GHz processors.
Check out my quickparser,
it chews up syslog data from Netscreen firewalls. It should
work
properly with any syslog source that uses key/value pairs separated by
a '='.
2007-08-17 "Better out than in, that's what
I always say!" -Shrek
InfoSec is from
Pluto, NetOps is from Jupiter
As
the tenth largest body orbiting our sun, Pluto has in recent years been
center stage to heated discussion about what makes a planet.
Living on
Pluto as it spins around its eccentric orbit at a chilly 29 AU to a
really chilly 49 AU from our Sun would be quite a challenge.
It's cold
and lonely and most people don't even consider Pluto a planet including
the IAU which on August 24th, 2006 relegated Pluto to 'dwarf planet'
status. It is surprisingly similar to the life as an InfoSec
professional. They are center stage to heated discussions
about the
significance, priority and impact of information security on
organizations. Aside from government and financial circles,
InfoSec is
at best an ugly stepchild and at worst is the bastard child of an
adulterous relationship. To the rest of the world, information security
is the curse of 'due diligence and care' that is resisted, ignored and
hated with vim and vigor likened to paying taxes. In short,
information security is the group that tries to make organizations do
silly things that cost too much and delay projects for no good reason
because "security breaches only happen to the other guy, not us".
The fifth planet from our Sun, Jupiter, stacks up as the
largest body in our solar system at 2 ½ times more massive
that all the
other planets put together. Jupiter keeps showing up in the
press with
missions like Voyager, Cassini and Galileo. If that
was not enough of
a spotlight, consider the Shoemaker-Levy 9 Impacts in July of
1994.
Jupiter is big, bright and full of hydrogen. Everybody knows
what
Jupiter looks like and we thank Jupiter for its gravitational pull, we
all prefer to have things hit Jupiter instead of us. Network
operations, like Jupiter, gets lots of visibility, is generally large
in comparison to other operational bodies and is full of an amazingly
diverse class of gases. And we all know to make a bee-line to
NetOps
when we can't surf the Internet.
Putting aside the above analogies, there are some fundamental
differences between InfoSec and NetOps and over the years I have
struggled to understand those differences as a way to improve my
interactions with my family on Jupiter. At its most
fundamental level,
the difference between "network" people and "security" people is that
one is focused on ensuring that packets move and the other
isn't. I
will leave ascribing the correct labels to you, the reader.
This fundamental schism is surprisingly wide and deep. And,
we are talking astronomic units (AU) here, not Grand Canyon
distances.
Countless times, I have gone to my brothers and sisters on Jupiter
asking for help in reducing the 'attack surface' of a problem and time
and time again, I have received feedback and lumps. With each
tongue-lashing and stroke I have heard "We don't have time or
resources". For a long time, I assumed that part of my family
was just
lazy.
The Epiphany came to me last week, NetOps is from Jupiter, not
my home town over on Pluto. When I ask network operations to
install
an ACL or firewall, they resist. Not out of laziness but as
an
instinctive response built into the very fabric of each resident of
Jupiter. Asking to block traffic is like asking them to move
to Pluto,
which is far too small and cold. When I look at the problem,
I see it
through the eyes of a happy resident of Pluto where blocking traffic is
just a matter of simple changes to router and firewall
configurations.
Add in a little audit trail and some monitoring for giggles, and it is
a happy place for all. But when someone from Jupiter looks at
preventing packets from reaching their final destination, it is like
preventing a packet from reaching it's pre-ordained and rightful place
in the universe and the ramifications will topple everything.
Not to
mention making a mess in the holiest of places, the change control
archive.
So, consider this, the next time you endeavor to make the
journey from Pluto to Jupiter to request a packet filter, start the
conversation with "Every packet is sacred", and bring lots of photos of
home to reassure them that Pluto is not all bad, because a network
operator who turns up a firewall is actually a Plutonian on vacation in
a warmer climate.
Ron Dilley
:Plutonian
2007-07-31 Blatant C.a.S.E.
I am sorry Marcus, I just can't keep it to myself . . .

2007-07-30 Passive syslog monitor v1.0 (psmd) has been
released
Thanks to mjr for suggesting an interesting solution to the problem of
how to handle broken time in logs. By broken I mean logs from
systems without accurate time, mixed time zones and the most annoying
of all . . . daylight savings. The new version of psmd
inserts
time marks which record the time skew between log time and the time
that the log is sucked off the wire.
2007-03-22 Yet another project (PiRat)
I just picked up a Nokia
N800
with the intent to port all of my InfoSec related tools to this
ultra-small computing platform. There is a pretty well put
together development environment and a strong open source development
community branded as Maemo.
2006-09-25 ÜberAdmin has a new website
After several years of a really plain website, I decided to give up
using vi for web development and switched to a more modern tool which
was capable of making really fancy websites. Though I opted
not
to make this site much fancier than the vi version, I at least used
more than one font this time.
2006-09-18 Passive syslog monitor daemon has a new home
at SourceForge (psmd)
After tweaking on my code an hour at a time over the last year, I have
finally been pushed and prodded enough to actually release it to the
public. As I am not a programmer by trade and know just how
much
gum and how many rubber bands are used to hold it together, I do so
with a bit of reservation. With all the messages on the logs
mailing list about signing syslog, what else could I do?
2018-12-10 Log Pseudo Indexer(logpi) v0.6 has been released!
Searching through a large dataset was taking too long, so I updated and released a small utility
that will index addresses in arbitrary formatted text data. Once a pseudo index has been generated,
finding interesting data is pretty quick. Very helpful when you want to find the bad guys.
2018-01-03 Wirespy(wsd) v0.6 has been released!
I spent some time over the holiday to finish the new version of wirespy. It now supports
off-line mode using PCAP files, logs more metadata including TCP flows and can save
flow state across executions.
2016-07-06 Difftree(dt) v0.5.8 made it into a trade journal!
Difftree earned 5 stars in Linux Pro Magazine's July issue #188 with a nice quote "Difftree is convincing due to its speed, flexibility,
and simple operation. Numerous examples on the project
site and man page help out with the first steps."

* Image included with permission from linuxpromagazine.com
2016-03-27 PDF Carver(pdfcarve) v0.7 has been released
I had a need to extract a malicious binary from a PDF file at CanSecWest this year and was inspired to
dust off my PDF carving code and fix some bugs.
2015-12-29 Difftree(dt) v0.5.8 has been released
I just finished updating difftree to play nicely with ATIME and to report on changes. This come in handy
when you need to see when a file was accessed across a series of time periods. Run difftree every day and
it is simple to see what has happened in a directory tree over time.
2015-08-23 Difftree(dt) has moved from SourceForge to GitHub
I have started moving the many of my projects that could benifit from more community involvement to GitHub. Difftree is the second project to make the trek and I can't wait to see how it improves over time!
2015-08-23 Log Templater (tmpltr) has moved from SourceForge to GitHub
After being forced to use GitHub to help port passivedns to OpenBSD, it is clear that GitHub is far better
than SourceForge.
2015-07-26 Freshening The Wiretappers Toolkit (TWT)
I have been modernizing The Wiretappers Toolkit (TWT)
and just finished standing up a new packet vacuum for my home office. CappuccinoPC makes a nice small form factor fanless machine.
The machine includes an Atom D525, 4Gb Ram, 4xUSB, 4x1Gb Ethernet, RS232 and room for one 2.5" HDD:

I added a 2TB HDD for $110 and an extra external heat-sink for $8. Out the door for $440.
2014-12-03 Selling Packet Vacuums Door-to-Door
Thanks to the IANS Faculty for inviting me to speak
about my second most favorite incident response tool (Packet Vacuums)!
2014-09-18 Enough with the BSoD!
I gave up in frustration at
my Intel Extreme MB
with the BSoD, hangs, thermal events
and on and on. So, time for an upgrade! I switched to an ASUS
Rampage Black Edition. Along with the
MB, CPU and
Ram,
I upgraded my SDD
and HDD configuration.
Boot speed times are as follows:.
2
x 500Gb Samsung 840 EVO SSD (Raid-0)
Sample
1
Sample
2
Sample
3
Average
Boot to Login
27.70 sec
25.80 sec
27.00 sec
26.30 sec
Login to Desktop
3.40 sec
2.50 sec
2.70 sec
2.70 sec
Login to
Chrome Open/Page Loaded
4.50 sec
4.10 sec
4.10 sec
4.20 sec
Now the really important thing is how does this new computer run for gaming? Well, here is the benchmark for
the default motherboard confuguration (no overclocking):

The 2 x RAID-0 Samsung SSD performed much better than the 4 x RAID-0 drives I had previously used:

An additional surprise was how well the 4 x RAID-5 Samsung 2.5" HDD performed:

2013-12-31 Log Templater (tmpltr) v0.6 is now available
I have been laying some ground work for implementing log chain templates in the next version of Log Templater.
Part of that work includes adding support for more field types (IPv4, IPv6, MAC Address and HEX numbers).
These changes clean up the templates and make it simpler and faster to find some key data when responding to
a threat.
2013-04-03 Geeking out with Marcus Ranum - Take 2
My last session
with Marcus in February may have lacked "Marcus", but there was enough participation and positive feedback that he
asked me to come back and have a more detailed discussion. This time, we had a chance to dig much deeper into the topic and
came up with a couple of interesting ideas that we are now percolating on. Perhaps this will lead to a new tool in our kit.
The webcast is available and who knows what may come next.
2013-02-19 Geeking out with Marcus Ranum
I was looking forward to spending some quality
geek out
time with Marcus today talking about logging
and log analysis. Unfortunately, Marcus fell victim to the Webcast gremlins at a hotel in Germany and
was not able to join me. I still had a good time talking with Allan
about all things "logging" but I am looking forward to geeking our with Marcus some other time.
The webcast has been posted along with some takeaways.
2013-01-20 Hosting ISOI 11
I had the honor and privilege of hosting ISOI 11 in January.
There was an amazing array of speakers and topics. I can't wait for ISOI 12!
Special thanks to Dragos for the use of the secure WiFi gear.
2012-06-27 Upgraded GPU Cracker
With the recent breaches of authentication credentials around the Interwebs, I decided to upgrade my GPU
Cracker and see how it performs and how hot my office can get all at the same time. I replaced my aging
Radeon 5xxx boards with three Radeon 7970's
and one Radeon 6970. SHA1 is now running at almost 6T computations
per second using oclHashCat-Plus.
Time to port Nightengale (BaraCUDA) to OpenCL and see how she runs!

2012-02-04 Passive Proxy Daemon (pproxyd) v0.2 is now available
I have been procrastinating about building a libpcap based sniffer that reassembles web traffic and
generates Squid proxy logs for years.
I tried to use Mike Poor's "development via osmosis" trick with a couple of buddies but in the end, I was forced
to put it together in the last couple of weeks to help solve a vexing web application problem. So, in a pinch,
I pulled out the paper clips, rubber bands and chewing gum. Then I read the docs on libnids.
2012-01-17 Log Templater (tmpltr) v0.5 is now available
After some very helpful and specific feedback about the last version of tmpltr, I have added a few additions
including faux clustering for the occasion when it is handy to know what on a given log line has not changed.
There is a performance penalty for this extra processing, but not as much as I had originally expected. The
table below shows average performance metrics on a Linux VM running on an i7 @ 3.2GHz.
Log size and type
Avg. Line Len
Avg. Arg Count
Args Stored
Avg. Lines per Min
18M Line Cisco FW Log
180
32
0
12,004,023/min
18M Line Cisco FW Log (Clustered)
180
32
24,009
4,093,802/Min
11M Line Apache Access Log
246
44
0
9,453,905/Min
11M Line Apache Access Log (Clustered)
246
44
21,666
5,563,009/Min
4M Line Windows Event Log
793
90
0
2,854,123/Min
4M Line Windows Event Log (Clustered)
793
90
70,361
1,183,226/Min
In addition, I have added a greedy mode where the templater will ignore double quotes. This is very useful
when processing web server logs. In non-greedy mode, tmpltr will assume most things in between a pair of double
quotes are a single string. In greedy mode, all data will be handled the same.
2011-10-17 SSD-Spindle Hybrid
I picked up a couple of Seagate MomentusXT 500Gb
Solid State Hybrid drives to see how they stacked up to
my four 120Gb SSDs running RAID-0. I pulled out the very handy HD TunePro and
the sad fact is, configured as a RAID-0, they were no where near as fast as the pure SSD RAID-0. The linear read and the seek speed was also unpredictable.
Even worse, they did not out perform a couple of 1TB spindle drives running RAID-0 as the chart below shows.

2011-10-01 Log Templater (tmpltr) v0.3 is now available
During the last security incident that I worked on, I needed to grind through 20gb of log files looking
for any odd log lines that would indicate the point where the bad guys got in. If I had done it manually,
I would still be looking at log data. Instead, I built a tool that converted logs into pattern
templates and looked for templates that I had never seen before. This allowed me to zero in on just a
few hundred log lines out of all the data.
2011-07-29 Quick Parser (quickparser) v0.5 is now available
After re-implementing some parser code in difftree with bug
fixes and improved bounds checking, I have ported those changes back to this tool. So, I now present
the new and improved quick parser with less bugs and more bounds checking. Re-energized after touching
the code, I am working on the template based version, which will not be limited to syslog style,
key=value formatted logs.
2011-07-27 Directory Tree Differ (difftree) v0.5 is now available
I have released a new version of difftree with more features and less memory leaks.
This new version adds the ability to save directory tree state and to compare both
directories and archives of directory trees that were previously saved. In addition,
you can hash and compare files if accuracy is more important the speed.
2011-07-16 Directory Tree Differ (difftree) v0.4 is now available
While working on a security incident and fighting with tripwire and Osiris,
I gave up and wrote a fast directory diff tool to allow me to do simple
comparisons between SAN snapshots. To tool was so handy for me, I
figured I would share it.
2011-07-03 SSD Redux
After
fighting with the RAID chassis that I picked up to house my new clutch
of SSD drives I returned them all in a fit of nerd rage and downgraded
from a RAID enclosure to a simple JBOD and larger SSD drives.
I have not been disappointed:
4 x
120Gb OCZ SSD (Raid-0)
Sample
1
Sample
2
Sample
3
Average
Boot to Login
27.30 sec
27.50 sec
27.28 sec
27.28 sec
Login to Desktop
3.50 sec
3.10 sec
3.60 sec
3.40 sec
Login to
Firefox Open/Page Loaded
6.90 sec
5.40 sec
6.05 sec
6.12 sec
Using the very handy HD TunePro
utility, I was able to get a bit more imperial data about the
difference in performance between my old configuration and the new SSD
smoke-fest. Here is the read throughput and access time graph
for
the 4x120Gb OCZ Vertex II SSD (Raid-0):

That
may not look too impressive, but if you compare it to the same read
throughput and access time graph for my old 2x1Tb 7200RPM SATA II HDD
(Raid-0) configuration you will see a bit of a difference and why my
grin is from ear to ear:

2011-05-21 Power supply failure leads to faster boot
times
In
the spirit of tricking people into reading what I write, I have given
in to temptation and deliberately misled you. Yes, my old
power
supply on my Windows development system died and I was forced to
replace it today. In addition, I have improved my boot times
considerably. But the only correlation between the two is
that I
figured I would do a bit of upgrading while I had my case open to
replace the power supply. So, out with the old 850W and in
with
the new 1200W Thermaltake. Additionally, out
with the old 2 x 1TB Raid-0 boot drives and in with the new 4 x 64GB Raid-0 SSD. All
this "high speed, low drag" boot hotness in a fancy 5 1/4" chassis by Patriot. Boot
speed times are as follows:.
2
x 1TB 7200RPM HDD (Raid-0)
Sample
1
Sample
2
Sample
3
Average
Boot to Login
58.00 sec
87.80 sec
87.80 sec
77.87 sec
Login to Desktop
72.50 sec
51.40 sec
32.10 sec
52.00 sec
Login to
Firefox Open/Page Loaded
78.70 sec
63.80 sec
69.80 sec
70.77 sec
4
x 64Gb Patriot TRB SSD (Raid-0)
Sample
1
Sample
2
Sample
3
Average
Boot to Login
32.60 sec
29.40 sec
26.70 sec
29.57 sec
Login to Desktop
5.20 sec
3.40 sec
4.40 sec
4.33 sec
Login to
Firefox Open/Page Loaded
8.30 sec
6.20 sec
6.90 sec
7.13 sec

2010-11-24 Generate password lists using Markov
chains
In
preparation for adding additional password plaintext generators to my GPU password cracker,
I prototyped a simple Markov chain plaintext generator (pwMarkov.pl).
I added it to my John scripts for good measure and am testing
to
see if there is a measurable improvement in cracking efforts now.
2010-05-18 Say goodbye to my liquid cooling system
After
my second coolant leak, it was time to remove my liquid cooling system.
It worked really well at keeping my system cool. It
was not
as effective at keeping it dry. It would not have been as
annoying if I did not have an air cooled system running two dual GPU
graphics cards and a Tesla super computer sitting under my desk at the
same time. My GPU password cracking box just hummed along
without
any overheating issues while my game system learned how to swim in low
conductivity cooling solution. So, I upgraded my case to an
Antec
1200 to match my GPU cracker and replaced my pair of ATI
4895's
with two ATI 5970's and I am back to the races. The 3DMark
numbers speak wonders about both the video cards and the difference
between running Windows XP and Windows 7.

2010-05-12 LogReporter
v1.5 is available
In
response to some feedback from Santiago Zapata, I have updated the
LogReporter.c code to enumerate and report on all active MAC and IP
addresses. Irrespective of the size of your Windows
environment,
you probably struggle with mapping actions in your
firewalls or IDS logs back to users. Stick this program in
your
login scripts and it will provide syslog records for each
login
including NETBIOS computer name, username as well as all active MAC and
IP addresses.
2010-03-19 Mining A/V logs continues to extract gold
After updating my
simple Symantec A/V log parser
I used it to convert syslog Symantec A/V logs to CSV files and loaded
the data into Advizor
Analyst. This type of graph shows interesting re-infection
patterns for individual hosts (horizontal lines), signature updates
following malware blooms (vertical patterns with the same colors) as
well as others.

The y-axis is a list of all infected machines so each horizontal line
is a single system (Host names clipped for anonymity). The color coding
is based on the name of the malware with similar names having similar
colors on the pallet. Analysis of the four solid verticals outside of
the weekly schedule scan pattern (the consistent vertical pattern
across all the plots) were four different outbreaks of a network
scanner where signature updates were loaded across all systems and the
IPS started detecting and blocking immediately. The analysis was done
to evaluate the effectiveness of an A/V deployment. The initial impact
was a clear determination that the A/V system needed some attention and
over time, the analysis was used to re-enforce the value of enabling
additional options in the A/V system. Ongoing analysis shows the tempo
of malware detects and changes to the A/V environment.
2009-10-13 LogReporter
v1.4 is available
I
needed to add support for unicode in my simple login tracker.
While poking around in the source, I added a few more
features to
make is a bit easier to use. If you have a small, medium or
large
Windows environment, you probably struggle with mapping actions in your
firewalls or IDS logs back to users. Stick this program in
your
login scripts and it will provide syslog records for each
login
including NETBIOS computer name, username, MAC address and IP.
The new version does a better job with long and unicode
netbios
names and allows you to specify your loghost by name or IP address.
2009-09-21 A/V logs can help you find troubled
systems
I
was culling through the logs on one of my systems the other day and
realized that I was getting a fair amount of alerts from my Symantec
A/V servers. At first, I was not interested in what malware
was
being detected and cleaned but it got me thinking about what
interesting patterns existed. I suspected that the majority
of
malware infections were caused by a minority of users as most malware
these days require some user action. To test this theory I
wrote
a simple parser
to convert the logs to something that I could push into
a visualizer
and started looking for interesting patterns.

Above
is a histogram plotting A/V detects over time. Each dot is an
piece of malware color coded by host. Horizontal patterns are
a
large quantity of the same piece of malware and vertical lines show
patterns in the A/V detections indicating a schedule for scanning.
This was helpful in deducing the infection and detection
patterns
but not very useful for mapping infections to individual hosts.

This heat map is much more interesting as it shows that a small number
of systems have a disproportionate
number of detected infections. About 50 systems have more
than
3,000 detected pieces of malware while the rest average just two.
This gives the admin teams a short list of systems that they
can
focus on both with technical as well as awareness based remediation.
2009-05-21 I just switched from air to liquid cooling
After
many years of dreading summer and the system over temp lock-ups I just
made the leap into liquid cooling. I had resisted for the
last
couple of years because the cost of entry in money and time was just
too much. After a couple of days to reading on the net I
decided
that it was too simple and cheap, that waiting any longer was silly.

So
far, I am running 32c on my CPU and 35c on both of my GPUs on fan speed
4 of 10. This is not bad considering ambient is 46c and my
CPU
averaged around 50c on air. I will play with this for a
couple
of weeks while I over clock this and that. Once I have
gathered
more data, I will switch from a serial to a parallel flow configuration
and see if that makes any significant difference.
After running the Intel
over clocking utility and installing 3DMark I have a
snapshot of what my new performance is with little tweaking.

2009-04-07 QuickParser
(quickparser) v0.4 released
I
just posted an updated version of QuickParser to SourceForge.
There are some minor bug fixes and changes to the parser to
better support generic logs with key=value pairs.
2008-12-27 Projects on my short list
Of
the long list of projects that I am ignoring most of the time and
banging on when I have a free moment, there are a few that I am putting
on my resolution list to get finished in 2009!
- Log tokenizer, compressor and decompressor
- PDF carver (pdfcarver)
- Network ACL Builder (wirespy)
- IM Sniffer (imspy)
- Forensic packet archiver (The
Wiretapper's Toolkit - TWT)
- DNS Sniffer (pdnsd)
There are also a few ideas that I need to flesh out on paper in 2009
(we shall see how I do).
- "Distrust Engineering", finding the bad guys without
signatures.
- "The State of Information Security Data
Visualization", a Marcus style rant.
- "The
11th Domain of Information Security", how to achieve long term
improvement of the security of your organization by creating a
sustainable information security practice.
2008-08-21 QuickParser
(quickparser) v0.3
In
the spirit of sharing and in the hopes of prodding a co-conspirator
into finishing *his* better, stronger and faster parser, I have
released the source to my regex-less log parser specifically for
Juniper (Netscreen) firewall logs.
2008-07-01 PiRAT
v0.2
I
just upgraded my Nokia N800 to a N810 and it is time to update my tool
chain for OS2008. The new version will sport all of my
favorite
tools including NMAP,
AMAP,
xprobe2,
NBTScan,
NetCat,
Hping2, dsniff,
p0f,
hydra,
John the
Ripper, Snort,
TCPDump,
Metasploit,
Kismet,
Wireshark
(a real pain to build) and many more.
2008-06-19 Transitive Distrust
I have
watched our capability to detect threats degrade year after year as our
adversaries invest more and more time and effort in the pursuit of
stealthiness. As with all arms races, the winner is the faction with
the deepest pockets and lowest overhead. In the corporate
world,
that is a guarantee that the adversaries will always win. I
have
been toying with a different paradigm to identifying threats called
transitive distrust, or as a good friend of mine commented, trust
engineering.
Thesis:
To
test this, I am building with the help of some friends, a system of
instrumentation that applies a simple set of 30-40 rules to all systems
that interact with a given network. Once the rules are
applied, a
trust/distrust map is compiled. This is a very effective
filter
to separate the trusted, and therefore not interesting, from the
untrusted
The system can run
constantly, correcting the evaluated trust/distrust as the data points
change. Distrust
degrades over time so a system that was previously untrusted but no
longer exhibits these traits will become more trusted.
2008-05-31 Monitoring and logging removable media
access with OS/X
I wrongly assumed
that it would
be simple to find an intellectual property (IP) leakage monitoring tool
for removable media on OS/X. It is unfortunate that the
abundance
of this type of tool on Windows has not rubbed off on Mac.
That
said, I hacked together a volume monitoring daemon (vmd)
to provide logging of file activity on removable devices on systems
running OS/X. It is the poor mans solution to the problem.
It uses syslog, so it is possible to have all of your Mac's
point
to a central syslog server and gain arms length auditing of removable
media across all of your OS/X based systems with this little daemon.
A word of caution, I used the fsevents functionality of
10.4 and 10.5 which is not a standard hook for applications.
So don't be surprised if this stops working in a future
version of
OS/X.
2008-04-26 Malware detection through data visualization
Raffael over at secvis.org has been
working to improve the overall state of information security data
visualization. Along with logging, data visualization has
been a
pet project of mine for several years. I have, from time to
time
used visualization to filter through large volumes of data looking for
intruders, malware and data breaches.
I have been trying to find a way to go through firewall logs at a large
corporation where a days worth of traffic equates to 25Gb of
uncompressed logs
and mapping portions of the logs to simple 2D graphs helps
to point out obvious and sometimes subtle anomalies.
When you plot the destination IP address as an integer over time, many
interesting patterns are highlighted. Even more interesting than the horizontal patterns indicating
continuous traffic to specific IP addresses are the vertical clusters
with regularly repeating frequencies.
Even more interesting than the horizontal patterns indicating
continuous traffic to specific IP addresses are the vertical clusters
with regularly repeating frequencies.
Next, a plot of the same data using the destination port number over
time points to obvious port scanning in the form of diagonal
lines as well as odd patterns that sync with the previous destination
IP address plot. 
The last plot of source ports over time points to crafted packets.
Normal sockets allocated through the operating system will
have
positively incrementing source ports for each new connection.
Look for the horizontal lines and you have most likely found
tools
that are not using the operating system to instantiate new sockets.
To me, this screams packet crafting. 
All of these graphs were created by parsing firewalls logs using a perl script and
loading them into Advizor
Analyst.
Web server logs are another source of interesting data if you are able
to separate the wheat from the chaff. Apache2Dot.pl
is a small script that makes clear diagrams of website interactions.
2008-03-19 Sumo
vs. Judo
Over the course of my
career, it has become clear to me that Japan's national
sport offers a perfect analogy for the current state of
information security.

2008-03-18 Is it time for Computer Access
License Agreements?

Now that the US Federal Government is regularly seizing, coping and
snooping into the computers of US Citizens returning home, what can we
do to protect the privacy that we hold dear? The most obvious
response is to encrypt your drives using whatever tools you deem
appropriate. I had considered a "FiST
US Customs" campaign, but I suppose that would not be very
professional. I had also considered implementing some
anti-forensic countermeasures on my computers. A simple
change to
one of the many open source disk wipers could fill your unallocated and
slack space with billions of partial GIF
images. That sure would make going through the preview in EnCASE a bit more
tedious. And I suppose there are even more 'active'
countermeasures available to those who are not squeamish about fighting
back. After all, I have nothing to hide, and its not my job
to
make it easy for Law Enforcement to do theirs. Then it
occurred
to me as I was ranting to a fellow infosec practitioner. What
we
need is the equivalent of a EULA for our computers. Something
that warns off would-be snoopers who decide to look at our computers
without a warrant. I suppose putting one of these stickers on
your computer and your hard drives is just asking for them to be
confiscated, never to be seen again. But it sure would make a
great story.
2008-03-14 DPS for life!






Distance makes the
heart grow fonder.
2008-01-24 Passive syslog monitor v1.2.1 (psmd) has been
released
After many days of
pushing
hundreds of gigabytes of data through it, the new version of psmd
offers many bug fixes and a new TCP reassembler which notes lost log
data due to dropped packets. Along with the new features,
psmd
still offers many others:
- Passive syslog monitoring (no listening ports)
- Support for syslog over UDP and TCP (syslog-ng)
- Archiving of all log data with proper time stamps,
source and dest MAC and IP address
- MD5 and SHA1 hashing of all archived logs
- Forwarding of syslog data with or without forged
source IP addresses
- TIMEMARK insertion to handle time zone and time skew
issues
2007-09-25 Sending a shout out to my com padre
Further continuing
the South
Park theme, I bring you yet another image of a fellow student of Sun
Tsu and InfoSec practitioner. Can you guess who it is?

I just want to know one thing, where is my cut of the shirt
action Tom?
2007-09-22 Regexless log parsing (quickparser)
A co-conspirator
and I have been
building some log analysis tools. To feed data to the tools,
we
needed to convert log files into a pseudo XML format. I built
a
couple of regex log parsers in perl but they were very slow.
We
have spent some time talking about other ways of parsing logs and I
cannibalized a log compression tool that I had built using regexless
parsing and found out that it is pretty fast. By fast I am
talking 2.6M lines per minute on a single processor 2.5GHz PC running
linux and 950K lines per minute on a SunBlade 2000 with 1GHz processors.
Check out my quickparser,
it chews up syslog data from Netscreen firewalls. It should
work
properly with any syslog source that uses key/value pairs separated by
a '='.
2007-08-17 "Better out than in, that's what
I always say!" -Shrek
InfoSec is from
Pluto, NetOps is from Jupiter
As
the tenth largest body orbiting our sun, Pluto has in recent years been
center stage to heated discussion about what makes a planet.
Living on
Pluto as it spins around its eccentric orbit at a chilly 29 AU to a
really chilly 49 AU from our Sun would be quite a challenge.
It's cold
and lonely and most people don't even consider Pluto a planet including
the IAU which on August 24th, 2006 relegated Pluto to 'dwarf planet'
status. It is surprisingly similar to the life as an InfoSec
professional. They are center stage to heated discussions
about the
significance, priority and impact of information security on
organizations. Aside from government and financial circles,
InfoSec is
at best an ugly stepchild and at worst is the bastard child of an
adulterous relationship. To the rest of the world, information security
is the curse of 'due diligence and care' that is resisted, ignored and
hated with vim and vigor likened to paying taxes. In short,
information security is the group that tries to make organizations do
silly things that cost too much and delay projects for no good reason
because "security breaches only happen to the other guy, not us".
The fifth planet from our Sun, Jupiter, stacks up as the
largest body in our solar system at 2 ½ times more massive
that all the
other planets put together. Jupiter keeps showing up in the
press with
missions like Voyager, Cassini and Galileo. If that
was not enough of
a spotlight, consider the Shoemaker-Levy 9 Impacts in July of
1994.
Jupiter is big, bright and full of hydrogen. Everybody knows
what
Jupiter looks like and we thank Jupiter for its gravitational pull, we
all prefer to have things hit Jupiter instead of us. Network
operations, like Jupiter, gets lots of visibility, is generally large
in comparison to other operational bodies and is full of an amazingly
diverse class of gases. And we all know to make a bee-line to
NetOps
when we can't surf the Internet.
Putting aside the above analogies, there are some fundamental
differences between InfoSec and NetOps and over the years I have
struggled to understand those differences as a way to improve my
interactions with my family on Jupiter. At its most
fundamental level,
the difference between "network" people and "security" people is that
one is focused on ensuring that packets move and the other
isn't. I
will leave ascribing the correct labels to you, the reader.
This fundamental schism is surprisingly wide and deep. And,
we are talking astronomic units (AU) here, not Grand Canyon
distances.
Countless times, I have gone to my brothers and sisters on Jupiter
asking for help in reducing the 'attack surface' of a problem and time
and time again, I have received feedback and lumps. With each
tongue-lashing and stroke I have heard "We don't have time or
resources". For a long time, I assumed that part of my family
was just
lazy.
The Epiphany came to me last week, NetOps is from Jupiter, not
my home town over on Pluto. When I ask network operations to
install
an ACL or firewall, they resist. Not out of laziness but as
an
instinctive response built into the very fabric of each resident of
Jupiter. Asking to block traffic is like asking them to move
to Pluto,
which is far too small and cold. When I look at the problem,
I see it
through the eyes of a happy resident of Pluto where blocking traffic is
just a matter of simple changes to router and firewall
configurations.
Add in a little audit trail and some monitoring for giggles, and it is
a happy place for all. But when someone from Jupiter looks at
preventing packets from reaching their final destination, it is like
preventing a packet from reaching it's pre-ordained and rightful place
in the universe and the ramifications will topple everything.
Not to
mention making a mess in the holiest of places, the change control
archive.
So, consider this, the next time you endeavor to make the
journey from Pluto to Jupiter to request a packet filter, start the
conversation with "Every packet is sacred", and bring lots of photos of
home to reassure them that Pluto is not all bad, because a network
operator who turns up a firewall is actually a Plutonian on vacation in
a warmer climate.
Ron Dilley
:Plutonian
2007-07-31 Blatant C.a.S.E.
I am sorry Marcus, I just can't keep it to myself . . .

2007-07-30 Passive syslog monitor v1.0 (psmd) has been
released
Thanks to mjr for suggesting an interesting solution to the problem of
how to handle broken time in logs. By broken I mean logs from
systems without accurate time, mixed time zones and the most annoying
of all . . . daylight savings. The new version of psmd
inserts
time marks which record the time skew between log time and the time
that the log is sucked off the wire.
2007-03-22 Yet another project (PiRat)
I just picked up a Nokia
N800
with the intent to port all of my InfoSec related tools to this
ultra-small computing platform. There is a pretty well put
together development environment and a strong open source development
community branded as Maemo.
2006-09-25 ÜberAdmin has a new website
After several years of a really plain website, I decided to give up
using vi for web development and switched to a more modern tool which
was capable of making really fancy websites. Though I opted
not
to make this site much fancier than the vi version, I at least used
more than one font this time.
2006-09-18 Passive syslog monitor daemon has a new home
at SourceForge (psmd)
After tweaking on my code an hour at a time over the last year, I have
finally been pushed and prodded enough to actually release it to the
public. As I am not a programmer by trade and know just how
much
gum and how many rubber bands are used to hold it together, I do so
with a bit of reservation. With all the messages on the logs
mailing list about signing syslog, what else could I do?
2018-01-03 Wirespy(wsd) v0.6 has been released!
I spent some time over the holiday to finish the new version of wirespy. It now supports
off-line mode using PCAP files, logs more metadata including TCP flows and can save
flow state across executions.
2016-07-06 Difftree(dt) v0.5.8 made it into a trade journal!
Difftree earned 5 stars in Linux Pro Magazine's July issue #188 with a nice quote "Difftree is convincing due to its speed, flexibility,
and simple operation. Numerous examples on the project
site and man page help out with the first steps."

* Image included with permission from linuxpromagazine.com
2016-03-27 PDF Carver(pdfcarve) v0.7 has been released
I had a need to extract a malicious binary from a PDF file at CanSecWest this year and was inspired to
dust off my PDF carving code and fix some bugs.
2015-12-29 Difftree(dt) v0.5.8 has been released
I just finished updating difftree to play nicely with ATIME and to report on changes. This come in handy
when you need to see when a file was accessed across a series of time periods. Run difftree every day and
it is simple to see what has happened in a directory tree over time.
2015-08-23 Difftree(dt) has moved from SourceForge to GitHub
I have started moving the many of my projects that could benifit from more community involvement to GitHub. Difftree is the second project to make the trek and I can't wait to see how it improves over time!
2015-08-23 Log Templater (tmpltr) has moved from SourceForge to GitHub
After being forced to use GitHub to help port passivedns to OpenBSD, it is clear that GitHub is far better
than SourceForge.
2015-07-26 Freshening The Wiretappers Toolkit (TWT)
I have been modernizing The Wiretappers Toolkit (TWT)
and just finished standing up a new packet vacuum for my home office. CappuccinoPC makes a nice small form factor fanless machine.
The machine includes an Atom D525, 4Gb Ram, 4xUSB, 4x1Gb Ethernet, RS232 and room for one 2.5" HDD:

I added a 2TB HDD for $110 and an extra external heat-sink for $8. Out the door for $440.
2014-12-03 Selling Packet Vacuums Door-to-Door
Thanks to the IANS Faculty for inviting me to speak
about my second most favorite incident response tool (Packet Vacuums)!
2014-09-18 Enough with the BSoD!
I gave up in frustration at
my Intel Extreme MB
with the BSoD, hangs, thermal events
and on and on. So, time for an upgrade! I switched to an ASUS
Rampage Black Edition. Along with the
MB, CPU and
Ram,
I upgraded my SDD
and HDD configuration.
Boot speed times are as follows:.
2
x 500Gb Samsung 840 EVO SSD (Raid-0)
Sample
1
Sample
2
Sample
3
Average
Boot to Login
27.70 sec
25.80 sec
27.00 sec
26.30 sec
Login to Desktop
3.40 sec
2.50 sec
2.70 sec
2.70 sec
Login to
Chrome Open/Page Loaded
4.50 sec
4.10 sec
4.10 sec
4.20 sec
Now the really important thing is how does this new computer run for gaming? Well, here is the benchmark for
the default motherboard confuguration (no overclocking):

The 2 x RAID-0 Samsung SSD performed much better than the 4 x RAID-0 drives I had previously used:

An additional surprise was how well the 4 x RAID-5 Samsung 2.5" HDD performed:

2013-12-31 Log Templater (tmpltr) v0.6 is now available
I have been laying some ground work for implementing log chain templates in the next version of Log Templater.
Part of that work includes adding support for more field types (IPv4, IPv6, MAC Address and HEX numbers).
These changes clean up the templates and make it simpler and faster to find some key data when responding to
a threat.
2013-04-03 Geeking out with Marcus Ranum - Take 2
My last session
with Marcus in February may have lacked "Marcus", but there was enough participation and positive feedback that he
asked me to come back and have a more detailed discussion. This time, we had a chance to dig much deeper into the topic and
came up with a couple of interesting ideas that we are now percolating on. Perhaps this will lead to a new tool in our kit.
The webcast is available and who knows what may come next.
2013-02-19 Geeking out with Marcus Ranum
I was looking forward to spending some quality
geek out
time with Marcus today talking about logging
and log analysis. Unfortunately, Marcus fell victim to the Webcast gremlins at a hotel in Germany and
was not able to join me. I still had a good time talking with Allan
about all things "logging" but I am looking forward to geeking our with Marcus some other time.
The webcast has been posted along with some takeaways.
2013-01-20 Hosting ISOI 11
I had the honor and privilege of hosting ISOI 11 in January.
There was an amazing array of speakers and topics. I can't wait for ISOI 12!
Special thanks to Dragos for the use of the secure WiFi gear.
2012-06-27 Upgraded GPU Cracker
With the recent breaches of authentication credentials around the Interwebs, I decided to upgrade my GPU
Cracker and see how it performs and how hot my office can get all at the same time. I replaced my aging
Radeon 5xxx boards with three Radeon 7970's
and one Radeon 6970. SHA1 is now running at almost 6T computations
per second using oclHashCat-Plus.
Time to port Nightengale (BaraCUDA) to OpenCL and see how she runs!

2012-02-04 Passive Proxy Daemon (pproxyd) v0.2 is now available
I have been procrastinating about building a libpcap based sniffer that reassembles web traffic and
generates Squid proxy logs for years.
I tried to use Mike Poor's "development via osmosis" trick with a couple of buddies but in the end, I was forced
to put it together in the last couple of weeks to help solve a vexing web application problem. So, in a pinch,
I pulled out the paper clips, rubber bands and chewing gum. Then I read the docs on libnids.
2012-01-17 Log Templater (tmpltr) v0.5 is now available
After some very helpful and specific feedback about the last version of tmpltr, I have added a few additions
including faux clustering for the occasion when it is handy to know what on a given log line has not changed.
There is a performance penalty for this extra processing, but not as much as I had originally expected. The
table below shows average performance metrics on a Linux VM running on an i7 @ 3.2GHz.
Log size and type
Avg. Line Len
Avg. Arg Count
Args Stored
Avg. Lines per Min
18M Line Cisco FW Log
180
32
0
12,004,023/min
18M Line Cisco FW Log (Clustered)
180
32
24,009
4,093,802/Min
11M Line Apache Access Log
246
44
0
9,453,905/Min
11M Line Apache Access Log (Clustered)
246
44
21,666
5,563,009/Min
4M Line Windows Event Log
793
90
0
2,854,123/Min
4M Line Windows Event Log (Clustered)
793
90
70,361
1,183,226/Min
In addition, I have added a greedy mode where the templater will ignore double quotes. This is very useful
when processing web server logs. In non-greedy mode, tmpltr will assume most things in between a pair of double
quotes are a single string. In greedy mode, all data will be handled the same.
2011-10-17 SSD-Spindle Hybrid
I picked up a couple of Seagate MomentusXT 500Gb
Solid State Hybrid drives to see how they stacked up to
my four 120Gb SSDs running RAID-0. I pulled out the very handy HD TunePro and
the sad fact is, configured as a RAID-0, they were no where near as fast as the pure SSD RAID-0. The linear read and the seek speed was also unpredictable.
Even worse, they did not out perform a couple of 1TB spindle drives running RAID-0 as the chart below shows.

2011-10-01 Log Templater (tmpltr) v0.3 is now available
During the last security incident that I worked on, I needed to grind through 20gb of log files looking
for any odd log lines that would indicate the point where the bad guys got in. If I had done it manually,
I would still be looking at log data. Instead, I built a tool that converted logs into pattern
templates and looked for templates that I had never seen before. This allowed me to zero in on just a
few hundred log lines out of all the data.
2011-07-29 Quick Parser (quickparser) v0.5 is now available
After re-implementing some parser code in difftree with bug
fixes and improved bounds checking, I have ported those changes back to this tool. So, I now present
the new and improved quick parser with less bugs and more bounds checking. Re-energized after touching
the code, I am working on the template based version, which will not be limited to syslog style,
key=value formatted logs.
2011-07-27 Directory Tree Differ (difftree) v0.5 is now available
I have released a new version of difftree with more features and less memory leaks.
This new version adds the ability to save directory tree state and to compare both
directories and archives of directory trees that were previously saved. In addition,
you can hash and compare files if accuracy is more important the speed.
2011-07-16 Directory Tree Differ (difftree) v0.4 is now available
While working on a security incident and fighting with tripwire and Osiris,
I gave up and wrote a fast directory diff tool to allow me to do simple
comparisons between SAN snapshots. To tool was so handy for me, I
figured I would share it.
2011-07-03 SSD Redux
After
fighting with the RAID chassis that I picked up to house my new clutch
of SSD drives I returned them all in a fit of nerd rage and downgraded
from a RAID enclosure to a simple JBOD and larger SSD drives.
I have not been disappointed:
4 x
120Gb OCZ SSD (Raid-0)
Sample
1
Sample
2
Sample
3
Average
Boot to Login
27.30 sec
27.50 sec
27.28 sec
27.28 sec
Login to Desktop
3.50 sec
3.10 sec
3.60 sec
3.40 sec
Login to
Firefox Open/Page Loaded
6.90 sec
5.40 sec
6.05 sec
6.12 sec
Using the very handy HD TunePro
utility, I was able to get a bit more imperial data about the
difference in performance between my old configuration and the new SSD
smoke-fest. Here is the read throughput and access time graph
for
the 4x120Gb OCZ Vertex II SSD (Raid-0):

That
may not look too impressive, but if you compare it to the same read
throughput and access time graph for my old 2x1Tb 7200RPM SATA II HDD
(Raid-0) configuration you will see a bit of a difference and why my
grin is from ear to ear:

2011-05-21 Power supply failure leads to faster boot
times
In
the spirit of tricking people into reading what I write, I have given
in to temptation and deliberately misled you. Yes, my old
power
supply on my Windows development system died and I was forced to
replace it today. In addition, I have improved my boot times
considerably. But the only correlation between the two is
that I
figured I would do a bit of upgrading while I had my case open to
replace the power supply. So, out with the old 850W and in
with
the new 1200W Thermaltake. Additionally, out
with the old 2 x 1TB Raid-0 boot drives and in with the new 4 x 64GB Raid-0 SSD. All
this "high speed, low drag" boot hotness in a fancy 5 1/4" chassis by Patriot. Boot
speed times are as follows:.
2
x 1TB 7200RPM HDD (Raid-0)
Sample
1
Sample
2
Sample
3
Average
Boot to Login
58.00 sec
87.80 sec
87.80 sec
77.87 sec
Login to Desktop
72.50 sec
51.40 sec
32.10 sec
52.00 sec
Login to
Firefox Open/Page Loaded
78.70 sec
63.80 sec
69.80 sec
70.77 sec
4
x 64Gb Patriot TRB SSD (Raid-0)
Sample
1
Sample
2
Sample
3
Average
Boot to Login
32.60 sec
29.40 sec
26.70 sec
29.57 sec
Login to Desktop
5.20 sec
3.40 sec
4.40 sec
4.33 sec
Login to
Firefox Open/Page Loaded
8.30 sec
6.20 sec
6.90 sec
7.13 sec

2010-11-24 Generate password lists using Markov
chains
In
preparation for adding additional password plaintext generators to my GPU password cracker,
I prototyped a simple Markov chain plaintext generator (pwMarkov.pl).
I added it to my John scripts for good measure and am testing
to
see if there is a measurable improvement in cracking efforts now.
2010-05-18 Say goodbye to my liquid cooling system
After
my second coolant leak, it was time to remove my liquid cooling system.
It worked really well at keeping my system cool. It
was not
as effective at keeping it dry. It would not have been as
annoying if I did not have an air cooled system running two dual GPU
graphics cards and a Tesla super computer sitting under my desk at the
same time. My GPU password cracking box just hummed along
without
any overheating issues while my game system learned how to swim in low
conductivity cooling solution. So, I upgraded my case to an
Antec
1200 to match my GPU cracker and replaced my pair of ATI
4895's
with two ATI 5970's and I am back to the races. The 3DMark
numbers speak wonders about both the video cards and the difference
between running Windows XP and Windows 7.

2010-05-12 LogReporter
v1.5 is available
In
response to some feedback from Santiago Zapata, I have updated the
LogReporter.c code to enumerate and report on all active MAC and IP
addresses. Irrespective of the size of your Windows
environment,
you probably struggle with mapping actions in your
firewalls or IDS logs back to users. Stick this program in
your
login scripts and it will provide syslog records for each
login
including NETBIOS computer name, username as well as all active MAC and
IP addresses.
2010-03-19 Mining A/V logs continues to extract gold
After updating my
simple Symantec A/V log parser
I used it to convert syslog Symantec A/V logs to CSV files and loaded
the data into Advizor
Analyst. This type of graph shows interesting re-infection
patterns for individual hosts (horizontal lines), signature updates
following malware blooms (vertical patterns with the same colors) as
well as others.

The y-axis is a list of all infected machines so each horizontal line
is a single system (Host names clipped for anonymity). The color coding
is based on the name of the malware with similar names having similar
colors on the pallet. Analysis of the four solid verticals outside of
the weekly schedule scan pattern (the consistent vertical pattern
across all the plots) were four different outbreaks of a network
scanner where signature updates were loaded across all systems and the
IPS started detecting and blocking immediately. The analysis was done
to evaluate the effectiveness of an A/V deployment. The initial impact
was a clear determination that the A/V system needed some attention and
over time, the analysis was used to re-enforce the value of enabling
additional options in the A/V system. Ongoing analysis shows the tempo
of malware detects and changes to the A/V environment.
2009-10-13 LogReporter
v1.4 is available
I
needed to add support for unicode in my simple login tracker.
While poking around in the source, I added a few more
features to
make is a bit easier to use. If you have a small, medium or
large
Windows environment, you probably struggle with mapping actions in your
firewalls or IDS logs back to users. Stick this program in
your
login scripts and it will provide syslog records for each
login
including NETBIOS computer name, username, MAC address and IP.
The new version does a better job with long and unicode
netbios
names and allows you to specify your loghost by name or IP address.
2009-09-21 A/V logs can help you find troubled
systems
I
was culling through the logs on one of my systems the other day and
realized that I was getting a fair amount of alerts from my Symantec
A/V servers. At first, I was not interested in what malware
was
being detected and cleaned but it got me thinking about what
interesting patterns existed. I suspected that the majority
of
malware infections were caused by a minority of users as most malware
these days require some user action. To test this theory I
wrote
a simple parser
to convert the logs to something that I could push into
a visualizer
and started looking for interesting patterns.

Above
is a histogram plotting A/V detects over time. Each dot is an
piece of malware color coded by host. Horizontal patterns are
a
large quantity of the same piece of malware and vertical lines show
patterns in the A/V detections indicating a schedule for scanning.
This was helpful in deducing the infection and detection
patterns
but not very useful for mapping infections to individual hosts.

This heat map is much more interesting as it shows that a small number
of systems have a disproportionate
number of detected infections. About 50 systems have more
than
3,000 detected pieces of malware while the rest average just two.
This gives the admin teams a short list of systems that they
can
focus on both with technical as well as awareness based remediation.
2009-05-21 I just switched from air to liquid cooling
After
many years of dreading summer and the system over temp lock-ups I just
made the leap into liquid cooling. I had resisted for the
last
couple of years because the cost of entry in money and time was just
too much. After a couple of days to reading on the net I
decided
that it was too simple and cheap, that waiting any longer was silly.

So
far, I am running 32c on my CPU and 35c on both of my GPUs on fan speed
4 of 10. This is not bad considering ambient is 46c and my
CPU
averaged around 50c on air. I will play with this for a
couple
of weeks while I over clock this and that. Once I have
gathered
more data, I will switch from a serial to a parallel flow configuration
and see if that makes any significant difference.
After running the Intel
over clocking utility and installing 3DMark I have a
snapshot of what my new performance is with little tweaking.

2009-04-07 QuickParser
(quickparser) v0.4 released
I
just posted an updated version of QuickParser to SourceForge.
There are some minor bug fixes and changes to the parser to
better support generic logs with key=value pairs.
2008-12-27 Projects on my short list
Of
the long list of projects that I am ignoring most of the time and
banging on when I have a free moment, there are a few that I am putting
on my resolution list to get finished in 2009!
- Log tokenizer, compressor and decompressor
- PDF carver (pdfcarver)
- Network ACL Builder (wirespy)
- IM Sniffer (imspy)
- Forensic packet archiver (The
Wiretapper's Toolkit - TWT)
- DNS Sniffer (pdnsd)
There are also a few ideas that I need to flesh out on paper in 2009
(we shall see how I do).
- "Distrust Engineering", finding the bad guys without
signatures.
- "The State of Information Security Data
Visualization", a Marcus style rant.
- "The
11th Domain of Information Security", how to achieve long term
improvement of the security of your organization by creating a
sustainable information security practice.
2008-08-21 QuickParser
(quickparser) v0.3
In
the spirit of sharing and in the hopes of prodding a co-conspirator
into finishing *his* better, stronger and faster parser, I have
released the source to my regex-less log parser specifically for
Juniper (Netscreen) firewall logs.
2008-07-01 PiRAT
v0.2
I
just upgraded my Nokia N800 to a N810 and it is time to update my tool
chain for OS2008. The new version will sport all of my
favorite
tools including NMAP,
AMAP,
xprobe2,
NBTScan,
NetCat,
Hping2, dsniff,
p0f,
hydra,
John the
Ripper, Snort,
TCPDump,
Metasploit,
Kismet,
Wireshark
(a real pain to build) and many more.
2008-06-19 Transitive Distrust
I have
watched our capability to detect threats degrade year after year as our
adversaries invest more and more time and effort in the pursuit of
stealthiness. As with all arms races, the winner is the faction with
the deepest pockets and lowest overhead. In the corporate
world,
that is a guarantee that the adversaries will always win. I
have
been toying with a different paradigm to identifying threats called
transitive distrust, or as a good friend of mine commented, trust
engineering.
Thesis:
To
test this, I am building with the help of some friends, a system of
instrumentation that applies a simple set of 30-40 rules to all systems
that interact with a given network. Once the rules are
applied, a
trust/distrust map is compiled. This is a very effective
filter
to separate the trusted, and therefore not interesting, from the
untrusted
The system can run
constantly, correcting the evaluated trust/distrust as the data points
change. Distrust
degrades over time so a system that was previously untrusted but no
longer exhibits these traits will become more trusted.
2008-05-31 Monitoring and logging removable media
access with OS/X
I wrongly assumed
that it would
be simple to find an intellectual property (IP) leakage monitoring tool
for removable media on OS/X. It is unfortunate that the
abundance
of this type of tool on Windows has not rubbed off on Mac.
That
said, I hacked together a volume monitoring daemon (vmd)
to provide logging of file activity on removable devices on systems
running OS/X. It is the poor mans solution to the problem.
It uses syslog, so it is possible to have all of your Mac's
point
to a central syslog server and gain arms length auditing of removable
media across all of your OS/X based systems with this little daemon.
A word of caution, I used the fsevents functionality of
10.4 and 10.5 which is not a standard hook for applications.
So don't be surprised if this stops working in a future
version of
OS/X.
2008-04-26 Malware detection through data visualization
Raffael over at secvis.org has been
working to improve the overall state of information security data
visualization. Along with logging, data visualization has
been a
pet project of mine for several years. I have, from time to
time
used visualization to filter through large volumes of data looking for
intruders, malware and data breaches.
I have been trying to find a way to go through firewall logs at a large
corporation where a days worth of traffic equates to 25Gb of
uncompressed logs
and mapping portions of the logs to simple 2D graphs helps
to point out obvious and sometimes subtle anomalies.
When you plot the destination IP address as an integer over time, many
interesting patterns are highlighted. Even more interesting than the horizontal patterns indicating
continuous traffic to specific IP addresses are the vertical clusters
with regularly repeating frequencies.
Even more interesting than the horizontal patterns indicating
continuous traffic to specific IP addresses are the vertical clusters
with regularly repeating frequencies.
Next, a plot of the same data using the destination port number over
time points to obvious port scanning in the form of diagonal
lines as well as odd patterns that sync with the previous destination
IP address plot. 
The last plot of source ports over time points to crafted packets.
Normal sockets allocated through the operating system will
have
positively incrementing source ports for each new connection.
Look for the horizontal lines and you have most likely found
tools
that are not using the operating system to instantiate new sockets.
To me, this screams packet crafting. 
All of these graphs were created by parsing firewalls logs using a perl script and
loading them into Advizor
Analyst.
Web server logs are another source of interesting data if you are able
to separate the wheat from the chaff. Apache2Dot.pl
is a small script that makes clear diagrams of website interactions.
2008-03-19 Sumo
vs. Judo
Over the course of my
career, it has become clear to me that Japan's national
sport offers a perfect analogy for the current state of
information security.

2008-03-18 Is it time for Computer Access
License Agreements?

Now that the US Federal Government is regularly seizing, coping and
snooping into the computers of US Citizens returning home, what can we
do to protect the privacy that we hold dear? The most obvious
response is to encrypt your drives using whatever tools you deem
appropriate. I had considered a "FiST
US Customs" campaign, but I suppose that would not be very
professional. I had also considered implementing some
anti-forensic countermeasures on my computers. A simple
change to
one of the many open source disk wipers could fill your unallocated and
slack space with billions of partial GIF
images. That sure would make going through the preview in EnCASE a bit more
tedious. And I suppose there are even more 'active'
countermeasures available to those who are not squeamish about fighting
back. After all, I have nothing to hide, and its not my job
to
make it easy for Law Enforcement to do theirs. Then it
occurred
to me as I was ranting to a fellow infosec practitioner. What
we
need is the equivalent of a EULA for our computers. Something
that warns off would-be snoopers who decide to look at our computers
without a warrant. I suppose putting one of these stickers on
your computer and your hard drives is just asking for them to be
confiscated, never to be seen again. But it sure would make a
great story.
2008-03-14 DPS for life!






Distance makes the
heart grow fonder.
2008-01-24 Passive syslog monitor v1.2.1 (psmd) has been
released
After many days of
pushing
hundreds of gigabytes of data through it, the new version of psmd
offers many bug fixes and a new TCP reassembler which notes lost log
data due to dropped packets. Along with the new features,
psmd
still offers many others:
- Passive syslog monitoring (no listening ports)
- Support for syslog over UDP and TCP (syslog-ng)
- Archiving of all log data with proper time stamps,
source and dest MAC and IP address
- MD5 and SHA1 hashing of all archived logs
- Forwarding of syslog data with or without forged
source IP addresses
- TIMEMARK insertion to handle time zone and time skew
issues
2007-09-25 Sending a shout out to my com padre
Further continuing
the South
Park theme, I bring you yet another image of a fellow student of Sun
Tsu and InfoSec practitioner. Can you guess who it is?

I just want to know one thing, where is my cut of the shirt
action Tom?
2007-09-22 Regexless log parsing (quickparser)
A co-conspirator
and I have been
building some log analysis tools. To feed data to the tools,
we
needed to convert log files into a pseudo XML format. I built
a
couple of regex log parsers in perl but they were very slow.
We
have spent some time talking about other ways of parsing logs and I
cannibalized a log compression tool that I had built using regexless
parsing and found out that it is pretty fast. By fast I am
talking 2.6M lines per minute on a single processor 2.5GHz PC running
linux and 950K lines per minute on a SunBlade 2000 with 1GHz processors.
Check out my quickparser,
it chews up syslog data from Netscreen firewalls. It should
work
properly with any syslog source that uses key/value pairs separated by
a '='.
2007-08-17 "Better out than in, that's what
I always say!" -Shrek
InfoSec is from
Pluto, NetOps is from Jupiter
As
the tenth largest body orbiting our sun, Pluto has in recent years been
center stage to heated discussion about what makes a planet.
Living on
Pluto as it spins around its eccentric orbit at a chilly 29 AU to a
really chilly 49 AU from our Sun would be quite a challenge.
It's cold
and lonely and most people don't even consider Pluto a planet including
the IAU which on August 24th, 2006 relegated Pluto to 'dwarf planet'
status. It is surprisingly similar to the life as an InfoSec
professional. They are center stage to heated discussions
about the
significance, priority and impact of information security on
organizations. Aside from government and financial circles,
InfoSec is
at best an ugly stepchild and at worst is the bastard child of an
adulterous relationship. To the rest of the world, information security
is the curse of 'due diligence and care' that is resisted, ignored and
hated with vim and vigor likened to paying taxes. In short,
information security is the group that tries to make organizations do
silly things that cost too much and delay projects for no good reason
because "security breaches only happen to the other guy, not us".
The fifth planet from our Sun, Jupiter, stacks up as the
largest body in our solar system at 2 ½ times more massive
that all the
other planets put together. Jupiter keeps showing up in the
press with
missions like Voyager, Cassini and Galileo. If that
was not enough of
a spotlight, consider the Shoemaker-Levy 9 Impacts in July of
1994.
Jupiter is big, bright and full of hydrogen. Everybody knows
what
Jupiter looks like and we thank Jupiter for its gravitational pull, we
all prefer to have things hit Jupiter instead of us. Network
operations, like Jupiter, gets lots of visibility, is generally large
in comparison to other operational bodies and is full of an amazingly
diverse class of gases. And we all know to make a bee-line to
NetOps
when we can't surf the Internet.
Putting aside the above analogies, there are some fundamental
differences between InfoSec and NetOps and over the years I have
struggled to understand those differences as a way to improve my
interactions with my family on Jupiter. At its most
fundamental level,
the difference between "network" people and "security" people is that
one is focused on ensuring that packets move and the other
isn't. I
will leave ascribing the correct labels to you, the reader.
This fundamental schism is surprisingly wide and deep. And,
we are talking astronomic units (AU) here, not Grand Canyon
distances.
Countless times, I have gone to my brothers and sisters on Jupiter
asking for help in reducing the 'attack surface' of a problem and time
and time again, I have received feedback and lumps. With each
tongue-lashing and stroke I have heard "We don't have time or
resources". For a long time, I assumed that part of my family
was just
lazy.
The Epiphany came to me last week, NetOps is from Jupiter, not
my home town over on Pluto. When I ask network operations to
install
an ACL or firewall, they resist. Not out of laziness but as
an
instinctive response built into the very fabric of each resident of
Jupiter. Asking to block traffic is like asking them to move
to Pluto,
which is far too small and cold. When I look at the problem,
I see it
through the eyes of a happy resident of Pluto where blocking traffic is
just a matter of simple changes to router and firewall
configurations.
Add in a little audit trail and some monitoring for giggles, and it is
a happy place for all. But when someone from Jupiter looks at
preventing packets from reaching their final destination, it is like
preventing a packet from reaching it's pre-ordained and rightful place
in the universe and the ramifications will topple everything.
Not to
mention making a mess in the holiest of places, the change control
archive.
So, consider this, the next time you endeavor to make the
journey from Pluto to Jupiter to request a packet filter, start the
conversation with "Every packet is sacred", and bring lots of photos of
home to reassure them that Pluto is not all bad, because a network
operator who turns up a firewall is actually a Plutonian on vacation in
a warmer climate.
Ron Dilley
:Plutonian
2007-07-31 Blatant C.a.S.E.
I am sorry Marcus, I just can't keep it to myself . . .

2007-07-30 Passive syslog monitor v1.0 (psmd) has been
released
Thanks to mjr for suggesting an interesting solution to the problem of
how to handle broken time in logs. By broken I mean logs from
systems without accurate time, mixed time zones and the most annoying
of all . . . daylight savings. The new version of psmd
inserts
time marks which record the time skew between log time and the time
that the log is sucked off the wire.
2007-03-22 Yet another project (PiRat)
I just picked up a Nokia
N800
with the intent to port all of my InfoSec related tools to this
ultra-small computing platform. There is a pretty well put
together development environment and a strong open source development
community branded as Maemo.
2006-09-25 ÜberAdmin has a new website
After several years of a really plain website, I decided to give up
using vi for web development and switched to a more modern tool which
was capable of making really fancy websites. Though I opted
not
to make this site much fancier than the vi version, I at least used
more than one font this time.
2006-09-18 Passive syslog monitor daemon has a new home
at SourceForge (psmd)
After tweaking on my code an hour at a time over the last year, I have
finally been pushed and prodded enough to actually release it to the
public. As I am not a programmer by trade and know just how
much
gum and how many rubber bands are used to hold it together, I do so
with a bit of reservation. With all the messages on the logs
mailing list about signing syslog, what else could I do?
2016-07-06 Difftree(dt) v0.5.8 made it into a trade journal!
Difftree earned 5 stars in Linux Pro Magazine's July issue #188 with a nice quote "Difftree is convincing due to its speed, flexibility,
and simple operation. Numerous examples on the project
site and man page help out with the first steps."

* Image included with permission from linuxpromagazine.com
2016-03-27 PDF Carver(pdfcarve) v0.7 has been released
I had a need to extract a malicious binary from a PDF file at CanSecWest this year and was inspired to
dust off my PDF carving code and fix some bugs.
2015-12-29 Difftree(dt) v0.5.8 has been released
I just finished updating difftree to play nicely with ATIME and to report on changes. This come in handy
when you need to see when a file was accessed across a series of time periods. Run difftree every day and
it is simple to see what has happened in a directory tree over time.
2015-08-23 Difftree(dt) has moved from SourceForge to GitHub
I have started moving the many of my projects that could benifit from more community involvement to GitHub. Difftree is the second project to make the trek and I can't wait to see how it improves over time!
2015-08-23 Log Templater (tmpltr) has moved from SourceForge to GitHub
After being forced to use GitHub to help port passivedns to OpenBSD, it is clear that GitHub is far better
than SourceForge.
2015-07-26 Freshening The Wiretappers Toolkit (TWT)
I have been modernizing The Wiretappers Toolkit (TWT)
and just finished standing up a new packet vacuum for my home office. CappuccinoPC makes a nice small form factor fanless machine.
The machine includes an Atom D525, 4Gb Ram, 4xUSB, 4x1Gb Ethernet, RS232 and room for one 2.5" HDD:

I added a 2TB HDD for $110 and an extra external heat-sink for $8. Out the door for $440.
2014-12-03 Selling Packet Vacuums Door-to-Door
Thanks to the IANS Faculty for inviting me to speak
about my second most favorite incident response tool (Packet Vacuums)!
2014-09-18 Enough with the BSoD!
I gave up in frustration at
my Intel Extreme MB
with the BSoD, hangs, thermal events
and on and on. So, time for an upgrade! I switched to an ASUS
Rampage Black Edition. Along with the
MB, CPU and
Ram,
I upgraded my SDD
and HDD configuration.
Boot speed times are as follows:.
2
x 500Gb Samsung 840 EVO SSD (Raid-0)
Sample
1
Sample
2
Sample
3
Average
Boot to Login
27.70 sec
25.80 sec
27.00 sec
26.30 sec
Login to Desktop
3.40 sec
2.50 sec
2.70 sec
2.70 sec
Login to
Chrome Open/Page Loaded
4.50 sec
4.10 sec
4.10 sec
4.20 sec
Now the really important thing is how does this new computer run for gaming? Well, here is the benchmark for
the default motherboard confuguration (no overclocking):

The 2 x RAID-0 Samsung SSD performed much better than the 4 x RAID-0 drives I had previously used:

An additional surprise was how well the 4 x RAID-5 Samsung 2.5" HDD performed:

2013-12-31 Log Templater (tmpltr) v0.6 is now available
I have been laying some ground work for implementing log chain templates in the next version of Log Templater.
Part of that work includes adding support for more field types (IPv4, IPv6, MAC Address and HEX numbers).
These changes clean up the templates and make it simpler and faster to find some key data when responding to
a threat.
2013-04-03 Geeking out with Marcus Ranum - Take 2
My last session
with Marcus in February may have lacked "Marcus", but there was enough participation and positive feedback that he
asked me to come back and have a more detailed discussion. This time, we had a chance to dig much deeper into the topic and
came up with a couple of interesting ideas that we are now percolating on. Perhaps this will lead to a new tool in our kit.
The webcast is available and who knows what may come next.
2013-02-19 Geeking out with Marcus Ranum
I was looking forward to spending some quality
geek out
time with Marcus today talking about logging
and log analysis. Unfortunately, Marcus fell victim to the Webcast gremlins at a hotel in Germany and
was not able to join me. I still had a good time talking with Allan
about all things "logging" but I am looking forward to geeking our with Marcus some other time.
The webcast has been posted along with some takeaways.
2013-01-20 Hosting ISOI 11
I had the honor and privilege of hosting ISOI 11 in January.
There was an amazing array of speakers and topics. I can't wait for ISOI 12!
Special thanks to Dragos for the use of the secure WiFi gear.
2012-06-27 Upgraded GPU Cracker
With the recent breaches of authentication credentials around the Interwebs, I decided to upgrade my GPU
Cracker and see how it performs and how hot my office can get all at the same time. I replaced my aging
Radeon 5xxx boards with three Radeon 7970's
and one Radeon 6970. SHA1 is now running at almost 6T computations
per second using oclHashCat-Plus.
Time to port Nightengale (BaraCUDA) to OpenCL and see how she runs!

2012-02-04 Passive Proxy Daemon (pproxyd) v0.2 is now available
I have been procrastinating about building a libpcap based sniffer that reassembles web traffic and
generates Squid proxy logs for years.
I tried to use Mike Poor's "development via osmosis" trick with a couple of buddies but in the end, I was forced
to put it together in the last couple of weeks to help solve a vexing web application problem. So, in a pinch,
I pulled out the paper clips, rubber bands and chewing gum. Then I read the docs on libnids.
2012-01-17 Log Templater (tmpltr) v0.5 is now available
After some very helpful and specific feedback about the last version of tmpltr, I have added a few additions
including faux clustering for the occasion when it is handy to know what on a given log line has not changed.
There is a performance penalty for this extra processing, but not as much as I had originally expected. The
table below shows average performance metrics on a Linux VM running on an i7 @ 3.2GHz.
Log size and type
Avg. Line Len
Avg. Arg Count
Args Stored
Avg. Lines per Min
18M Line Cisco FW Log
180
32
0
12,004,023/min
18M Line Cisco FW Log (Clustered)
180
32
24,009
4,093,802/Min
11M Line Apache Access Log
246
44
0
9,453,905/Min
11M Line Apache Access Log (Clustered)
246
44
21,666
5,563,009/Min
4M Line Windows Event Log
793
90
0
2,854,123/Min
4M Line Windows Event Log (Clustered)
793
90
70,361
1,183,226/Min
In addition, I have added a greedy mode where the templater will ignore double quotes. This is very useful
when processing web server logs. In non-greedy mode, tmpltr will assume most things in between a pair of double
quotes are a single string. In greedy mode, all data will be handled the same.
2011-10-17 SSD-Spindle Hybrid
I picked up a couple of Seagate MomentusXT 500Gb
Solid State Hybrid drives to see how they stacked up to
my four 120Gb SSDs running RAID-0. I pulled out the very handy HD TunePro and
the sad fact is, configured as a RAID-0, they were no where near as fast as the pure SSD RAID-0. The linear read and the seek speed was also unpredictable.
Even worse, they did not out perform a couple of 1TB spindle drives running RAID-0 as the chart below shows.

2011-10-01 Log Templater (tmpltr) v0.3 is now available
During the last security incident that I worked on, I needed to grind through 20gb of log files looking
for any odd log lines that would indicate the point where the bad guys got in. If I had done it manually,
I would still be looking at log data. Instead, I built a tool that converted logs into pattern
templates and looked for templates that I had never seen before. This allowed me to zero in on just a
few hundred log lines out of all the data.
2011-07-29 Quick Parser (quickparser) v0.5 is now available
After re-implementing some parser code in difftree with bug
fixes and improved bounds checking, I have ported those changes back to this tool. So, I now present
the new and improved quick parser with less bugs and more bounds checking. Re-energized after touching
the code, I am working on the template based version, which will not be limited to syslog style,
key=value formatted logs.
2011-07-27 Directory Tree Differ (difftree) v0.5 is now available
I have released a new version of difftree with more features and less memory leaks.
This new version adds the ability to save directory tree state and to compare both
directories and archives of directory trees that were previously saved. In addition,
you can hash and compare files if accuracy is more important the speed.
2011-07-16 Directory Tree Differ (difftree) v0.4 is now available
While working on a security incident and fighting with tripwire and Osiris,
I gave up and wrote a fast directory diff tool to allow me to do simple
comparisons between SAN snapshots. To tool was so handy for me, I
figured I would share it.
2011-07-03 SSD Redux
After
fighting with the RAID chassis that I picked up to house my new clutch
of SSD drives I returned them all in a fit of nerd rage and downgraded
from a RAID enclosure to a simple JBOD and larger SSD drives.
I have not been disappointed:
4 x
120Gb OCZ SSD (Raid-0)
Sample
1
Sample
2
Sample
3
Average
Boot to Login
27.30 sec
27.50 sec
27.28 sec
27.28 sec
Login to Desktop
3.50 sec
3.10 sec
3.60 sec
3.40 sec
Login to
Firefox Open/Page Loaded
6.90 sec
5.40 sec
6.05 sec
6.12 sec
Using the very handy HD TunePro
utility, I was able to get a bit more imperial data about the
difference in performance between my old configuration and the new SSD
smoke-fest. Here is the read throughput and access time graph
for
the 4x120Gb OCZ Vertex II SSD (Raid-0):

That
may not look too impressive, but if you compare it to the same read
throughput and access time graph for my old 2x1Tb 7200RPM SATA II HDD
(Raid-0) configuration you will see a bit of a difference and why my
grin is from ear to ear:

2011-05-21 Power supply failure leads to faster boot
times
In
the spirit of tricking people into reading what I write, I have given
in to temptation and deliberately misled you. Yes, my old
power
supply on my Windows development system died and I was forced to
replace it today. In addition, I have improved my boot times
considerably. But the only correlation between the two is
that I
figured I would do a bit of upgrading while I had my case open to
replace the power supply. So, out with the old 850W and in
with
the new 1200W Thermaltake. Additionally, out
with the old 2 x 1TB Raid-0 boot drives and in with the new 4 x 64GB Raid-0 SSD. All
this "high speed, low drag" boot hotness in a fancy 5 1/4" chassis by Patriot. Boot
speed times are as follows:.
2
x 1TB 7200RPM HDD (Raid-0)
Sample
1
Sample
2
Sample
3
Average
Boot to Login
58.00 sec
87.80 sec
87.80 sec
77.87 sec
Login to Desktop
72.50 sec
51.40 sec
32.10 sec
52.00 sec
Login to
Firefox Open/Page Loaded
78.70 sec
63.80 sec
69.80 sec
70.77 sec
4
x 64Gb Patriot TRB SSD (Raid-0)
Sample
1
Sample
2
Sample
3
Average
Boot to Login
32.60 sec
29.40 sec
26.70 sec
29.57 sec
Login to Desktop
5.20 sec
3.40 sec
4.40 sec
4.33 sec
Login to
Firefox Open/Page Loaded
8.30 sec
6.20 sec
6.90 sec
7.13 sec

2010-11-24 Generate password lists using Markov
chains
In
preparation for adding additional password plaintext generators to my GPU password cracker,
I prototyped a simple Markov chain plaintext generator (pwMarkov.pl).
I added it to my John scripts for good measure and am testing
to
see if there is a measurable improvement in cracking efforts now.
2010-05-18 Say goodbye to my liquid cooling system
After
my second coolant leak, it was time to remove my liquid cooling system.
It worked really well at keeping my system cool. It
was not
as effective at keeping it dry. It would not have been as
annoying if I did not have an air cooled system running two dual GPU
graphics cards and a Tesla super computer sitting under my desk at the
same time. My GPU password cracking box just hummed along
without
any overheating issues while my game system learned how to swim in low
conductivity cooling solution. So, I upgraded my case to an
Antec
1200 to match my GPU cracker and replaced my pair of ATI
4895's
with two ATI 5970's and I am back to the races. The 3DMark
numbers speak wonders about both the video cards and the difference
between running Windows XP and Windows 7.

2010-05-12 LogReporter
v1.5 is available
In
response to some feedback from Santiago Zapata, I have updated the
LogReporter.c code to enumerate and report on all active MAC and IP
addresses. Irrespective of the size of your Windows
environment,
you probably struggle with mapping actions in your
firewalls or IDS logs back to users. Stick this program in
your
login scripts and it will provide syslog records for each
login
including NETBIOS computer name, username as well as all active MAC and
IP addresses.
2010-03-19 Mining A/V logs continues to extract gold
After updating my
simple Symantec A/V log parser
I used it to convert syslog Symantec A/V logs to CSV files and loaded
the data into Advizor
Analyst. This type of graph shows interesting re-infection
patterns for individual hosts (horizontal lines), signature updates
following malware blooms (vertical patterns with the same colors) as
well as others.

The y-axis is a list of all infected machines so each horizontal line
is a single system (Host names clipped for anonymity). The color coding
is based on the name of the malware with similar names having similar
colors on the pallet. Analysis of the four solid verticals outside of
the weekly schedule scan pattern (the consistent vertical pattern
across all the plots) were four different outbreaks of a network
scanner where signature updates were loaded across all systems and the
IPS started detecting and blocking immediately. The analysis was done
to evaluate the effectiveness of an A/V deployment. The initial impact
was a clear determination that the A/V system needed some attention and
over time, the analysis was used to re-enforce the value of enabling
additional options in the A/V system. Ongoing analysis shows the tempo
of malware detects and changes to the A/V environment.
2009-10-13 LogReporter
v1.4 is available
I
needed to add support for unicode in my simple login tracker.
While poking around in the source, I added a few more
features to
make is a bit easier to use. If you have a small, medium or
large
Windows environment, you probably struggle with mapping actions in your
firewalls or IDS logs back to users. Stick this program in
your
login scripts and it will provide syslog records for each
login
including NETBIOS computer name, username, MAC address and IP.
The new version does a better job with long and unicode
netbios
names and allows you to specify your loghost by name or IP address.
2009-09-21 A/V logs can help you find troubled
systems
I
was culling through the logs on one of my systems the other day and
realized that I was getting a fair amount of alerts from my Symantec
A/V servers. At first, I was not interested in what malware
was
being detected and cleaned but it got me thinking about what
interesting patterns existed. I suspected that the majority
of
malware infections were caused by a minority of users as most malware
these days require some user action. To test this theory I
wrote
a simple parser
to convert the logs to something that I could push into
a visualizer
and started looking for interesting patterns.

Above
is a histogram plotting A/V detects over time. Each dot is an
piece of malware color coded by host. Horizontal patterns are
a
large quantity of the same piece of malware and vertical lines show
patterns in the A/V detections indicating a schedule for scanning.
This was helpful in deducing the infection and detection
patterns
but not very useful for mapping infections to individual hosts.

This heat map is much more interesting as it shows that a small number
of systems have a disproportionate
number of detected infections. About 50 systems have more
than
3,000 detected pieces of malware while the rest average just two.
This gives the admin teams a short list of systems that they
can
focus on both with technical as well as awareness based remediation.
2009-05-21 I just switched from air to liquid cooling
After
many years of dreading summer and the system over temp lock-ups I just
made the leap into liquid cooling. I had resisted for the
last
couple of years because the cost of entry in money and time was just
too much. After a couple of days to reading on the net I
decided
that it was too simple and cheap, that waiting any longer was silly.

So
far, I am running 32c on my CPU and 35c on both of my GPUs on fan speed
4 of 10. This is not bad considering ambient is 46c and my
CPU
averaged around 50c on air. I will play with this for a
couple
of weeks while I over clock this and that. Once I have
gathered
more data, I will switch from a serial to a parallel flow configuration
and see if that makes any significant difference.
After running the Intel
over clocking utility and installing 3DMark I have a
snapshot of what my new performance is with little tweaking.

2009-04-07 QuickParser
(quickparser) v0.4 released
I
just posted an updated version of QuickParser to SourceForge.
There are some minor bug fixes and changes to the parser to
better support generic logs with key=value pairs.
2008-12-27 Projects on my short list
Of
the long list of projects that I am ignoring most of the time and
banging on when I have a free moment, there are a few that I am putting
on my resolution list to get finished in 2009!
- Log tokenizer, compressor and decompressor
- PDF carver (pdfcarver)
- Network ACL Builder (wirespy)
- IM Sniffer (imspy)
- Forensic packet archiver (The
Wiretapper's Toolkit - TWT)
- DNS Sniffer (pdnsd)
There are also a few ideas that I need to flesh out on paper in 2009
(we shall see how I do).
- "Distrust Engineering", finding the bad guys without
signatures.
- "The State of Information Security Data
Visualization", a Marcus style rant.
- "The
11th Domain of Information Security", how to achieve long term
improvement of the security of your organization by creating a
sustainable information security practice.
2008-08-21 QuickParser
(quickparser) v0.3
In
the spirit of sharing and in the hopes of prodding a co-conspirator
into finishing *his* better, stronger and faster parser, I have
released the source to my regex-less log parser specifically for
Juniper (Netscreen) firewall logs.
2008-07-01 PiRAT
v0.2
I
just upgraded my Nokia N800 to a N810 and it is time to update my tool
chain for OS2008. The new version will sport all of my
favorite
tools including NMAP,
AMAP,
xprobe2,
NBTScan,
NetCat,
Hping2, dsniff,
p0f,
hydra,
John the
Ripper, Snort,
TCPDump,
Metasploit,
Kismet,
Wireshark
(a real pain to build) and many more.
2008-06-19 Transitive Distrust
I have
watched our capability to detect threats degrade year after year as our
adversaries invest more and more time and effort in the pursuit of
stealthiness. As with all arms races, the winner is the faction with
the deepest pockets and lowest overhead. In the corporate
world,
that is a guarantee that the adversaries will always win. I
have
been toying with a different paradigm to identifying threats called
transitive distrust, or as a good friend of mine commented, trust
engineering.
Thesis:
To
test this, I am building with the help of some friends, a system of
instrumentation that applies a simple set of 30-40 rules to all systems
that interact with a given network. Once the rules are
applied, a
trust/distrust map is compiled. This is a very effective
filter
to separate the trusted, and therefore not interesting, from the
untrusted
The system can run
constantly, correcting the evaluated trust/distrust as the data points
change. Distrust
degrades over time so a system that was previously untrusted but no
longer exhibits these traits will become more trusted.
2008-05-31 Monitoring and logging removable media
access with OS/X
I wrongly assumed
that it would
be simple to find an intellectual property (IP) leakage monitoring tool
for removable media on OS/X. It is unfortunate that the
abundance
of this type of tool on Windows has not rubbed off on Mac.
That
said, I hacked together a volume monitoring daemon (vmd)
to provide logging of file activity on removable devices on systems
running OS/X. It is the poor mans solution to the problem.
It uses syslog, so it is possible to have all of your Mac's
point
to a central syslog server and gain arms length auditing of removable
media across all of your OS/X based systems with this little daemon.
A word of caution, I used the fsevents functionality of
10.4 and 10.5 which is not a standard hook for applications.
So don't be surprised if this stops working in a future
version of
OS/X.
2008-04-26 Malware detection through data visualization
Raffael over at secvis.org has been
working to improve the overall state of information security data
visualization. Along with logging, data visualization has
been a
pet project of mine for several years. I have, from time to
time
used visualization to filter through large volumes of data looking for
intruders, malware and data breaches.
I have been trying to find a way to go through firewall logs at a large
corporation where a days worth of traffic equates to 25Gb of
uncompressed logs
and mapping portions of the logs to simple 2D graphs helps
to point out obvious and sometimes subtle anomalies.
When you plot the destination IP address as an integer over time, many
interesting patterns are highlighted. Even more interesting than the horizontal patterns indicating
continuous traffic to specific IP addresses are the vertical clusters
with regularly repeating frequencies.
Even more interesting than the horizontal patterns indicating
continuous traffic to specific IP addresses are the vertical clusters
with regularly repeating frequencies.
Next, a plot of the same data using the destination port number over
time points to obvious port scanning in the form of diagonal
lines as well as odd patterns that sync with the previous destination
IP address plot. 
The last plot of source ports over time points to crafted packets.
Normal sockets allocated through the operating system will
have
positively incrementing source ports for each new connection.
Look for the horizontal lines and you have most likely found
tools
that are not using the operating system to instantiate new sockets.
To me, this screams packet crafting. 
All of these graphs were created by parsing firewalls logs using a perl script and
loading them into Advizor
Analyst.
Web server logs are another source of interesting data if you are able
to separate the wheat from the chaff. Apache2Dot.pl
is a small script that makes clear diagrams of website interactions.
2008-03-19 Sumo
vs. Judo
Over the course of my
career, it has become clear to me that Japan's national
sport offers a perfect analogy for the current state of
information security.

2008-03-18 Is it time for Computer Access
License Agreements?

Now that the US Federal Government is regularly seizing, coping and
snooping into the computers of US Citizens returning home, what can we
do to protect the privacy that we hold dear? The most obvious
response is to encrypt your drives using whatever tools you deem
appropriate. I had considered a "FiST
US Customs" campaign, but I suppose that would not be very
professional. I had also considered implementing some
anti-forensic countermeasures on my computers. A simple
change to
one of the many open source disk wipers could fill your unallocated and
slack space with billions of partial GIF
images. That sure would make going through the preview in EnCASE a bit more
tedious. And I suppose there are even more 'active'
countermeasures available to those who are not squeamish about fighting
back. After all, I have nothing to hide, and its not my job
to
make it easy for Law Enforcement to do theirs. Then it
occurred
to me as I was ranting to a fellow infosec practitioner. What
we
need is the equivalent of a EULA for our computers. Something
that warns off would-be snoopers who decide to look at our computers
without a warrant. I suppose putting one of these stickers on
your computer and your hard drives is just asking for them to be
confiscated, never to be seen again. But it sure would make a
great story.
2008-03-14 DPS for life!






Distance makes the
heart grow fonder.
2008-01-24 Passive syslog monitor v1.2.1 (psmd) has been
released
After many days of
pushing
hundreds of gigabytes of data through it, the new version of psmd
offers many bug fixes and a new TCP reassembler which notes lost log
data due to dropped packets. Along with the new features,
psmd
still offers many others:
- Passive syslog monitoring (no listening ports)
- Support for syslog over UDP and TCP (syslog-ng)
- Archiving of all log data with proper time stamps,
source and dest MAC and IP address
- MD5 and SHA1 hashing of all archived logs
- Forwarding of syslog data with or without forged
source IP addresses
- TIMEMARK insertion to handle time zone and time skew
issues
2007-09-25 Sending a shout out to my com padre
Further continuing
the South
Park theme, I bring you yet another image of a fellow student of Sun
Tsu and InfoSec practitioner. Can you guess who it is?

I just want to know one thing, where is my cut of the shirt
action Tom?
2007-09-22 Regexless log parsing (quickparser)
A co-conspirator
and I have been
building some log analysis tools. To feed data to the tools,
we
needed to convert log files into a pseudo XML format. I built
a
couple of regex log parsers in perl but they were very slow.
We
have spent some time talking about other ways of parsing logs and I
cannibalized a log compression tool that I had built using regexless
parsing and found out that it is pretty fast. By fast I am
talking 2.6M lines per minute on a single processor 2.5GHz PC running
linux and 950K lines per minute on a SunBlade 2000 with 1GHz processors.
Check out my quickparser,
it chews up syslog data from Netscreen firewalls. It should
work
properly with any syslog source that uses key/value pairs separated by
a '='.
2007-08-17 "Better out than in, that's what
I always say!" -Shrek
InfoSec is from
Pluto, NetOps is from Jupiter
As
the tenth largest body orbiting our sun, Pluto has in recent years been
center stage to heated discussion about what makes a planet.
Living on
Pluto as it spins around its eccentric orbit at a chilly 29 AU to a
really chilly 49 AU from our Sun would be quite a challenge.
It's cold
and lonely and most people don't even consider Pluto a planet including
the IAU which on August 24th, 2006 relegated Pluto to 'dwarf planet'
status. It is surprisingly similar to the life as an InfoSec
professional. They are center stage to heated discussions
about the
significance, priority and impact of information security on
organizations. Aside from government and financial circles,
InfoSec is
at best an ugly stepchild and at worst is the bastard child of an
adulterous relationship. To the rest of the world, information security
is the curse of 'due diligence and care' that is resisted, ignored and
hated with vim and vigor likened to paying taxes. In short,
information security is the group that tries to make organizations do
silly things that cost too much and delay projects for no good reason
because "security breaches only happen to the other guy, not us".
The fifth planet from our Sun, Jupiter, stacks up as the
largest body in our solar system at 2 ½ times more massive
that all the
other planets put together. Jupiter keeps showing up in the
press with
missions like Voyager, Cassini and Galileo. If that
was not enough of
a spotlight, consider the Shoemaker-Levy 9 Impacts in July of
1994.
Jupiter is big, bright and full of hydrogen. Everybody knows
what
Jupiter looks like and we thank Jupiter for its gravitational pull, we
all prefer to have things hit Jupiter instead of us. Network
operations, like Jupiter, gets lots of visibility, is generally large
in comparison to other operational bodies and is full of an amazingly
diverse class of gases. And we all know to make a bee-line to
NetOps
when we can't surf the Internet.
Putting aside the above analogies, there are some fundamental
differences between InfoSec and NetOps and over the years I have
struggled to understand those differences as a way to improve my
interactions with my family on Jupiter. At its most
fundamental level,
the difference between "network" people and "security" people is that
one is focused on ensuring that packets move and the other
isn't. I
will leave ascribing the correct labels to you, the reader.
This fundamental schism is surprisingly wide and deep. And,
we are talking astronomic units (AU) here, not Grand Canyon
distances.
Countless times, I have gone to my brothers and sisters on Jupiter
asking for help in reducing the 'attack surface' of a problem and time
and time again, I have received feedback and lumps. With each
tongue-lashing and stroke I have heard "We don't have time or
resources". For a long time, I assumed that part of my family
was just
lazy.
The Epiphany came to me last week, NetOps is from Jupiter, not
my home town over on Pluto. When I ask network operations to
install
an ACL or firewall, they resist. Not out of laziness but as
an
instinctive response built into the very fabric of each resident of
Jupiter. Asking to block traffic is like asking them to move
to Pluto,
which is far too small and cold. When I look at the problem,
I see it
through the eyes of a happy resident of Pluto where blocking traffic is
just a matter of simple changes to router and firewall
configurations.
Add in a little audit trail and some monitoring for giggles, and it is
a happy place for all. But when someone from Jupiter looks at
preventing packets from reaching their final destination, it is like
preventing a packet from reaching it's pre-ordained and rightful place
in the universe and the ramifications will topple everything.
Not to
mention making a mess in the holiest of places, the change control
archive.
So, consider this, the next time you endeavor to make the
journey from Pluto to Jupiter to request a packet filter, start the
conversation with "Every packet is sacred", and bring lots of photos of
home to reassure them that Pluto is not all bad, because a network
operator who turns up a firewall is actually a Plutonian on vacation in
a warmer climate.
Ron Dilley
:Plutonian
2007-07-31 Blatant C.a.S.E.
I am sorry Marcus, I just can't keep it to myself . . .

2007-07-30 Passive syslog monitor v1.0 (psmd) has been
released
Thanks to mjr for suggesting an interesting solution to the problem of
how to handle broken time in logs. By broken I mean logs from
systems without accurate time, mixed time zones and the most annoying
of all . . . daylight savings. The new version of psmd
inserts
time marks which record the time skew between log time and the time
that the log is sucked off the wire.
2007-03-22 Yet another project (PiRat)
I just picked up a Nokia
N800
with the intent to port all of my InfoSec related tools to this
ultra-small computing platform. There is a pretty well put
together development environment and a strong open source development
community branded as Maemo.
2006-09-25 ÜberAdmin has a new website
After several years of a really plain website, I decided to give up
using vi for web development and switched to a more modern tool which
was capable of making really fancy websites. Though I opted
not
to make this site much fancier than the vi version, I at least used
more than one font this time.
2006-09-18 Passive syslog monitor daemon has a new home
at SourceForge (psmd)
After tweaking on my code an hour at a time over the last year, I have
finally been pushed and prodded enough to actually release it to the
public. As I am not a programmer by trade and know just how
much
gum and how many rubber bands are used to hold it together, I do so
with a bit of reservation. With all the messages on the logs
mailing list about signing syslog, what else could I do?
2016-03-27 PDF Carver(pdfcarve) v0.7 has been released
I had a need to extract a malicious binary from a PDF file at CanSecWest this year and was inspired to
dust off my PDF carving code and fix some bugs.
2015-12-29 Difftree(dt) v0.5.8 has been released
I just finished updating difftree to play nicely with ATIME and to report on changes. This come in handy
when you need to see when a file was accessed across a series of time periods. Run difftree every day and
it is simple to see what has happened in a directory tree over time.
2015-08-23 Difftree(dt) has moved from SourceForge to GitHub
I have started moving the many of my projects that could benifit from more community involvement to GitHub. Difftree is the second project to make the trek and I can't wait to see how it improves over time!
2015-08-23 Log Templater (tmpltr) has moved from SourceForge to GitHub
After being forced to use GitHub to help port passivedns to OpenBSD, it is clear that GitHub is far better
than SourceForge.
2015-07-26 Freshening The Wiretappers Toolkit (TWT)
I have been modernizing The Wiretappers Toolkit (TWT)
and just finished standing up a new packet vacuum for my home office. CappuccinoPC makes a nice small form factor fanless machine.
The machine includes an Atom D525, 4Gb Ram, 4xUSB, 4x1Gb Ethernet, RS232 and room for one 2.5" HDD:

I added a 2TB HDD for $110 and an extra external heat-sink for $8. Out the door for $440.
2014-12-03 Selling Packet Vacuums Door-to-Door
Thanks to the IANS Faculty for inviting me to speak
about my second most favorite incident response tool (Packet Vacuums)!
2014-09-18 Enough with the BSoD!
I gave up in frustration at
my Intel Extreme MB
with the BSoD, hangs, thermal events
and on and on. So, time for an upgrade! I switched to an ASUS
Rampage Black Edition. Along with the
MB, CPU and
Ram,
I upgraded my SDD
and HDD configuration.
Boot speed times are as follows:.
2
x 500Gb Samsung 840 EVO SSD (Raid-0)
Sample
1
Sample
2
Sample
3
Average
Boot to Login
27.70 sec
25.80 sec
27.00 sec
26.30 sec
Login to Desktop
3.40 sec
2.50 sec
2.70 sec
2.70 sec
Login to
Chrome Open/Page Loaded
4.50 sec
4.10 sec
4.10 sec
4.20 sec
Now the really important thing is how does this new computer run for gaming? Well, here is the benchmark for
the default motherboard confuguration (no overclocking):

The 2 x RAID-0 Samsung SSD performed much better than the 4 x RAID-0 drives I had previously used:

An additional surprise was how well the 4 x RAID-5 Samsung 2.5" HDD performed:

2013-12-31 Log Templater (tmpltr) v0.6 is now available
I have been laying some ground work for implementing log chain templates in the next version of Log Templater.
Part of that work includes adding support for more field types (IPv4, IPv6, MAC Address and HEX numbers).
These changes clean up the templates and make it simpler and faster to find some key data when responding to
a threat.
2013-04-03 Geeking out with Marcus Ranum - Take 2
My last session
with Marcus in February may have lacked "Marcus", but there was enough participation and positive feedback that he
asked me to come back and have a more detailed discussion. This time, we had a chance to dig much deeper into the topic and
came up with a couple of interesting ideas that we are now percolating on. Perhaps this will lead to a new tool in our kit.
The webcast is available and who knows what may come next.
2013-02-19 Geeking out with Marcus Ranum
I was looking forward to spending some quality
geek out
time with Marcus today talking about logging
and log analysis. Unfortunately, Marcus fell victim to the Webcast gremlins at a hotel in Germany and
was not able to join me. I still had a good time talking with Allan
about all things "logging" but I am looking forward to geeking our with Marcus some other time.
The webcast has been posted along with some takeaways.
2013-01-20 Hosting ISOI 11
I had the honor and privilege of hosting ISOI 11 in January.
There was an amazing array of speakers and topics. I can't wait for ISOI 12!
Special thanks to Dragos for the use of the secure WiFi gear.
2012-06-27 Upgraded GPU Cracker
With the recent breaches of authentication credentials around the Interwebs, I decided to upgrade my GPU
Cracker and see how it performs and how hot my office can get all at the same time. I replaced my aging
Radeon 5xxx boards with three Radeon 7970's
and one Radeon 6970. SHA1 is now running at almost 6T computations
per second using oclHashCat-Plus.
Time to port Nightengale (BaraCUDA) to OpenCL and see how she runs!

2012-02-04 Passive Proxy Daemon (pproxyd) v0.2 is now available
I have been procrastinating about building a libpcap based sniffer that reassembles web traffic and
generates Squid proxy logs for years.
I tried to use Mike Poor's "development via osmosis" trick with a couple of buddies but in the end, I was forced
to put it together in the last couple of weeks to help solve a vexing web application problem. So, in a pinch,
I pulled out the paper clips, rubber bands and chewing gum. Then I read the docs on libnids.
2012-01-17 Log Templater (tmpltr) v0.5 is now available
After some very helpful and specific feedback about the last version of tmpltr, I have added a few additions
including faux clustering for the occasion when it is handy to know what on a given log line has not changed.
There is a performance penalty for this extra processing, but not as much as I had originally expected. The
table below shows average performance metrics on a Linux VM running on an i7 @ 3.2GHz.
Log size and type
Avg. Line Len
Avg. Arg Count
Args Stored
Avg. Lines per Min
18M Line Cisco FW Log
180
32
0
12,004,023/min
18M Line Cisco FW Log (Clustered)
180
32
24,009
4,093,802/Min
11M Line Apache Access Log
246
44
0
9,453,905/Min
11M Line Apache Access Log (Clustered)
246
44
21,666
5,563,009/Min
4M Line Windows Event Log
793
90
0
2,854,123/Min
4M Line Windows Event Log (Clustered)
793
90
70,361
1,183,226/Min
In addition, I have added a greedy mode where the templater will ignore double quotes. This is very useful
when processing web server logs. In non-greedy mode, tmpltr will assume most things in between a pair of double
quotes are a single string. In greedy mode, all data will be handled the same.
2011-10-17 SSD-Spindle Hybrid
I picked up a couple of Seagate MomentusXT 500Gb
Solid State Hybrid drives to see how they stacked up to
my four 120Gb SSDs running RAID-0. I pulled out the very handy HD TunePro and
the sad fact is, configured as a RAID-0, they were no where near as fast as the pure SSD RAID-0. The linear read and the seek speed was also unpredictable.
Even worse, they did not out perform a couple of 1TB spindle drives running RAID-0 as the chart below shows.

2011-10-01 Log Templater (tmpltr) v0.3 is now available
During the last security incident that I worked on, I needed to grind through 20gb of log files looking
for any odd log lines that would indicate the point where the bad guys got in. If I had done it manually,
I would still be looking at log data. Instead, I built a tool that converted logs into pattern
templates and looked for templates that I had never seen before. This allowed me to zero in on just a
few hundred log lines out of all the data.
2011-07-29 Quick Parser (quickparser) v0.5 is now available
After re-implementing some parser code in difftree with bug
fixes and improved bounds checking, I have ported those changes back to this tool. So, I now present
the new and improved quick parser with less bugs and more bounds checking. Re-energized after touching
the code, I am working on the template based version, which will not be limited to syslog style,
key=value formatted logs.
2011-07-27 Directory Tree Differ (difftree) v0.5 is now available
I have released a new version of difftree with more features and less memory leaks.
This new version adds the ability to save directory tree state and to compare both
directories and archives of directory trees that were previously saved. In addition,
you can hash and compare files if accuracy is more important the speed.
2011-07-16 Directory Tree Differ (difftree) v0.4 is now available
While working on a security incident and fighting with tripwire and Osiris,
I gave up and wrote a fast directory diff tool to allow me to do simple
comparisons between SAN snapshots. To tool was so handy for me, I
figured I would share it.
2011-07-03 SSD Redux
After
fighting with the RAID chassis that I picked up to house my new clutch
of SSD drives I returned them all in a fit of nerd rage and downgraded
from a RAID enclosure to a simple JBOD and larger SSD drives.
I have not been disappointed:
4 x
120Gb OCZ SSD (Raid-0)
Sample
1
Sample
2
Sample
3
Average
Boot to Login
27.30 sec
27.50 sec
27.28 sec
27.28 sec
Login to Desktop
3.50 sec
3.10 sec
3.60 sec
3.40 sec
Login to
Firefox Open/Page Loaded
6.90 sec
5.40 sec
6.05 sec
6.12 sec
Using the very handy HD TunePro
utility, I was able to get a bit more imperial data about the
difference in performance between my old configuration and the new SSD
smoke-fest. Here is the read throughput and access time graph
for
the 4x120Gb OCZ Vertex II SSD (Raid-0):

That
may not look too impressive, but if you compare it to the same read
throughput and access time graph for my old 2x1Tb 7200RPM SATA II HDD
(Raid-0) configuration you will see a bit of a difference and why my
grin is from ear to ear:

2011-05-21 Power supply failure leads to faster boot
times
In
the spirit of tricking people into reading what I write, I have given
in to temptation and deliberately misled you. Yes, my old
power
supply on my Windows development system died and I was forced to
replace it today. In addition, I have improved my boot times
considerably. But the only correlation between the two is
that I
figured I would do a bit of upgrading while I had my case open to
replace the power supply. So, out with the old 850W and in
with
the new 1200W Thermaltake. Additionally, out
with the old 2 x 1TB Raid-0 boot drives and in with the new 4 x 64GB Raid-0 SSD. All
this "high speed, low drag" boot hotness in a fancy 5 1/4" chassis by Patriot. Boot
speed times are as follows:.
2
x 1TB 7200RPM HDD (Raid-0)
Sample
1
Sample
2
Sample
3
Average
Boot to Login
58.00 sec
87.80 sec
87.80 sec
77.87 sec
Login to Desktop
72.50 sec
51.40 sec
32.10 sec
52.00 sec
Login to
Firefox Open/Page Loaded
78.70 sec
63.80 sec
69.80 sec
70.77 sec
4
x 64Gb Patriot TRB SSD (Raid-0)
Sample
1
Sample
2
Sample
3
Average
Boot to Login
32.60 sec
29.40 sec
26.70 sec
29.57 sec
Login to Desktop
5.20 sec
3.40 sec
4.40 sec
4.33 sec
Login to
Firefox Open/Page Loaded
8.30 sec
6.20 sec
6.90 sec
7.13 sec

2010-11-24 Generate password lists using Markov
chains
In
preparation for adding additional password plaintext generators to my GPU password cracker,
I prototyped a simple Markov chain plaintext generator (pwMarkov.pl).
I added it to my John scripts for good measure and am testing
to
see if there is a measurable improvement in cracking efforts now.
2010-05-18 Say goodbye to my liquid cooling system
After
my second coolant leak, it was time to remove my liquid cooling system.
It worked really well at keeping my system cool. It
was not
as effective at keeping it dry. It would not have been as
annoying if I did not have an air cooled system running two dual GPU
graphics cards and a Tesla super computer sitting under my desk at the
same time. My GPU password cracking box just hummed along
without
any overheating issues while my game system learned how to swim in low
conductivity cooling solution. So, I upgraded my case to an
Antec
1200 to match my GPU cracker and replaced my pair of ATI
4895's
with two ATI 5970's and I am back to the races. The 3DMark
numbers speak wonders about both the video cards and the difference
between running Windows XP and Windows 7.

2010-05-12 LogReporter
v1.5 is available
In
response to some feedback from Santiago Zapata, I have updated the
LogReporter.c code to enumerate and report on all active MAC and IP
addresses. Irrespective of the size of your Windows
environment,
you probably struggle with mapping actions in your
firewalls or IDS logs back to users. Stick this program in
your
login scripts and it will provide syslog records for each
login
including NETBIOS computer name, username as well as all active MAC and
IP addresses.
2010-03-19 Mining A/V logs continues to extract gold
After updating my
simple Symantec A/V log parser
I used it to convert syslog Symantec A/V logs to CSV files and loaded
the data into Advizor
Analyst. This type of graph shows interesting re-infection
patterns for individual hosts (horizontal lines), signature updates
following malware blooms (vertical patterns with the same colors) as
well as others.

The y-axis is a list of all infected machines so each horizontal line
is a single system (Host names clipped for anonymity). The color coding
is based on the name of the malware with similar names having similar
colors on the pallet. Analysis of the four solid verticals outside of
the weekly schedule scan pattern (the consistent vertical pattern
across all the plots) were four different outbreaks of a network
scanner where signature updates were loaded across all systems and the
IPS started detecting and blocking immediately. The analysis was done
to evaluate the effectiveness of an A/V deployment. The initial impact
was a clear determination that the A/V system needed some attention and
over time, the analysis was used to re-enforce the value of enabling
additional options in the A/V system. Ongoing analysis shows the tempo
of malware detects and changes to the A/V environment.
2009-10-13 LogReporter
v1.4 is available
I
needed to add support for unicode in my simple login tracker.
While poking around in the source, I added a few more
features to
make is a bit easier to use. If you have a small, medium or
large
Windows environment, you probably struggle with mapping actions in your
firewalls or IDS logs back to users. Stick this program in
your
login scripts and it will provide syslog records for each
login
including NETBIOS computer name, username, MAC address and IP.
The new version does a better job with long and unicode
netbios
names and allows you to specify your loghost by name or IP address.
2009-09-21 A/V logs can help you find troubled
systems
I
was culling through the logs on one of my systems the other day and
realized that I was getting a fair amount of alerts from my Symantec
A/V servers. At first, I was not interested in what malware
was
being detected and cleaned but it got me thinking about what
interesting patterns existed. I suspected that the majority
of
malware infections were caused by a minority of users as most malware
these days require some user action. To test this theory I
wrote
a simple parser
to convert the logs to something that I could push into
a visualizer
and started looking for interesting patterns.

Above
is a histogram plotting A/V detects over time. Each dot is an
piece of malware color coded by host. Horizontal patterns are
a
large quantity of the same piece of malware and vertical lines show
patterns in the A/V detections indicating a schedule for scanning.
This was helpful in deducing the infection and detection
patterns
but not very useful for mapping infections to individual hosts.

This heat map is much more interesting as it shows that a small number
of systems have a disproportionate
number of detected infections. About 50 systems have more
than
3,000 detected pieces of malware while the rest average just two.
This gives the admin teams a short list of systems that they
can
focus on both with technical as well as awareness based remediation.
2009-05-21 I just switched from air to liquid cooling
After
many years of dreading summer and the system over temp lock-ups I just
made the leap into liquid cooling. I had resisted for the
last
couple of years because the cost of entry in money and time was just
too much. After a couple of days to reading on the net I
decided
that it was too simple and cheap, that waiting any longer was silly.

So
far, I am running 32c on my CPU and 35c on both of my GPUs on fan speed
4 of 10. This is not bad considering ambient is 46c and my
CPU
averaged around 50c on air. I will play with this for a
couple
of weeks while I over clock this and that. Once I have
gathered
more data, I will switch from a serial to a parallel flow configuration
and see if that makes any significant difference.
After running the Intel
over clocking utility and installing 3DMark I have a
snapshot of what my new performance is with little tweaking.

2009-04-07 QuickParser
(quickparser) v0.4 released
I
just posted an updated version of QuickParser to SourceForge.
There are some minor bug fixes and changes to the parser to
better support generic logs with key=value pairs.
2008-12-27 Projects on my short list
Of
the long list of projects that I am ignoring most of the time and
banging on when I have a free moment, there are a few that I am putting
on my resolution list to get finished in 2009!
- Log tokenizer, compressor and decompressor
- PDF carver (pdfcarver)
- Network ACL Builder (wirespy)
- IM Sniffer (imspy)
- Forensic packet archiver (The
Wiretapper's Toolkit - TWT)
- DNS Sniffer (pdnsd)
There are also a few ideas that I need to flesh out on paper in 2009
(we shall see how I do).
- "Distrust Engineering", finding the bad guys without
signatures.
- "The State of Information Security Data
Visualization", a Marcus style rant.
- "The
11th Domain of Information Security", how to achieve long term
improvement of the security of your organization by creating a
sustainable information security practice.
2008-08-21 QuickParser
(quickparser) v0.3
In
the spirit of sharing and in the hopes of prodding a co-conspirator
into finishing *his* better, stronger and faster parser, I have
released the source to my regex-less log parser specifically for
Juniper (Netscreen) firewall logs.
2008-07-01 PiRAT
v0.2
I
just upgraded my Nokia N800 to a N810 and it is time to update my tool
chain for OS2008. The new version will sport all of my
favorite
tools including NMAP,
AMAP,
xprobe2,
NBTScan,
NetCat,
Hping2, dsniff,
p0f,
hydra,
John the
Ripper, Snort,
TCPDump,
Metasploit,
Kismet,
Wireshark
(a real pain to build) and many more.
2008-06-19 Transitive Distrust
I have
watched our capability to detect threats degrade year after year as our
adversaries invest more and more time and effort in the pursuit of
stealthiness. As with all arms races, the winner is the faction with
the deepest pockets and lowest overhead. In the corporate
world,
that is a guarantee that the adversaries will always win. I
have
been toying with a different paradigm to identifying threats called
transitive distrust, or as a good friend of mine commented, trust
engineering.
Thesis:
To
test this, I am building with the help of some friends, a system of
instrumentation that applies a simple set of 30-40 rules to all systems
that interact with a given network. Once the rules are
applied, a
trust/distrust map is compiled. This is a very effective
filter
to separate the trusted, and therefore not interesting, from the
untrusted
The system can run
constantly, correcting the evaluated trust/distrust as the data points
change. Distrust
degrades over time so a system that was previously untrusted but no
longer exhibits these traits will become more trusted.
2008-05-31 Monitoring and logging removable media
access with OS/X
I wrongly assumed
that it would
be simple to find an intellectual property (IP) leakage monitoring tool
for removable media on OS/X. It is unfortunate that the
abundance
of this type of tool on Windows has not rubbed off on Mac.
That
said, I hacked together a volume monitoring daemon (vmd)
to provide logging of file activity on removable devices on systems
running OS/X. It is the poor mans solution to the problem.
It uses syslog, so it is possible to have all of your Mac's
point
to a central syslog server and gain arms length auditing of removable
media across all of your OS/X based systems with this little daemon.
A word of caution, I used the fsevents functionality of
10.4 and 10.5 which is not a standard hook for applications.
So don't be surprised if this stops working in a future
version of
OS/X.
2008-04-26 Malware detection through data visualization
Raffael over at secvis.org has been
working to improve the overall state of information security data
visualization. Along with logging, data visualization has
been a
pet project of mine for several years. I have, from time to
time
used visualization to filter through large volumes of data looking for
intruders, malware and data breaches.
I have been trying to find a way to go through firewall logs at a large
corporation where a days worth of traffic equates to 25Gb of
uncompressed logs
and mapping portions of the logs to simple 2D graphs helps
to point out obvious and sometimes subtle anomalies.
When you plot the destination IP address as an integer over time, many
interesting patterns are highlighted. Even more interesting than the horizontal patterns indicating
continuous traffic to specific IP addresses are the vertical clusters
with regularly repeating frequencies.
Even more interesting than the horizontal patterns indicating
continuous traffic to specific IP addresses are the vertical clusters
with regularly repeating frequencies.
Next, a plot of the same data using the destination port number over
time points to obvious port scanning in the form of diagonal
lines as well as odd patterns that sync with the previous destination
IP address plot. 
The last plot of source ports over time points to crafted packets.
Normal sockets allocated through the operating system will
have
positively incrementing source ports for each new connection.
Look for the horizontal lines and you have most likely found
tools
that are not using the operating system to instantiate new sockets.
To me, this screams packet crafting. 
All of these graphs were created by parsing firewalls logs using a perl script and
loading them into Advizor
Analyst.
Web server logs are another source of interesting data if you are able
to separate the wheat from the chaff. Apache2Dot.pl
is a small script that makes clear diagrams of website interactions.
2008-03-19 Sumo
vs. Judo
Over the course of my
career, it has become clear to me that Japan's national
sport offers a perfect analogy for the current state of
information security.

2008-03-18 Is it time for Computer Access
License Agreements?

Now that the US Federal Government is regularly seizing, coping and
snooping into the computers of US Citizens returning home, what can we
do to protect the privacy that we hold dear? The most obvious
response is to encrypt your drives using whatever tools you deem
appropriate. I had considered a "FiST
US Customs" campaign, but I suppose that would not be very
professional. I had also considered implementing some
anti-forensic countermeasures on my computers. A simple
change to
one of the many open source disk wipers could fill your unallocated and
slack space with billions of partial GIF
images. That sure would make going through the preview in EnCASE a bit more
tedious. And I suppose there are even more 'active'
countermeasures available to those who are not squeamish about fighting
back. After all, I have nothing to hide, and its not my job
to
make it easy for Law Enforcement to do theirs. Then it
occurred
to me as I was ranting to a fellow infosec practitioner. What
we
need is the equivalent of a EULA for our computers. Something
that warns off would-be snoopers who decide to look at our computers
without a warrant. I suppose putting one of these stickers on
your computer and your hard drives is just asking for them to be
confiscated, never to be seen again. But it sure would make a
great story.
2008-03-14 DPS for life!






Distance makes the
heart grow fonder.
2008-01-24 Passive syslog monitor v1.2.1 (psmd) has been
released
After many days of
pushing
hundreds of gigabytes of data through it, the new version of psmd
offers many bug fixes and a new TCP reassembler which notes lost log
data due to dropped packets. Along with the new features,
psmd
still offers many others:
- Passive syslog monitoring (no listening ports)
- Support for syslog over UDP and TCP (syslog-ng)
- Archiving of all log data with proper time stamps,
source and dest MAC and IP address
- MD5 and SHA1 hashing of all archived logs
- Forwarding of syslog data with or without forged
source IP addresses
- TIMEMARK insertion to handle time zone and time skew
issues
2007-09-25 Sending a shout out to my com padre
Further continuing
the South
Park theme, I bring you yet another image of a fellow student of Sun
Tsu and InfoSec practitioner. Can you guess who it is?

I just want to know one thing, where is my cut of the shirt
action Tom?
2007-09-22 Regexless log parsing (quickparser)
A co-conspirator
and I have been
building some log analysis tools. To feed data to the tools,
we
needed to convert log files into a pseudo XML format. I built
a
couple of regex log parsers in perl but they were very slow.
We
have spent some time talking about other ways of parsing logs and I
cannibalized a log compression tool that I had built using regexless
parsing and found out that it is pretty fast. By fast I am
talking 2.6M lines per minute on a single processor 2.5GHz PC running
linux and 950K lines per minute on a SunBlade 2000 with 1GHz processors.
Check out my quickparser,
it chews up syslog data from Netscreen firewalls. It should
work
properly with any syslog source that uses key/value pairs separated by
a '='.
2007-08-17 "Better out than in, that's what
I always say!" -Shrek
InfoSec is from
Pluto, NetOps is from Jupiter
As
the tenth largest body orbiting our sun, Pluto has in recent years been
center stage to heated discussion about what makes a planet.
Living on
Pluto as it spins around its eccentric orbit at a chilly 29 AU to a
really chilly 49 AU from our Sun would be quite a challenge.
It's cold
and lonely and most people don't even consider Pluto a planet including
the IAU which on August 24th, 2006 relegated Pluto to 'dwarf planet'
status. It is surprisingly similar to the life as an InfoSec
professional. They are center stage to heated discussions
about the
significance, priority and impact of information security on
organizations. Aside from government and financial circles,
InfoSec is
at best an ugly stepchild and at worst is the bastard child of an
adulterous relationship. To the rest of the world, information security
is the curse of 'due diligence and care' that is resisted, ignored and
hated with vim and vigor likened to paying taxes. In short,
information security is the group that tries to make organizations do
silly things that cost too much and delay projects for no good reason
because "security breaches only happen to the other guy, not us".
The fifth planet from our Sun, Jupiter, stacks up as the
largest body in our solar system at 2 ½ times more massive
that all the
other planets put together. Jupiter keeps showing up in the
press with
missions like Voyager, Cassini and Galileo. If that
was not enough of
a spotlight, consider the Shoemaker-Levy 9 Impacts in July of
1994.
Jupiter is big, bright and full of hydrogen. Everybody knows
what
Jupiter looks like and we thank Jupiter for its gravitational pull, we
all prefer to have things hit Jupiter instead of us. Network
operations, like Jupiter, gets lots of visibility, is generally large
in comparison to other operational bodies and is full of an amazingly
diverse class of gases. And we all know to make a bee-line to
NetOps
when we can't surf the Internet.
Putting aside the above analogies, there are some fundamental
differences between InfoSec and NetOps and over the years I have
struggled to understand those differences as a way to improve my
interactions with my family on Jupiter. At its most
fundamental level,
the difference between "network" people and "security" people is that
one is focused on ensuring that packets move and the other
isn't. I
will leave ascribing the correct labels to you, the reader.
This fundamental schism is surprisingly wide and deep. And,
we are talking astronomic units (AU) here, not Grand Canyon
distances.
Countless times, I have gone to my brothers and sisters on Jupiter
asking for help in reducing the 'attack surface' of a problem and time
and time again, I have received feedback and lumps. With each
tongue-lashing and stroke I have heard "We don't have time or
resources". For a long time, I assumed that part of my family
was just
lazy.
The Epiphany came to me last week, NetOps is from Jupiter, not
my home town over on Pluto. When I ask network operations to
install
an ACL or firewall, they resist. Not out of laziness but as
an
instinctive response built into the very fabric of each resident of
Jupiter. Asking to block traffic is like asking them to move
to Pluto,
which is far too small and cold. When I look at the problem,
I see it
through the eyes of a happy resident of Pluto where blocking traffic is
just a matter of simple changes to router and firewall
configurations.
Add in a little audit trail and some monitoring for giggles, and it is
a happy place for all. But when someone from Jupiter looks at
preventing packets from reaching their final destination, it is like
preventing a packet from reaching it's pre-ordained and rightful place
in the universe and the ramifications will topple everything.
Not to
mention making a mess in the holiest of places, the change control
archive.
So, consider this, the next time you endeavor to make the
journey from Pluto to Jupiter to request a packet filter, start the
conversation with "Every packet is sacred", and bring lots of photos of
home to reassure them that Pluto is not all bad, because a network
operator who turns up a firewall is actually a Plutonian on vacation in
a warmer climate.
Ron Dilley
:Plutonian
2007-07-31 Blatant C.a.S.E.
I am sorry Marcus, I just can't keep it to myself . . .

2007-07-30 Passive syslog monitor v1.0 (psmd) has been
released
Thanks to mjr for suggesting an interesting solution to the problem of
how to handle broken time in logs. By broken I mean logs from
systems without accurate time, mixed time zones and the most annoying
of all . . . daylight savings. The new version of psmd
inserts
time marks which record the time skew between log time and the time
that the log is sucked off the wire.
2007-03-22 Yet another project (PiRat)
I just picked up a Nokia
N800
with the intent to port all of my InfoSec related tools to this
ultra-small computing platform. There is a pretty well put
together development environment and a strong open source development
community branded as Maemo.
2006-09-25 ÜberAdmin has a new website
After several years of a really plain website, I decided to give up
using vi for web development and switched to a more modern tool which
was capable of making really fancy websites. Though I opted
not
to make this site much fancier than the vi version, I at least used
more than one font this time.
2006-09-18 Passive syslog monitor daemon has a new home
at SourceForge (psmd)
After tweaking on my code an hour at a time over the last year, I have
finally been pushed and prodded enough to actually release it to the
public. As I am not a programmer by trade and know just how
much
gum and how many rubber bands are used to hold it together, I do so
with a bit of reservation. With all the messages on the logs
mailing list about signing syslog, what else could I do?
2015-08-23 Difftree(dt) has moved from SourceForge to GitHub
I have started moving the many of my projects that could benifit from more community involvement to GitHub. Difftree is the second project to make the trek and I can't wait to see how it improves over time!
2015-08-23 Log Templater (tmpltr) has moved from SourceForge to GitHub
After being forced to use GitHub to help port passivedns to OpenBSD, it is clear that GitHub is far better
than SourceForge.
2015-07-26 Freshening The Wiretappers Toolkit (TWT)
I have been modernizing The Wiretappers Toolkit (TWT)
and just finished standing up a new packet vacuum for my home office. CappuccinoPC makes a nice small form factor fanless machine.
The machine includes an Atom D525, 4Gb Ram, 4xUSB, 4x1Gb Ethernet, RS232 and room for one 2.5" HDD:

I added a 2TB HDD for $110 and an extra external heat-sink for $8. Out the door for $440.
2014-12-03 Selling Packet Vacuums Door-to-Door
Thanks to the IANS Faculty for inviting me to speak
about my second most favorite incident response tool (Packet Vacuums)!
2014-09-18 Enough with the BSoD!
I gave up in frustration at
my Intel Extreme MB
with the BSoD, hangs, thermal events
and on and on. So, time for an upgrade! I switched to an ASUS
Rampage Black Edition. Along with the
MB, CPU and
Ram,
I upgraded my SDD
and HDD configuration.
Boot speed times are as follows:.
2
x 500Gb Samsung 840 EVO SSD (Raid-0)
Sample
1
Sample
2
Sample
3
Average
Boot to Login
27.70 sec
25.80 sec
27.00 sec
26.30 sec
Login to Desktop
3.40 sec
2.50 sec
2.70 sec
2.70 sec
Login to
Chrome Open/Page Loaded
4.50 sec
4.10 sec
4.10 sec
4.20 sec
Now the really important thing is how does this new computer run for gaming? Well, here is the benchmark for
the default motherboard confuguration (no overclocking):

The 2 x RAID-0 Samsung SSD performed much better than the 4 x RAID-0 drives I had previously used:

An additional surprise was how well the 4 x RAID-5 Samsung 2.5" HDD performed:

2013-12-31 Log Templater (tmpltr) v0.6 is now available
I have been laying some ground work for implementing log chain templates in the next version of Log Templater.
Part of that work includes adding support for more field types (IPv4, IPv6, MAC Address and HEX numbers).
These changes clean up the templates and make it simpler and faster to find some key data when responding to
a threat.
2013-04-03 Geeking out with Marcus Ranum - Take 2
My last session
with Marcus in February may have lacked "Marcus", but there was enough participation and positive feedback that he
asked me to come back and have a more detailed discussion. This time, we had a chance to dig much deeper into the topic and
came up with a couple of interesting ideas that we are now percolating on. Perhaps this will lead to a new tool in our kit.
The webcast is available and who knows what may come next.
2013-02-19 Geeking out with Marcus Ranum
I was looking forward to spending some quality
geek out
time with Marcus today talking about logging
and log analysis. Unfortunately, Marcus fell victim to the Webcast gremlins at a hotel in Germany and
was not able to join me. I still had a good time talking with Allan
about all things "logging" but I am looking forward to geeking our with Marcus some other time.
The webcast has been posted along with some takeaways.
2013-01-20 Hosting ISOI 11
I had the honor and privilege of hosting ISOI 11 in January.
There was an amazing array of speakers and topics. I can't wait for ISOI 12!
Special thanks to Dragos for the use of the secure WiFi gear.
2012-06-27 Upgraded GPU Cracker
With the recent breaches of authentication credentials around the Interwebs, I decided to upgrade my GPU
Cracker and see how it performs and how hot my office can get all at the same time. I replaced my aging
Radeon 5xxx boards with three Radeon 7970's
and one Radeon 6970. SHA1 is now running at almost 6T computations
per second using oclHashCat-Plus.
Time to port Nightengale (BaraCUDA) to OpenCL and see how she runs!

2012-02-04 Passive Proxy Daemon (pproxyd) v0.2 is now available
I have been procrastinating about building a libpcap based sniffer that reassembles web traffic and
generates Squid proxy logs for years.
I tried to use Mike Poor's "development via osmosis" trick with a couple of buddies but in the end, I was forced
to put it together in the last couple of weeks to help solve a vexing web application problem. So, in a pinch,
I pulled out the paper clips, rubber bands and chewing gum. Then I read the docs on libnids.
2012-01-17 Log Templater (tmpltr) v0.5 is now available
After some very helpful and specific feedback about the last version of tmpltr, I have added a few additions
including faux clustering for the occasion when it is handy to know what on a given log line has not changed.
There is a performance penalty for this extra processing, but not as much as I had originally expected. The
table below shows average performance metrics on a Linux VM running on an i7 @ 3.2GHz.
Log size and type
Avg. Line Len
Avg. Arg Count
Args Stored
Avg. Lines per Min
18M Line Cisco FW Log
180
32
0
12,004,023/min
18M Line Cisco FW Log (Clustered)
180
32
24,009
4,093,802/Min
11M Line Apache Access Log
246
44
0
9,453,905/Min
11M Line Apache Access Log (Clustered)
246
44
21,666
5,563,009/Min
4M Line Windows Event Log
793
90
0
2,854,123/Min
4M Line Windows Event Log (Clustered)
793
90
70,361
1,183,226/Min
In addition, I have added a greedy mode where the templater will ignore double quotes. This is very useful
when processing web server logs. In non-greedy mode, tmpltr will assume most things in between a pair of double
quotes are a single string. In greedy mode, all data will be handled the same.
2011-10-17 SSD-Spindle Hybrid
I picked up a couple of Seagate MomentusXT 500Gb
Solid State Hybrid drives to see how they stacked up to
my four 120Gb SSDs running RAID-0. I pulled out the very handy HD TunePro and
the sad fact is, configured as a RAID-0, they were no where near as fast as the pure SSD RAID-0. The linear read and the seek speed was also unpredictable.
Even worse, they did not out perform a couple of 1TB spindle drives running RAID-0 as the chart below shows.

2011-10-01 Log Templater (tmpltr) v0.3 is now available
During the last security incident that I worked on, I needed to grind through 20gb of log files looking
for any odd log lines that would indicate the point where the bad guys got in. If I had done it manually,
I would still be looking at log data. Instead, I built a tool that converted logs into pattern
templates and looked for templates that I had never seen before. This allowed me to zero in on just a
few hundred log lines out of all the data.
2011-07-29 Quick Parser (quickparser) v0.5 is now available
After re-implementing some parser code in difftree with bug
fixes and improved bounds checking, I have ported those changes back to this tool. So, I now present
the new and improved quick parser with less bugs and more bounds checking. Re-energized after touching
the code, I am working on the template based version, which will not be limited to syslog style,
key=value formatted logs.
2011-07-27 Directory Tree Differ (difftree) v0.5 is now available
I have released a new version of difftree with more features and less memory leaks.
This new version adds the ability to save directory tree state and to compare both
directories and archives of directory trees that were previously saved. In addition,
you can hash and compare files if accuracy is more important the speed.
2011-07-16 Directory Tree Differ (difftree) v0.4 is now available
While working on a security incident and fighting with tripwire and Osiris,
I gave up and wrote a fast directory diff tool to allow me to do simple
comparisons between SAN snapshots. To tool was so handy for me, I
figured I would share it.
2011-07-03 SSD Redux
After
fighting with the RAID chassis that I picked up to house my new clutch
of SSD drives I returned them all in a fit of nerd rage and downgraded
from a RAID enclosure to a simple JBOD and larger SSD drives.
I have not been disappointed:
4 x
120Gb OCZ SSD (Raid-0)
Sample
1
Sample
2
Sample
3
Average
Boot to Login
27.30 sec
27.50 sec
27.28 sec
27.28 sec
Login to Desktop
3.50 sec
3.10 sec
3.60 sec
3.40 sec
Login to
Firefox Open/Page Loaded
6.90 sec
5.40 sec
6.05 sec
6.12 sec
Using the very handy HD TunePro
utility, I was able to get a bit more imperial data about the
difference in performance between my old configuration and the new SSD
smoke-fest. Here is the read throughput and access time graph
for
the 4x120Gb OCZ Vertex II SSD (Raid-0):

That
may not look too impressive, but if you compare it to the same read
throughput and access time graph for my old 2x1Tb 7200RPM SATA II HDD
(Raid-0) configuration you will see a bit of a difference and why my
grin is from ear to ear:

2011-05-21 Power supply failure leads to faster boot
times
In
the spirit of tricking people into reading what I write, I have given
in to temptation and deliberately misled you. Yes, my old
power
supply on my Windows development system died and I was forced to
replace it today. In addition, I have improved my boot times
considerably. But the only correlation between the two is
that I
figured I would do a bit of upgrading while I had my case open to
replace the power supply. So, out with the old 850W and in
with
the new 1200W Thermaltake. Additionally, out
with the old 2 x 1TB Raid-0 boot drives and in with the new 4 x 64GB Raid-0 SSD. All
this "high speed, low drag" boot hotness in a fancy 5 1/4" chassis by Patriot. Boot
speed times are as follows:.
2
x 1TB 7200RPM HDD (Raid-0)
Sample
1
Sample
2
Sample
3
Average
Boot to Login
58.00 sec
87.80 sec
87.80 sec
77.87 sec
Login to Desktop
72.50 sec
51.40 sec
32.10 sec
52.00 sec
Login to
Firefox Open/Page Loaded
78.70 sec
63.80 sec
69.80 sec
70.77 sec
4
x 64Gb Patriot TRB SSD (Raid-0)
Sample
1
Sample
2
Sample
3
Average
Boot to Login
32.60 sec
29.40 sec
26.70 sec
29.57 sec
Login to Desktop
5.20 sec
3.40 sec
4.40 sec
4.33 sec
Login to
Firefox Open/Page Loaded
8.30 sec
6.20 sec
6.90 sec
7.13 sec

2010-11-24 Generate password lists using Markov
chains
In
preparation for adding additional password plaintext generators to my GPU password cracker,
I prototyped a simple Markov chain plaintext generator (pwMarkov.pl).
I added it to my John scripts for good measure and am testing
to
see if there is a measurable improvement in cracking efforts now.
2010-05-18 Say goodbye to my liquid cooling system
After
my second coolant leak, it was time to remove my liquid cooling system.
It worked really well at keeping my system cool. It
was not
as effective at keeping it dry. It would not have been as
annoying if I did not have an air cooled system running two dual GPU
graphics cards and a Tesla super computer sitting under my desk at the
same time. My GPU password cracking box just hummed along
without
any overheating issues while my game system learned how to swim in low
conductivity cooling solution. So, I upgraded my case to an
Antec
1200 to match my GPU cracker and replaced my pair of ATI
4895's
with two ATI 5970's and I am back to the races. The 3DMark
numbers speak wonders about both the video cards and the difference
between running Windows XP and Windows 7.

2010-05-12 LogReporter
v1.5 is available
In
response to some feedback from Santiago Zapata, I have updated the
LogReporter.c code to enumerate and report on all active MAC and IP
addresses. Irrespective of the size of your Windows
environment,
you probably struggle with mapping actions in your
firewalls or IDS logs back to users. Stick this program in
your
login scripts and it will provide syslog records for each
login
including NETBIOS computer name, username as well as all active MAC and
IP addresses.
2010-03-19 Mining A/V logs continues to extract gold
After updating my
simple Symantec A/V log parser
I used it to convert syslog Symantec A/V logs to CSV files and loaded
the data into Advizor
Analyst. This type of graph shows interesting re-infection
patterns for individual hosts (horizontal lines), signature updates
following malware blooms (vertical patterns with the same colors) as
well as others.

The y-axis is a list of all infected machines so each horizontal line
is a single system (Host names clipped for anonymity). The color coding
is based on the name of the malware with similar names having similar
colors on the pallet. Analysis of the four solid verticals outside of
the weekly schedule scan pattern (the consistent vertical pattern
across all the plots) were four different outbreaks of a network
scanner where signature updates were loaded across all systems and the
IPS started detecting and blocking immediately. The analysis was done
to evaluate the effectiveness of an A/V deployment. The initial impact
was a clear determination that the A/V system needed some attention and
over time, the analysis was used to re-enforce the value of enabling
additional options in the A/V system. Ongoing analysis shows the tempo
of malware detects and changes to the A/V environment.
2009-10-13 LogReporter
v1.4 is available
I
needed to add support for unicode in my simple login tracker.
While poking around in the source, I added a few more
features to
make is a bit easier to use. If you have a small, medium or
large
Windows environment, you probably struggle with mapping actions in your
firewalls or IDS logs back to users. Stick this program in
your
login scripts and it will provide syslog records for each
login
including NETBIOS computer name, username, MAC address and IP.
The new version does a better job with long and unicode
netbios
names and allows you to specify your loghost by name or IP address.
2009-09-21 A/V logs can help you find troubled
systems
I
was culling through the logs on one of my systems the other day and
realized that I was getting a fair amount of alerts from my Symantec
A/V servers. At first, I was not interested in what malware
was
being detected and cleaned but it got me thinking about what
interesting patterns existed. I suspected that the majority
of
malware infections were caused by a minority of users as most malware
these days require some user action. To test this theory I
wrote
a simple parser
to convert the logs to something that I could push into
a visualizer
and started looking for interesting patterns.

Above
is a histogram plotting A/V detects over time. Each dot is an
piece of malware color coded by host. Horizontal patterns are
a
large quantity of the same piece of malware and vertical lines show
patterns in the A/V detections indicating a schedule for scanning.
This was helpful in deducing the infection and detection
patterns
but not very useful for mapping infections to individual hosts.

This heat map is much more interesting as it shows that a small number
of systems have a disproportionate
number of detected infections. About 50 systems have more
than
3,000 detected pieces of malware while the rest average just two.
This gives the admin teams a short list of systems that they
can
focus on both with technical as well as awareness based remediation.
2009-05-21 I just switched from air to liquid cooling
After
many years of dreading summer and the system over temp lock-ups I just
made the leap into liquid cooling. I had resisted for the
last
couple of years because the cost of entry in money and time was just
too much. After a couple of days to reading on the net I
decided
that it was too simple and cheap, that waiting any longer was silly.

So
far, I am running 32c on my CPU and 35c on both of my GPUs on fan speed
4 of 10. This is not bad considering ambient is 46c and my
CPU
averaged around 50c on air. I will play with this for a
couple
of weeks while I over clock this and that. Once I have
gathered
more data, I will switch from a serial to a parallel flow configuration
and see if that makes any significant difference.
After running the Intel
over clocking utility and installing 3DMark I have a
snapshot of what my new performance is with little tweaking.

2009-04-07 QuickParser
(quickparser) v0.4 released
I
just posted an updated version of QuickParser to SourceForge.
There are some minor bug fixes and changes to the parser to
better support generic logs with key=value pairs.
2008-12-27 Projects on my short list
Of
the long list of projects that I am ignoring most of the time and
banging on when I have a free moment, there are a few that I am putting
on my resolution list to get finished in 2009!
- Log tokenizer, compressor and decompressor
- PDF carver (pdfcarver)
- Network ACL Builder (wirespy)
- IM Sniffer (imspy)
- Forensic packet archiver (The
Wiretapper's Toolkit - TWT)
- DNS Sniffer (pdnsd)
There are also a few ideas that I need to flesh out on paper in 2009
(we shall see how I do).
- "Distrust Engineering", finding the bad guys without
signatures.
- "The State of Information Security Data
Visualization", a Marcus style rant.
- "The
11th Domain of Information Security", how to achieve long term
improvement of the security of your organization by creating a
sustainable information security practice.
2008-08-21 QuickParser
(quickparser) v0.3
In
the spirit of sharing and in the hopes of prodding a co-conspirator
into finishing *his* better, stronger and faster parser, I have
released the source to my regex-less log parser specifically for
Juniper (Netscreen) firewall logs.
2008-07-01 PiRAT
v0.2
I
just upgraded my Nokia N800 to a N810 and it is time to update my tool
chain for OS2008. The new version will sport all of my
favorite
tools including NMAP,
AMAP,
xprobe2,
NBTScan,
NetCat,
Hping2, dsniff,
p0f,
hydra,
John the
Ripper, Snort,
TCPDump,
Metasploit,
Kismet,
Wireshark
(a real pain to build) and many more.
2008-06-19 Transitive Distrust
I have
watched our capability to detect threats degrade year after year as our
adversaries invest more and more time and effort in the pursuit of
stealthiness. As with all arms races, the winner is the faction with
the deepest pockets and lowest overhead. In the corporate
world,
that is a guarantee that the adversaries will always win. I
have
been toying with a different paradigm to identifying threats called
transitive distrust, or as a good friend of mine commented, trust
engineering.
Thesis:
To
test this, I am building with the help of some friends, a system of
instrumentation that applies a simple set of 30-40 rules to all systems
that interact with a given network. Once the rules are
applied, a
trust/distrust map is compiled. This is a very effective
filter
to separate the trusted, and therefore not interesting, from the
untrusted
The system can run
constantly, correcting the evaluated trust/distrust as the data points
change. Distrust
degrades over time so a system that was previously untrusted but no
longer exhibits these traits will become more trusted.
2008-05-31 Monitoring and logging removable media
access with OS/X
I wrongly assumed
that it would
be simple to find an intellectual property (IP) leakage monitoring tool
for removable media on OS/X. It is unfortunate that the
abundance
of this type of tool on Windows has not rubbed off on Mac.
That
said, I hacked together a volume monitoring daemon (vmd)
to provide logging of file activity on removable devices on systems
running OS/X. It is the poor mans solution to the problem.
It uses syslog, so it is possible to have all of your Mac's
point
to a central syslog server and gain arms length auditing of removable
media across all of your OS/X based systems with this little daemon.
A word of caution, I used the fsevents functionality of
10.4 and 10.5 which is not a standard hook for applications.
So don't be surprised if this stops working in a future
version of
OS/X.
2008-04-26 Malware detection through data visualization
Raffael over at secvis.org has been
working to improve the overall state of information security data
visualization. Along with logging, data visualization has
been a
pet project of mine for several years. I have, from time to
time
used visualization to filter through large volumes of data looking for
intruders, malware and data breaches.
I have been trying to find a way to go through firewall logs at a large
corporation where a days worth of traffic equates to 25Gb of
uncompressed logs
and mapping portions of the logs to simple 2D graphs helps
to point out obvious and sometimes subtle anomalies.
When you plot the destination IP address as an integer over time, many
interesting patterns are highlighted. Even more interesting than the horizontal patterns indicating
continuous traffic to specific IP addresses are the vertical clusters
with regularly repeating frequencies.
Even more interesting than the horizontal patterns indicating
continuous traffic to specific IP addresses are the vertical clusters
with regularly repeating frequencies.
Next, a plot of the same data using the destination port number over
time points to obvious port scanning in the form of diagonal
lines as well as odd patterns that sync with the previous destination
IP address plot. 
The last plot of source ports over time points to crafted packets.
Normal sockets allocated through the operating system will
have
positively incrementing source ports for each new connection.
Look for the horizontal lines and you have most likely found
tools
that are not using the operating system to instantiate new sockets.
To me, this screams packet crafting. 
All of these graphs were created by parsing firewalls logs using a perl script and
loading them into Advizor
Analyst.
Web server logs are another source of interesting data if you are able
to separate the wheat from the chaff. Apache2Dot.pl
is a small script that makes clear diagrams of website interactions.
2008-03-19 Sumo
vs. Judo
Over the course of my
career, it has become clear to me that Japan's national
sport offers a perfect analogy for the current state of
information security.

2008-03-18 Is it time for Computer Access
License Agreements?

Now that the US Federal Government is regularly seizing, coping and
snooping into the computers of US Citizens returning home, what can we
do to protect the privacy that we hold dear? The most obvious
response is to encrypt your drives using whatever tools you deem
appropriate. I had considered a "FiST
US Customs" campaign, but I suppose that would not be very
professional. I had also considered implementing some
anti-forensic countermeasures on my computers. A simple
change to
one of the many open source disk wipers could fill your unallocated and
slack space with billions of partial GIF
images. That sure would make going through the preview in EnCASE a bit more
tedious. And I suppose there are even more 'active'
countermeasures available to those who are not squeamish about fighting
back. After all, I have nothing to hide, and its not my job
to
make it easy for Law Enforcement to do theirs. Then it
occurred
to me as I was ranting to a fellow infosec practitioner. What
we
need is the equivalent of a EULA for our computers. Something
that warns off would-be snoopers who decide to look at our computers
without a warrant. I suppose putting one of these stickers on
your computer and your hard drives is just asking for them to be
confiscated, never to be seen again. But it sure would make a
great story.
2008-03-14 DPS for life!






Distance makes the
heart grow fonder.
2008-01-24 Passive syslog monitor v1.2.1 (psmd) has been
released
After many days of
pushing
hundreds of gigabytes of data through it, the new version of psmd
offers many bug fixes and a new TCP reassembler which notes lost log
data due to dropped packets. Along with the new features,
psmd
still offers many others:
- Passive syslog monitoring (no listening ports)
- Support for syslog over UDP and TCP (syslog-ng)
- Archiving of all log data with proper time stamps,
source and dest MAC and IP address
- MD5 and SHA1 hashing of all archived logs
- Forwarding of syslog data with or without forged
source IP addresses
- TIMEMARK insertion to handle time zone and time skew
issues
2007-09-25 Sending a shout out to my com padre
Further continuing
the South
Park theme, I bring you yet another image of a fellow student of Sun
Tsu and InfoSec practitioner. Can you guess who it is?

I just want to know one thing, where is my cut of the shirt
action Tom?
2007-09-22 Regexless log parsing (quickparser)
A co-conspirator
and I have been
building some log analysis tools. To feed data to the tools,
we
needed to convert log files into a pseudo XML format. I built
a
couple of regex log parsers in perl but they were very slow.
We
have spent some time talking about other ways of parsing logs and I
cannibalized a log compression tool that I had built using regexless
parsing and found out that it is pretty fast. By fast I am
talking 2.6M lines per minute on a single processor 2.5GHz PC running
linux and 950K lines per minute on a SunBlade 2000 with 1GHz processors.
Check out my quickparser,
it chews up syslog data from Netscreen firewalls. It should
work
properly with any syslog source that uses key/value pairs separated by
a '='.
2007-08-17 "Better out than in, that's what
I always say!" -Shrek
InfoSec is from
Pluto, NetOps is from Jupiter
As
the tenth largest body orbiting our sun, Pluto has in recent years been
center stage to heated discussion about what makes a planet.
Living on
Pluto as it spins around its eccentric orbit at a chilly 29 AU to a
really chilly 49 AU from our Sun would be quite a challenge.
It's cold
and lonely and most people don't even consider Pluto a planet including
the IAU which on August 24th, 2006 relegated Pluto to 'dwarf planet'
status. It is surprisingly similar to the life as an InfoSec
professional. They are center stage to heated discussions
about the
significance, priority and impact of information security on
organizations. Aside from government and financial circles,
InfoSec is
at best an ugly stepchild and at worst is the bastard child of an
adulterous relationship. To the rest of the world, information security
is the curse of 'due diligence and care' that is resisted, ignored and
hated with vim and vigor likened to paying taxes. In short,
information security is the group that tries to make organizations do
silly things that cost too much and delay projects for no good reason
because "security breaches only happen to the other guy, not us".
The fifth planet from our Sun, Jupiter, stacks up as the
largest body in our solar system at 2 ½ times more massive
that all the
other planets put together. Jupiter keeps showing up in the
press with
missions like Voyager, Cassini and Galileo. If that
was not enough of
a spotlight, consider the Shoemaker-Levy 9 Impacts in July of
1994.
Jupiter is big, bright and full of hydrogen. Everybody knows
what
Jupiter looks like and we thank Jupiter for its gravitational pull, we
all prefer to have things hit Jupiter instead of us. Network
operations, like Jupiter, gets lots of visibility, is generally large
in comparison to other operational bodies and is full of an amazingly
diverse class of gases. And we all know to make a bee-line to
NetOps
when we can't surf the Internet.
Putting aside the above analogies, there are some fundamental
differences between InfoSec and NetOps and over the years I have
struggled to understand those differences as a way to improve my
interactions with my family on Jupiter. At its most
fundamental level,
the difference between "network" people and "security" people is that
one is focused on ensuring that packets move and the other
isn't. I
will leave ascribing the correct labels to you, the reader.
This fundamental schism is surprisingly wide and deep. And,
we are talking astronomic units (AU) here, not Grand Canyon
distances.
Countless times, I have gone to my brothers and sisters on Jupiter
asking for help in reducing the 'attack surface' of a problem and time
and time again, I have received feedback and lumps. With each
tongue-lashing and stroke I have heard "We don't have time or
resources". For a long time, I assumed that part of my family
was just
lazy.
The Epiphany came to me last week, NetOps is from Jupiter, not
my home town over on Pluto. When I ask network operations to
install
an ACL or firewall, they resist. Not out of laziness but as
an
instinctive response built into the very fabric of each resident of
Jupiter. Asking to block traffic is like asking them to move
to Pluto,
which is far too small and cold. When I look at the problem,
I see it
through the eyes of a happy resident of Pluto where blocking traffic is
just a matter of simple changes to router and firewall
configurations.
Add in a little audit trail and some monitoring for giggles, and it is
a happy place for all. But when someone from Jupiter looks at
preventing packets from reaching their final destination, it is like
preventing a packet from reaching it's pre-ordained and rightful place
in the universe and the ramifications will topple everything.
Not to
mention making a mess in the holiest of places, the change control
archive.
So, consider this, the next time you endeavor to make the
journey from Pluto to Jupiter to request a packet filter, start the
conversation with "Every packet is sacred", and bring lots of photos of
home to reassure them that Pluto is not all bad, because a network
operator who turns up a firewall is actually a Plutonian on vacation in
a warmer climate.
Ron Dilley
:Plutonian
2007-07-31 Blatant C.a.S.E.
I am sorry Marcus, I just can't keep it to myself . . .

2007-07-30 Passive syslog monitor v1.0 (psmd) has been
released
Thanks to mjr for suggesting an interesting solution to the problem of
how to handle broken time in logs. By broken I mean logs from
systems without accurate time, mixed time zones and the most annoying
of all . . . daylight savings. The new version of psmd
inserts
time marks which record the time skew between log time and the time
that the log is sucked off the wire.
2007-03-22 Yet another project (PiRat)
I just picked up a Nokia
N800
with the intent to port all of my InfoSec related tools to this
ultra-small computing platform. There is a pretty well put
together development environment and a strong open source development
community branded as Maemo.
2006-09-25 ÜberAdmin has a new website
After several years of a really plain website, I decided to give up
using vi for web development and switched to a more modern tool which
was capable of making really fancy websites. Though I opted
not
to make this site much fancier than the vi version, I at least used
more than one font this time.
2006-09-18 Passive syslog monitor daemon has a new home
at SourceForge (psmd)
After tweaking on my code an hour at a time over the last year, I have
finally been pushed and prodded enough to actually release it to the
public. As I am not a programmer by trade and know just how
much
gum and how many rubber bands are used to hold it together, I do so
with a bit of reservation. With all the messages on the logs
mailing list about signing syslog, what else could I do?
2015-07-26 Freshening The Wiretappers Toolkit (TWT)
I have been modernizing The Wiretappers Toolkit (TWT)
and just finished standing up a new packet vacuum for my home office. CappuccinoPC makes a nice small form factor fanless machine.
The machine includes an Atom D525, 4Gb Ram, 4xUSB, 4x1Gb Ethernet, RS232 and room for one 2.5" HDD:

I added a 2TB HDD for $110 and an extra external heat-sink for $8. Out the door for $440.

2014-12-03 Selling Packet Vacuums Door-to-Door
Thanks to the IANS Faculty for inviting me to speak
about my second most favorite incident response tool (Packet Vacuums)!
2014-09-18 Enough with the BSoD!
I gave up in frustration at my Intel Extreme MB with the BSoD, hangs, thermal events and on and on. So, time for an upgrade! I switched to an ASUS Rampage Black Edition. Along with the MB, CPU and Ram, I upgraded my SDD and HDD configuration. Boot speed times are as follows:.
| 2 x 500Gb Samsung 840 EVO SSD (Raid-0) | Sample 1 | Sample 2 | Sample 3 | Average |
| Boot to Login | 27.70 sec | 25.80 sec | 27.00 sec | 26.30 sec |
| Login to Desktop | 3.40 sec | 2.50 sec | 2.70 sec | 2.70 sec |
| Login to Chrome Open/Page Loaded | 4.50 sec | 4.10 sec | 4.10 sec | 4.20 sec |
Now the really important thing is how does this new computer run for gaming? Well, here is the benchmark for the default motherboard confuguration (no overclocking):
2013-12-31 Log Templater (tmpltr) v0.6 is now available
I have been laying some ground work for implementing log chain templates in the next version of Log Templater.
Part of that work includes adding support for more field types (IPv4, IPv6, MAC Address and HEX numbers).
These changes clean up the templates and make it simpler and faster to find some key data when responding to
a threat.
2013-04-03 Geeking out with Marcus Ranum - Take 2
My last session
with Marcus in February may have lacked "Marcus", but there was enough participation and positive feedback that he
asked me to come back and have a more detailed discussion. This time, we had a chance to dig much deeper into the topic and
came up with a couple of interesting ideas that we are now percolating on. Perhaps this will lead to a new tool in our kit.
The webcast is available and who knows what may come next.
2013-02-19 Geeking out with Marcus Ranum
I was looking forward to spending some quality
geek out
time with Marcus today talking about logging
and log analysis. Unfortunately, Marcus fell victim to the Webcast gremlins at a hotel in Germany and
was not able to join me. I still had a good time talking with Allan
about all things "logging" but I am looking forward to geeking our with Marcus some other time.
The webcast has been posted along with some takeaways.
2013-01-20 Hosting ISOI 11
I had the honor and privilege of hosting ISOI 11 in January.
There was an amazing array of speakers and topics. I can't wait for ISOI 12!
Special thanks to Dragos for the use of the secure WiFi gear.
2012-06-27 Upgraded GPU Cracker
With the recent breaches of authentication credentials around the Interwebs, I decided to upgrade my GPU
Cracker and see how it performs and how hot my office can get all at the same time. I replaced my aging
Radeon 5xxx boards with three Radeon 7970's
and one Radeon 6970. SHA1 is now running at almost 6T computations
per second using oclHashCat-Plus.
Time to port Nightengale (BaraCUDA) to OpenCL and see how she runs!

2012-02-04 Passive Proxy Daemon (pproxyd) v0.2 is now available
I have been procrastinating about building a libpcap based sniffer that reassembles web traffic and
generates Squid proxy logs for years.
I tried to use Mike Poor's "development via osmosis" trick with a couple of buddies but in the end, I was forced
to put it together in the last couple of weeks to help solve a vexing web application problem. So, in a pinch,
I pulled out the paper clips, rubber bands and chewing gum. Then I read the docs on libnids.
2012-01-17 Log Templater (tmpltr) v0.5 is now available
After some very helpful and specific feedback about the last version of tmpltr, I have added a few additions
including faux clustering for the occasion when it is handy to know what on a given log line has not changed.
There is a performance penalty for this extra processing, but not as much as I had originally expected. The
table below shows average performance metrics on a Linux VM running on an i7 @ 3.2GHz.
Log size and type
Avg. Line Len
Avg. Arg Count
Args Stored
Avg. Lines per Min
18M Line Cisco FW Log
180
32
0
12,004,023/min
18M Line Cisco FW Log (Clustered)
180
32
24,009
4,093,802/Min
11M Line Apache Access Log
246
44
0
9,453,905/Min
11M Line Apache Access Log (Clustered)
246
44
21,666
5,563,009/Min
4M Line Windows Event Log
793
90
0
2,854,123/Min
4M Line Windows Event Log (Clustered)
793
90
70,361
1,183,226/Min
In addition, I have added a greedy mode where the templater will ignore double quotes. This is very useful
when processing web server logs. In non-greedy mode, tmpltr will assume most things in between a pair of double
quotes are a single string. In greedy mode, all data will be handled the same.
2011-10-17 SSD-Spindle Hybrid
I picked up a couple of Seagate MomentusXT 500Gb
Solid State Hybrid drives to see how they stacked up to
my four 120Gb SSDs running RAID-0. I pulled out the very handy HD TunePro and
the sad fact is, configured as a RAID-0, they were no where near as fast as the pure SSD RAID-0. The linear read and the seek speed was also unpredictable.
Even worse, they did not out perform a couple of 1TB spindle drives running RAID-0 as the chart below shows.

2011-10-01 Log Templater (tmpltr) v0.3 is now available
During the last security incident that I worked on, I needed to grind through 20gb of log files looking
for any odd log lines that would indicate the point where the bad guys got in. If I had done it manually,
I would still be looking at log data. Instead, I built a tool that converted logs into pattern
templates and looked for templates that I had never seen before. This allowed me to zero in on just a
few hundred log lines out of all the data.
2011-07-29 Quick Parser (quickparser) v0.5 is now available
After re-implementing some parser code in difftree with bug
fixes and improved bounds checking, I have ported those changes back to this tool. So, I now present
the new and improved quick parser with less bugs and more bounds checking. Re-energized after touching
the code, I am working on the template based version, which will not be limited to syslog style,
key=value formatted logs.
2011-07-27 Directory Tree Differ (difftree) v0.5 is now available
I have released a new version of difftree with more features and less memory leaks.
This new version adds the ability to save directory tree state and to compare both
directories and archives of directory trees that were previously saved. In addition,
you can hash and compare files if accuracy is more important the speed.
2011-07-16 Directory Tree Differ (difftree) v0.4 is now available
While working on a security incident and fighting with tripwire and Osiris,
I gave up and wrote a fast directory diff tool to allow me to do simple
comparisons between SAN snapshots. To tool was so handy for me, I
figured I would share it.
2011-07-03 SSD Redux
After
fighting with the RAID chassis that I picked up to house my new clutch
of SSD drives I returned them all in a fit of nerd rage and downgraded
from a RAID enclosure to a simple JBOD and larger SSD drives.
I have not been disappointed:
4 x
120Gb OCZ SSD (Raid-0)
Sample
1
Sample
2
Sample
3
Average
Boot to Login
27.30 sec
27.50 sec
27.28 sec
27.28 sec
Login to Desktop
3.50 sec
3.10 sec
3.60 sec
3.40 sec
Login to
Firefox Open/Page Loaded
6.90 sec
5.40 sec
6.05 sec
6.12 sec
Using the very handy HD TunePro
utility, I was able to get a bit more imperial data about the
difference in performance between my old configuration and the new SSD
smoke-fest. Here is the read throughput and access time graph
for
the 4x120Gb OCZ Vertex II SSD (Raid-0):

That
may not look too impressive, but if you compare it to the same read
throughput and access time graph for my old 2x1Tb 7200RPM SATA II HDD
(Raid-0) configuration you will see a bit of a difference and why my
grin is from ear to ear:

2011-05-21 Power supply failure leads to faster boot
times
In
the spirit of tricking people into reading what I write, I have given
in to temptation and deliberately misled you. Yes, my old
power
supply on my Windows development system died and I was forced to
replace it today. In addition, I have improved my boot times
considerably. But the only correlation between the two is
that I
figured I would do a bit of upgrading while I had my case open to
replace the power supply. So, out with the old 850W and in
with
the new 1200W Thermaltake. Additionally, out
with the old 2 x 1TB Raid-0 boot drives and in with the new 4 x 64GB Raid-0 SSD. All
this "high speed, low drag" boot hotness in a fancy 5 1/4" chassis by Patriot. Boot
speed times are as follows:.
2
x 1TB 7200RPM HDD (Raid-0)
Sample
1
Sample
2
Sample
3
Average
Boot to Login
58.00 sec
87.80 sec
87.80 sec
77.87 sec
Login to Desktop
72.50 sec
51.40 sec
32.10 sec
52.00 sec
Login to
Firefox Open/Page Loaded
78.70 sec
63.80 sec
69.80 sec
70.77 sec
4
x 64Gb Patriot TRB SSD (Raid-0)
Sample
1
Sample
2
Sample
3
Average
Boot to Login
32.60 sec
29.40 sec
26.70 sec
29.57 sec
Login to Desktop
5.20 sec
3.40 sec
4.40 sec
4.33 sec
Login to
Firefox Open/Page Loaded
8.30 sec
6.20 sec
6.90 sec
7.13 sec

2010-11-24 Generate password lists using Markov
chains
In
preparation for adding additional password plaintext generators to my GPU password cracker,
I prototyped a simple Markov chain plaintext generator (pwMarkov.pl).
I added it to my John scripts for good measure and am testing
to
see if there is a measurable improvement in cracking efforts now.
2010-05-18 Say goodbye to my liquid cooling system
After
my second coolant leak, it was time to remove my liquid cooling system.
It worked really well at keeping my system cool. It
was not
as effective at keeping it dry. It would not have been as
annoying if I did not have an air cooled system running two dual GPU
graphics cards and a Tesla super computer sitting under my desk at the
same time. My GPU password cracking box just hummed along
without
any overheating issues while my game system learned how to swim in low
conductivity cooling solution. So, I upgraded my case to an
Antec
1200 to match my GPU cracker and replaced my pair of ATI
4895's
with two ATI 5970's and I am back to the races. The 3DMark
numbers speak wonders about both the video cards and the difference
between running Windows XP and Windows 7.

2010-05-12 LogReporter
v1.5 is available
In
response to some feedback from Santiago Zapata, I have updated the
LogReporter.c code to enumerate and report on all active MAC and IP
addresses. Irrespective of the size of your Windows
environment,
you probably struggle with mapping actions in your
firewalls or IDS logs back to users. Stick this program in
your
login scripts and it will provide syslog records for each
login
including NETBIOS computer name, username as well as all active MAC and
IP addresses.
2010-03-19 Mining A/V logs continues to extract gold
After updating my
simple Symantec A/V log parser
I used it to convert syslog Symantec A/V logs to CSV files and loaded
the data into Advizor
Analyst. This type of graph shows interesting re-infection
patterns for individual hosts (horizontal lines), signature updates
following malware blooms (vertical patterns with the same colors) as
well as others.

The y-axis is a list of all infected machines so each horizontal line
is a single system (Host names clipped for anonymity). The color coding
is based on the name of the malware with similar names having similar
colors on the pallet. Analysis of the four solid verticals outside of
the weekly schedule scan pattern (the consistent vertical pattern
across all the plots) were four different outbreaks of a network
scanner where signature updates were loaded across all systems and the
IPS started detecting and blocking immediately. The analysis was done
to evaluate the effectiveness of an A/V deployment. The initial impact
was a clear determination that the A/V system needed some attention and
over time, the analysis was used to re-enforce the value of enabling
additional options in the A/V system. Ongoing analysis shows the tempo
of malware detects and changes to the A/V environment.
2009-10-13 LogReporter
v1.4 is available
I
needed to add support for unicode in my simple login tracker.
While poking around in the source, I added a few more
features to
make is a bit easier to use. If you have a small, medium or
large
Windows environment, you probably struggle with mapping actions in your
firewalls or IDS logs back to users. Stick this program in
your
login scripts and it will provide syslog records for each
login
including NETBIOS computer name, username, MAC address and IP.
The new version does a better job with long and unicode
netbios
names and allows you to specify your loghost by name or IP address.
2009-09-21 A/V logs can help you find troubled
systems
I
was culling through the logs on one of my systems the other day and
realized that I was getting a fair amount of alerts from my Symantec
A/V servers. At first, I was not interested in what malware
was
being detected and cleaned but it got me thinking about what
interesting patterns existed. I suspected that the majority
of
malware infections were caused by a minority of users as most malware
these days require some user action. To test this theory I
wrote
a simple parser
to convert the logs to something that I could push into
a visualizer
and started looking for interesting patterns.

Above
is a histogram plotting A/V detects over time. Each dot is an
piece of malware color coded by host. Horizontal patterns are
a
large quantity of the same piece of malware and vertical lines show
patterns in the A/V detections indicating a schedule for scanning.
This was helpful in deducing the infection and detection
patterns
but not very useful for mapping infections to individual hosts.

This heat map is much more interesting as it shows that a small number
of systems have a disproportionate
number of detected infections. About 50 systems have more
than
3,000 detected pieces of malware while the rest average just two.
This gives the admin teams a short list of systems that they
can
focus on both with technical as well as awareness based remediation.
2009-05-21 I just switched from air to liquid cooling
After
many years of dreading summer and the system over temp lock-ups I just
made the leap into liquid cooling. I had resisted for the
last
couple of years because the cost of entry in money and time was just
too much. After a couple of days to reading on the net I
decided
that it was too simple and cheap, that waiting any longer was silly.

So
far, I am running 32c on my CPU and 35c on both of my GPUs on fan speed
4 of 10. This is not bad considering ambient is 46c and my
CPU
averaged around 50c on air. I will play with this for a
couple
of weeks while I over clock this and that. Once I have
gathered
more data, I will switch from a serial to a parallel flow configuration
and see if that makes any significant difference.
After running the Intel
over clocking utility and installing 3DMark I have a
snapshot of what my new performance is with little tweaking.

2009-04-07 QuickParser
(quickparser) v0.4 released
I
just posted an updated version of QuickParser to SourceForge.
There are some minor bug fixes and changes to the parser to
better support generic logs with key=value pairs.
2008-12-27 Projects on my short list
Of
the long list of projects that I am ignoring most of the time and
banging on when I have a free moment, there are a few that I am putting
on my resolution list to get finished in 2009!
- Log tokenizer, compressor and decompressor
- PDF carver (pdfcarver)
- Network ACL Builder (wirespy)
- IM Sniffer (imspy)
- Forensic packet archiver (The
Wiretapper's Toolkit - TWT)
- DNS Sniffer (pdnsd)
There are also a few ideas that I need to flesh out on paper in 2009
(we shall see how I do).
- "Distrust Engineering", finding the bad guys without
signatures.
- "The State of Information Security Data
Visualization", a Marcus style rant.
- "The
11th Domain of Information Security", how to achieve long term
improvement of the security of your organization by creating a
sustainable information security practice.
2008-08-21 QuickParser
(quickparser) v0.3
In
the spirit of sharing and in the hopes of prodding a co-conspirator
into finishing *his* better, stronger and faster parser, I have
released the source to my regex-less log parser specifically for
Juniper (Netscreen) firewall logs.
2008-07-01 PiRAT
v0.2
I
just upgraded my Nokia N800 to a N810 and it is time to update my tool
chain for OS2008. The new version will sport all of my
favorite
tools including NMAP,
AMAP,
xprobe2,
NBTScan,
NetCat,
Hping2, dsniff,
p0f,
hydra,
John the
Ripper, Snort,
TCPDump,
Metasploit,
Kismet,
Wireshark
(a real pain to build) and many more.
2008-06-19 Transitive Distrust
I have
watched our capability to detect threats degrade year after year as our
adversaries invest more and more time and effort in the pursuit of
stealthiness. As with all arms races, the winner is the faction with
the deepest pockets and lowest overhead. In the corporate
world,
that is a guarantee that the adversaries will always win. I
have
been toying with a different paradigm to identifying threats called
transitive distrust, or as a good friend of mine commented, trust
engineering.
Thesis:
To
test this, I am building with the help of some friends, a system of
instrumentation that applies a simple set of 30-40 rules to all systems
that interact with a given network. Once the rules are
applied, a
trust/distrust map is compiled. This is a very effective
filter
to separate the trusted, and therefore not interesting, from the
untrusted
The system can run
constantly, correcting the evaluated trust/distrust as the data points
change. Distrust
degrades over time so a system that was previously untrusted but no
longer exhibits these traits will become more trusted.
2008-05-31 Monitoring and logging removable media
access with OS/X
I wrongly assumed
that it would
be simple to find an intellectual property (IP) leakage monitoring tool
for removable media on OS/X. It is unfortunate that the
abundance
of this type of tool on Windows has not rubbed off on Mac.
That
said, I hacked together a volume monitoring daemon (vmd)
to provide logging of file activity on removable devices on systems
running OS/X. It is the poor mans solution to the problem.
It uses syslog, so it is possible to have all of your Mac's
point
to a central syslog server and gain arms length auditing of removable
media across all of your OS/X based systems with this little daemon.
A word of caution, I used the fsevents functionality of
10.4 and 10.5 which is not a standard hook for applications.
So don't be surprised if this stops working in a future
version of
OS/X.
2008-04-26 Malware detection through data visualization
Raffael over at secvis.org has been
working to improve the overall state of information security data
visualization. Along with logging, data visualization has
been a
pet project of mine for several years. I have, from time to
time
used visualization to filter through large volumes of data looking for
intruders, malware and data breaches.
I have been trying to find a way to go through firewall logs at a large
corporation where a days worth of traffic equates to 25Gb of
uncompressed logs
and mapping portions of the logs to simple 2D graphs helps
to point out obvious and sometimes subtle anomalies.
When you plot the destination IP address as an integer over time, many
interesting patterns are highlighted. Even more interesting than the horizontal patterns indicating
continuous traffic to specific IP addresses are the vertical clusters
with regularly repeating frequencies.
Even more interesting than the horizontal patterns indicating
continuous traffic to specific IP addresses are the vertical clusters
with regularly repeating frequencies.
Next, a plot of the same data using the destination port number over
time points to obvious port scanning in the form of diagonal
lines as well as odd patterns that sync with the previous destination
IP address plot. 
The last plot of source ports over time points to crafted packets.
Normal sockets allocated through the operating system will
have
positively incrementing source ports for each new connection.
Look for the horizontal lines and you have most likely found
tools
that are not using the operating system to instantiate new sockets.
To me, this screams packet crafting. 
All of these graphs were created by parsing firewalls logs using a perl script and
loading them into Advizor
Analyst.
Web server logs are another source of interesting data if you are able
to separate the wheat from the chaff. Apache2Dot.pl
is a small script that makes clear diagrams of website interactions.
2008-03-19 Sumo
vs. Judo
Over the course of my
career, it has become clear to me that Japan's national
sport offers a perfect analogy for the current state of
information security.

2008-03-18 Is it time for Computer Access
License Agreements?

Now that the US Federal Government is regularly seizing, coping and
snooping into the computers of US Citizens returning home, what can we
do to protect the privacy that we hold dear? The most obvious
response is to encrypt your drives using whatever tools you deem
appropriate. I had considered a "FiST
US Customs" campaign, but I suppose that would not be very
professional. I had also considered implementing some
anti-forensic countermeasures on my computers. A simple
change to
one of the many open source disk wipers could fill your unallocated and
slack space with billions of partial GIF
images. That sure would make going through the preview in EnCASE a bit more
tedious. And I suppose there are even more 'active'
countermeasures available to those who are not squeamish about fighting
back. After all, I have nothing to hide, and its not my job
to
make it easy for Law Enforcement to do theirs. Then it
occurred
to me as I was ranting to a fellow infosec practitioner. What
we
need is the equivalent of a EULA for our computers. Something
that warns off would-be snoopers who decide to look at our computers
without a warrant. I suppose putting one of these stickers on
your computer and your hard drives is just asking for them to be
confiscated, never to be seen again. But it sure would make a
great story.
2008-03-14 DPS for life!






Distance makes the
heart grow fonder.
2008-01-24 Passive syslog monitor v1.2.1 (psmd) has been
released
After many days of
pushing
hundreds of gigabytes of data through it, the new version of psmd
offers many bug fixes and a new TCP reassembler which notes lost log
data due to dropped packets. Along with the new features,
psmd
still offers many others:
- Passive syslog monitoring (no listening ports)
- Support for syslog over UDP and TCP (syslog-ng)
- Archiving of all log data with proper time stamps,
source and dest MAC and IP address
- MD5 and SHA1 hashing of all archived logs
- Forwarding of syslog data with or without forged
source IP addresses
- TIMEMARK insertion to handle time zone and time skew
issues
2007-09-25 Sending a shout out to my com padre
Further continuing
the South
Park theme, I bring you yet another image of a fellow student of Sun
Tsu and InfoSec practitioner. Can you guess who it is?

I just want to know one thing, where is my cut of the shirt
action Tom?
2007-09-22 Regexless log parsing (quickparser)
A co-conspirator
and I have been
building some log analysis tools. To feed data to the tools,
we
needed to convert log files into a pseudo XML format. I built
a
couple of regex log parsers in perl but they were very slow.
We
have spent some time talking about other ways of parsing logs and I
cannibalized a log compression tool that I had built using regexless
parsing and found out that it is pretty fast. By fast I am
talking 2.6M lines per minute on a single processor 2.5GHz PC running
linux and 950K lines per minute on a SunBlade 2000 with 1GHz processors.
Check out my quickparser,
it chews up syslog data from Netscreen firewalls. It should
work
properly with any syslog source that uses key/value pairs separated by
a '='.
2007-08-17 "Better out than in, that's what
I always say!" -Shrek
InfoSec is from
Pluto, NetOps is from Jupiter
As
the tenth largest body orbiting our sun, Pluto has in recent years been
center stage to heated discussion about what makes a planet.
Living on
Pluto as it spins around its eccentric orbit at a chilly 29 AU to a
really chilly 49 AU from our Sun would be quite a challenge.
It's cold
and lonely and most people don't even consider Pluto a planet including
the IAU which on August 24th, 2006 relegated Pluto to 'dwarf planet'
status. It is surprisingly similar to the life as an InfoSec
professional. They are center stage to heated discussions
about the
significance, priority and impact of information security on
organizations. Aside from government and financial circles,
InfoSec is
at best an ugly stepchild and at worst is the bastard child of an
adulterous relationship. To the rest of the world, information security
is the curse of 'due diligence and care' that is resisted, ignored and
hated with vim and vigor likened to paying taxes. In short,
information security is the group that tries to make organizations do
silly things that cost too much and delay projects for no good reason
because "security breaches only happen to the other guy, not us".
The fifth planet from our Sun, Jupiter, stacks up as the
largest body in our solar system at 2 ½ times more massive
that all the
other planets put together. Jupiter keeps showing up in the
press with
missions like Voyager, Cassini and Galileo. If that
was not enough of
a spotlight, consider the Shoemaker-Levy 9 Impacts in July of
1994.
Jupiter is big, bright and full of hydrogen. Everybody knows
what
Jupiter looks like and we thank Jupiter for its gravitational pull, we
all prefer to have things hit Jupiter instead of us. Network
operations, like Jupiter, gets lots of visibility, is generally large
in comparison to other operational bodies and is full of an amazingly
diverse class of gases. And we all know to make a bee-line to
NetOps
when we can't surf the Internet.
Putting aside the above analogies, there are some fundamental
differences between InfoSec and NetOps and over the years I have
struggled to understand those differences as a way to improve my
interactions with my family on Jupiter. At its most
fundamental level,
the difference between "network" people and "security" people is that
one is focused on ensuring that packets move and the other
isn't. I
will leave ascribing the correct labels to you, the reader.
This fundamental schism is surprisingly wide and deep. And,
we are talking astronomic units (AU) here, not Grand Canyon
distances.
Countless times, I have gone to my brothers and sisters on Jupiter
asking for help in reducing the 'attack surface' of a problem and time
and time again, I have received feedback and lumps. With each
tongue-lashing and stroke I have heard "We don't have time or
resources". For a long time, I assumed that part of my family
was just
lazy.
The Epiphany came to me last week, NetOps is from Jupiter, not
my home town over on Pluto. When I ask network operations to
install
an ACL or firewall, they resist. Not out of laziness but as
an
instinctive response built into the very fabric of each resident of
Jupiter. Asking to block traffic is like asking them to move
to Pluto,
which is far too small and cold. When I look at the problem,
I see it
through the eyes of a happy resident of Pluto where blocking traffic is
just a matter of simple changes to router and firewall
configurations.
Add in a little audit trail and some monitoring for giggles, and it is
a happy place for all. But when someone from Jupiter looks at
preventing packets from reaching their final destination, it is like
preventing a packet from reaching it's pre-ordained and rightful place
in the universe and the ramifications will topple everything.
Not to
mention making a mess in the holiest of places, the change control
archive.
So, consider this, the next time you endeavor to make the
journey from Pluto to Jupiter to request a packet filter, start the
conversation with "Every packet is sacred", and bring lots of photos of
home to reassure them that Pluto is not all bad, because a network
operator who turns up a firewall is actually a Plutonian on vacation in
a warmer climate.
Ron Dilley
:Plutonian
2007-07-31 Blatant C.a.S.E.
I am sorry Marcus, I just can't keep it to myself . . .

2007-07-30 Passive syslog monitor v1.0 (psmd) has been
released
Thanks to mjr for suggesting an interesting solution to the problem of
how to handle broken time in logs. By broken I mean logs from
systems without accurate time, mixed time zones and the most annoying
of all . . . daylight savings. The new version of psmd
inserts
time marks which record the time skew between log time and the time
that the log is sucked off the wire.
2007-03-22 Yet another project (PiRat)
I just picked up a Nokia
N800
with the intent to port all of my InfoSec related tools to this
ultra-small computing platform. There is a pretty well put
together development environment and a strong open source development
community branded as Maemo.
2006-09-25 ÜberAdmin has a new website
After several years of a really plain website, I decided to give up
using vi for web development and switched to a more modern tool which
was capable of making really fancy websites. Though I opted
not
to make this site much fancier than the vi version, I at least used
more than one font this time.
2006-09-18 Passive syslog monitor daemon has a new home
at SourceForge (psmd)
After tweaking on my code an hour at a time over the last year, I have
finally been pushed and prodded enough to actually release it to the
public. As I am not a programmer by trade and know just how
much
gum and how many rubber bands are used to hold it together, I do so
with a bit of reservation. With all the messages on the logs
mailing list about signing syslog, what else could I do?
The webcast is available and who knows what may come next.
The webcast has been posted along with some takeaways.
Special thanks to Dragos for the use of the secure WiFi gear.

| Log size and type | Avg. Line Len | Avg. Arg Count | Args Stored | Avg. Lines per Min |
| 18M Line Cisco FW Log | 180 | 32 | 0 | 12,004,023/min |
| 18M Line Cisco FW Log (Clustered) | 180 | 32 | 24,009 | 4,093,802/Min |
| 11M Line Apache Access Log | 246 | 44 | 0 | 9,453,905/Min | 11M Line Apache Access Log (Clustered) | 246 | 44 | 21,666 | 5,563,009/Min | 4M Line Windows Event Log | 793 | 90 | 0 | 2,854,123/Min | 4M Line Windows Event Log (Clustered) | 793 | 90 | 70,361 | 1,183,226/Min |
In addition, I have added a greedy mode where the templater will ignore double quotes. This is very useful when processing web server logs. In non-greedy mode, tmpltr will assume most things in between a pair of double quotes are a single string. In greedy mode, all data will be handled the same.

2011-10-01 Log Templater (tmpltr) v0.3 is now available
During the last security incident that I worked on, I needed to grind through 20gb of log files looking for any odd log lines that would indicate the point where the bad guys got in. If I had done it manually, I would still be looking at log data. Instead, I built a tool that converted logs into pattern templates and looked for templates that I had never seen before. This allowed me to zero in on just a few hundred log lines out of all the data.
2011-07-29 Quick Parser (quickparser) v0.5 is now available
After re-implementing some parser code in difftree with bug fixes and improved bounds checking, I have ported those changes back to this tool. So, I now present the new and improved quick parser with less bugs and more bounds checking. Re-energized after touching the code, I am working on the template based version, which will not be limited to syslog style, key=value formatted logs.
2011-07-27 Directory Tree Differ (difftree) v0.5 is now available
I have released a new version of difftree with more features and less memory leaks. This new version adds the ability to save directory tree state and to compare both directories and archives of directory trees that were previously saved. In addition, you can hash and compare files if accuracy is more important the speed.
2011-07-16 Directory Tree Differ (difftree) v0.4 is now available
While working on a security incident and fighting with tripwire and Osiris, I gave up and wrote a fast directory diff tool to allow me to do simple comparisons between SAN snapshots. To tool was so handy for me, I figured I would share it.
2011-07-03 SSD Redux
After fighting with the RAID chassis that I picked up to house my new clutch of SSD drives I returned them all in a fit of nerd rage and downgraded from a RAID enclosure to a simple JBOD and larger SSD drives. I have not been disappointed:
| 4 x 120Gb OCZ SSD (Raid-0) | Sample 1 | Sample 2 | Sample 3 | Average |
| Boot to Login | 27.30 sec | 27.50 sec | 27.28 sec | 27.28 sec |
| Login to Desktop | 3.50 sec | 3.10 sec | 3.60 sec | 3.40 sec |
| Login to Firefox Open/Page Loaded | 6.90 sec | 5.40 sec | 6.05 sec | 6.12 sec |
Using the very handy HD TunePro utility, I was able to get a bit more imperial data about the difference in performance between my old configuration and the new SSD smoke-fest. Here is the read throughput and access time graph for the 4x120Gb OCZ Vertex II SSD (Raid-0):

2011-05-21 Power supply failure leads to faster boot times
In the spirit of tricking people into reading what I write, I have given in to temptation and deliberately misled you. Yes, my old power supply on my Windows development system died and I was forced to replace it today. In addition, I have improved my boot times considerably. But the only correlation between the two is that I figured I would do a bit of upgrading while I had my case open to replace the power supply. So, out with the old 850W and in with the new 1200W Thermaltake. Additionally, out with the old 2 x 1TB Raid-0 boot drives and in with the new 4 x 64GB Raid-0 SSD. All this "high speed, low drag" boot hotness in a fancy 5 1/4" chassis by Patriot. Boot speed times are as follows:.
| 2 x 1TB 7200RPM HDD (Raid-0) | Sample 1 | Sample 2 | Sample 3 | Average |
| Boot to Login | 58.00 sec | 87.80 sec | 87.80 sec | 77.87 sec |
| Login to Desktop | 72.50 sec | 51.40 sec | 32.10 sec | 52.00 sec |
| Login to Firefox Open/Page Loaded | 78.70 sec | 63.80 sec | 69.80 sec | 70.77 sec |
| 4 x 64Gb Patriot TRB SSD (Raid-0) | Sample 1 | Sample 2 | Sample 3 | Average |
| Boot to Login | 32.60 sec | 29.40 sec | 26.70 sec | 29.57 sec |
| Login to Desktop | 5.20 sec | 3.40 sec | 4.40 sec | 4.33 sec |
| Login to Firefox Open/Page Loaded | 8.30 sec | 6.20 sec | 6.90 sec | 7.13 sec |
2010-11-24 Generate password lists using Markov chains
In preparation for adding additional password plaintext generators to my GPU password cracker, I prototyped a simple Markov chain plaintext generator (pwMarkov.pl). I added it to my John scripts for good measure and am testing to see if there is a measurable improvement in cracking efforts now.
2010-05-18 Say goodbye to my liquid cooling system
After my second coolant leak, it was time to remove my liquid cooling system. It worked really well at keeping my system cool. It was not as effective at keeping it dry. It would not have been as annoying if I did not have an air cooled system running two dual GPU graphics cards and a Tesla super computer sitting under my desk at the same time. My GPU password cracking box just hummed along without any overheating issues while my game system learned how to swim in low conductivity cooling solution. So, I upgraded my case to an Antec 1200 to match my GPU cracker and replaced my pair of ATI 4895's with two ATI 5970's and I am back to the races. The 3DMark numbers speak wonders about both the video cards and the difference between running Windows XP and Windows 7.
2010-05-12 LogReporter v1.5 is available
In response to some feedback from Santiago Zapata, I have updated the LogReporter.c code to enumerate and report on all active MAC and IP addresses. Irrespective of the size of your Windows environment, you probably struggle with mapping actions in your firewalls or IDS logs back to users. Stick this program in your login scripts and it will provide syslog records for each login including NETBIOS computer name, username as well as all active MAC and IP addresses.
2010-03-19 Mining A/V logs continues to extract gold
After updating my simple Symantec A/V log parser I used it to convert syslog Symantec A/V logs to CSV files and loaded the data into Advizor Analyst. This type of graph shows interesting re-infection patterns for individual hosts (horizontal lines), signature updates following malware blooms (vertical patterns with the same colors) as well as others.

The y-axis is a list of all infected machines so each horizontal line is a single system (Host names clipped for anonymity). The color coding is based on the name of the malware with similar names having similar colors on the pallet. Analysis of the four solid verticals outside of the weekly schedule scan pattern (the consistent vertical pattern across all the plots) were four different outbreaks of a network scanner where signature updates were loaded across all systems and the IPS started detecting and blocking immediately. The analysis was done to evaluate the effectiveness of an A/V deployment. The initial impact was a clear determination that the A/V system needed some attention and over time, the analysis was used to re-enforce the value of enabling additional options in the A/V system. Ongoing analysis shows the tempo of malware detects and changes to the A/V environment.
2009-10-13 LogReporter v1.4 is available
I needed to add support for unicode in my simple login tracker. While poking around in the source, I added a few more features to make is a bit easier to use. If you have a small, medium or large Windows environment, you probably struggle with mapping actions in your firewalls or IDS logs back to users. Stick this program in your login scripts and it will provide syslog records for each login including NETBIOS computer name, username, MAC address and IP. The new version does a better job with long and unicode netbios names and allows you to specify your loghost by name or IP address.
2009-09-21 A/V logs can help you find troubled systems
I was culling through the logs on one of my systems the other day and realized that I was getting a fair amount of alerts from my Symantec A/V servers. At first, I was not interested in what malware was being detected and cleaned but it got me thinking about what interesting patterns existed. I suspected that the majority of malware infections were caused by a minority of users as most malware these days require some user action. To test this theory I wrote a simple parser to convert the logs to something that I could push into a visualizer and started looking for interesting patterns.

This heat map is much more interesting as it shows that a small number of systems have a disproportionate number of detected infections. About 50 systems have more than 3,000 detected pieces of malware while the rest average just two. This gives the admin teams a short list of systems that they can focus on both with technical as well as awareness based remediation.
2009-05-21 I just switched from air to liquid cooling
After many years of dreading summer and the system over temp lock-ups I just made the leap into liquid cooling. I had resisted for the last couple of years because the cost of entry in money and time was just too much. After a couple of days to reading on the net I decided that it was too simple and cheap, that waiting any longer was silly.

So far, I am running 32c on my CPU and 35c on both of my GPUs on fan speed 4 of 10. This is not bad considering ambient is 46c and my CPU averaged around 50c on air. I will play with this for a couple of weeks while I over clock this and that. Once I have gathered more data, I will switch from a serial to a parallel flow configuration and see if that makes any significant difference.
After running the Intel over clocking utility and installing 3DMark I have a snapshot of what my new performance is with little tweaking.

2009-04-07 QuickParser (quickparser) v0.4 released
I just posted an updated version of QuickParser to SourceForge. There are some minor bug fixes and changes to the parser to better support generic logs with key=value pairs.
2008-12-27 Projects on my short list
Of the long list of projects that I am ignoring most of the time and banging on when I have a free moment, there are a few that I am putting on my resolution list to get finished in 2009!
- Log tokenizer, compressor and decompressor
- PDF carver (pdfcarver)
- Network ACL Builder (wirespy)
- IM Sniffer (imspy)
- Forensic packet archiver (The Wiretapper's Toolkit - TWT)
- DNS Sniffer (pdnsd)
- "Distrust Engineering", finding the bad guys without signatures.
- "The State of Information Security Data Visualization", a Marcus style rant.
- "The 11th Domain of Information Security", how to achieve long term improvement of the security of your organization by creating a sustainable information security practice.
2008-08-21 QuickParser (quickparser) v0.3
In the spirit of sharing and in the hopes of prodding a co-conspirator into finishing *his* better, stronger and faster parser, I have released the source to my regex-less log parser specifically for Juniper (Netscreen) firewall logs.
2008-07-01 PiRAT v0.2
I just upgraded my Nokia N800 to a N810 and it is time to update my tool chain for OS2008. The new version will sport all of my favorite tools including NMAP, AMAP, xprobe2, NBTScan, NetCat, Hping2, dsniff, p0f, hydra, John the Ripper, Snort, TCPDump, Metasploit, Kismet, Wireshark (a real pain to build) and many more.
2008-06-19 Transitive Distrust
I have watched our capability to detect threats degrade year after year as our adversaries invest more and more time and effort in the pursuit of stealthiness. As with all arms races, the winner is the faction with the deepest pockets and lowest overhead. In the corporate world, that is a guarantee that the adversaries will always win. I have been toying with a different paradigm to identifying threats called transitive distrust, or as a good friend of mine commented, trust engineering.
Thesis:
To test this, I am building with the help of some friends, a system of instrumentation that applies a simple set of 30-40 rules to all systems that interact with a given network. Once the rules are applied, a trust/distrust map is compiled. This is a very effective filter to separate the trusted, and therefore not interesting, from the untrusted
The system can run
constantly, correcting the evaluated trust/distrust as the data points
change. Distrust
degrades over time so a system that was previously untrusted but no
longer exhibits these traits will become more trusted.
2008-05-31 Monitoring and logging removable media access with OS/X
I wrongly assumed that it would be simple to find an intellectual property (IP) leakage monitoring tool for removable media on OS/X. It is unfortunate that the abundance of this type of tool on Windows has not rubbed off on Mac. That said, I hacked together a volume monitoring daemon (vmd) to provide logging of file activity on removable devices on systems running OS/X. It is the poor mans solution to the problem. It uses syslog, so it is possible to have all of your Mac's point to a central syslog server and gain arms length auditing of removable media across all of your OS/X based systems with this little daemon. A word of caution, I used the fsevents functionality of 10.4 and 10.5 which is not a standard hook for applications. So don't be surprised if this stops working in a future version of OS/X.
2008-04-26 Malware detection through data visualization
Raffael over at secvis.org has been working to improve the overall state of information security data visualization. Along with logging, data visualization has been a pet project of mine for several years. I have, from time to time used visualization to filter through large volumes of data looking for intruders, malware and data breaches.
I have been trying to find a way to go through firewall logs at a large corporation where a days worth of traffic equates to 25Gb of uncompressed logs and mapping portions of the logs to simple 2D graphs helps to point out obvious and sometimes subtle anomalies.When you plot the destination IP address as an integer over time, many interesting patterns are highlighted.
 Even more interesting than the horizontal patterns indicating
continuous traffic to specific IP addresses are the vertical clusters
with regularly repeating frequencies.
Even more interesting than the horizontal patterns indicating
continuous traffic to specific IP addresses are the vertical clusters
with regularly repeating frequencies.Next, a plot of the same data using the destination port number over time points to obvious port scanning in the form of diagonal lines as well as odd patterns that sync with the previous destination IP address plot.

The last plot of source ports over time points to crafted packets. Normal sockets allocated through the operating system will have positively incrementing source ports for each new connection. Look for the horizontal lines and you have most likely found tools that are not using the operating system to instantiate new sockets. To me, this screams packet crafting.

All of these graphs were created by parsing firewalls logs using a perl script and loading them into Advizor Analyst.
Web server logs are another source of interesting data if you are able to separate the wheat from the chaff. Apache2Dot.pl is a small script that makes clear diagrams of website interactions.
2008-03-19 Sumo vs. Judo
Over the course of my career, it has become clear to me that Japan's national sport offers a perfect analogy for the current state of information security.2008-03-18 Is it time for Computer Access License Agreements?

Now that the US Federal Government is regularly seizing, coping and snooping into the computers of US Citizens returning home, what can we do to protect the privacy that we hold dear? The most obvious response is to encrypt your drives using whatever tools you deem appropriate. I had considered a "FiST US Customs" campaign, but I suppose that would not be very professional. I had also considered implementing some anti-forensic countermeasures on my computers. A simple change to one of the many open source disk wipers could fill your unallocated and slack space with billions of partial GIF images. That sure would make going through the preview in EnCASE a bit more tedious. And I suppose there are even more 'active' countermeasures available to those who are not squeamish about fighting back. After all, I have nothing to hide, and its not my job to make it easy for Law Enforcement to do theirs. Then it occurred to me as I was ranting to a fellow infosec practitioner. What we need is the equivalent of a EULA for our computers. Something that warns off would-be snoopers who decide to look at our computers without a warrant. I suppose putting one of these stickers on your computer and your hard drives is just asking for them to be confiscated, never to be seen again. But it sure would make a great story.
2008-03-14 DPS for life!
Distance makes the
heart grow fonder.
2008-01-24 Passive syslog monitor v1.2.1 (psmd) has been released
After many days of pushing hundreds of gigabytes of data through it, the new version of psmd offers many bug fixes and a new TCP reassembler which notes lost log data due to dropped packets. Along with the new features, psmd still offers many others:
- Passive syslog monitoring (no listening ports)
- Support for syslog over UDP and TCP (syslog-ng)
- Archiving of all log data with proper time stamps, source and dest MAC and IP address
- MD5 and SHA1 hashing of all archived logs
- Forwarding of syslog data with or without forged source IP addresses
- TIMEMARK insertion to handle time zone and time skew issues
2007-09-25 Sending a shout out to my com padre
Further continuing the South Park theme, I bring you yet another image of a fellow student of Sun Tsu and InfoSec practitioner. Can you guess who it is?

I just want to know one thing, where is my cut of the shirt action Tom?
2007-09-22 Regexless log parsing (quickparser)
A co-conspirator and I have been building some log analysis tools. To feed data to the tools, we needed to convert log files into a pseudo XML format. I built a couple of regex log parsers in perl but they were very slow. We have spent some time talking about other ways of parsing logs and I cannibalized a log compression tool that I had built using regexless parsing and found out that it is pretty fast. By fast I am talking 2.6M lines per minute on a single processor 2.5GHz PC running linux and 950K lines per minute on a SunBlade 2000 with 1GHz processors.
Check out my quickparser, it chews up syslog data from Netscreen firewalls. It should work properly with any syslog source that uses key/value pairs separated by a '='.
2007-08-17 "Better out than in, that's what I always say!" -Shrek
InfoSec is from
Pluto, NetOps is from Jupiter
As
the tenth largest body orbiting our sun, Pluto has in recent years been
center stage to heated discussion about what makes a planet.
Living on
Pluto as it spins around its eccentric orbit at a chilly 29 AU to a
really chilly 49 AU from our Sun would be quite a challenge.
It's cold
and lonely and most people don't even consider Pluto a planet including
the IAU which on August 24th, 2006 relegated Pluto to 'dwarf planet'
status. It is surprisingly similar to the life as an InfoSec
professional. They are center stage to heated discussions
about the
significance, priority and impact of information security on
organizations. Aside from government and financial circles,
InfoSec is
at best an ugly stepchild and at worst is the bastard child of an
adulterous relationship. To the rest of the world, information security
is the curse of 'due diligence and care' that is resisted, ignored and
hated with vim and vigor likened to paying taxes. In short,
information security is the group that tries to make organizations do
silly things that cost too much and delay projects for no good reason
because "security breaches only happen to the other guy, not us".
The fifth planet from our Sun, Jupiter, stacks up as the
largest body in our solar system at 2 ½ times more massive
that all the
other planets put together. Jupiter keeps showing up in the
press with
missions like Voyager, Cassini and Galileo. If that
was not enough of
a spotlight, consider the Shoemaker-Levy 9 Impacts in July of
1994.
Jupiter is big, bright and full of hydrogen. Everybody knows
what
Jupiter looks like and we thank Jupiter for its gravitational pull, we
all prefer to have things hit Jupiter instead of us. Network
operations, like Jupiter, gets lots of visibility, is generally large
in comparison to other operational bodies and is full of an amazingly
diverse class of gases. And we all know to make a bee-line to
NetOps
when we can't surf the Internet.
Putting aside the above analogies, there are some fundamental
differences between InfoSec and NetOps and over the years I have
struggled to understand those differences as a way to improve my
interactions with my family on Jupiter. At its most
fundamental level,
the difference between "network" people and "security" people is that
one is focused on ensuring that packets move and the other
isn't. I
will leave ascribing the correct labels to you, the reader.
This fundamental schism is surprisingly wide and deep. And,
we are talking astronomic units (AU) here, not Grand Canyon
distances.
Countless times, I have gone to my brothers and sisters on Jupiter
asking for help in reducing the 'attack surface' of a problem and time
and time again, I have received feedback and lumps. With each
tongue-lashing and stroke I have heard "We don't have time or
resources". For a long time, I assumed that part of my family
was just
lazy.
The Epiphany came to me last week, NetOps is from Jupiter, not
my home town over on Pluto. When I ask network operations to
install
an ACL or firewall, they resist. Not out of laziness but as
an
instinctive response built into the very fabric of each resident of
Jupiter. Asking to block traffic is like asking them to move
to Pluto,
which is far too small and cold. When I look at the problem,
I see it
through the eyes of a happy resident of Pluto where blocking traffic is
just a matter of simple changes to router and firewall
configurations.
Add in a little audit trail and some monitoring for giggles, and it is
a happy place for all. But when someone from Jupiter looks at
preventing packets from reaching their final destination, it is like
preventing a packet from reaching it's pre-ordained and rightful place
in the universe and the ramifications will topple everything.
Not to
mention making a mess in the holiest of places, the change control
archive.
So, consider this, the next time you endeavor to make the
journey from Pluto to Jupiter to request a packet filter, start the
conversation with "Every packet is sacred", and bring lots of photos of
home to reassure them that Pluto is not all bad, because a network
operator who turns up a firewall is actually a Plutonian on vacation in
a warmer climate.
Ron Dilley
:Plutonian
2007-07-31 Blatant C.a.S.E.
I am sorry Marcus, I just can't keep it to myself . . .